Free WiFi still poses risks despite improved security. Understanding these risks helps you take necessary precautions.
Despite the rise of HTTPS, public WiFi networks still pose some risks in 2024.
Unencrypted WiFi Networks
Most public WiFi networks are password-protected and encrypted. However, free WiFi without a password is unsecured, allowing anyone within range of the network to intercept your online activity.
Even on password-protected networks, risks include:
- Network owners can see visited websites, even with HTTPS.
- Traffic interception and decryption remains possible, depending on security.
WEP networks use shared passwords, enabling easy decryption. WPA/WPA2-PSK networks use individual keys derived from shared passwords, improving but not eliminating risks.
WPA2-PSK networks offer improved security with individual encryption keys.
WPA/WPA2-Enterprise networks generate unique per-client, per-session keys, preventing traffic decoding between users. Here, attackers would need to create fake hotspots to access data.
HTTPS vs HTTP Websites
Most websites use HTTPS, an encrypted connection that secures information between your device and web servers using TLS (Transport Layer Security).
HTTPS is an encrypted version of HTTP, which is the basic internet standard for accessing web pages, that:
- Prevents most third parties from viewing your website activity.
- Blocks insertion of malicious code into your web traffic.
HTTPS-enabled websites display a padlock in your browser’s address bar:

While HTTPS improves public WiFi safety, it doesn’t guarantee complete protection. Vulnerabilities remain to certain Man-in-the-Middle attacks, phishing, certificate authority issues, and SSL/TLS vulnerabilities.
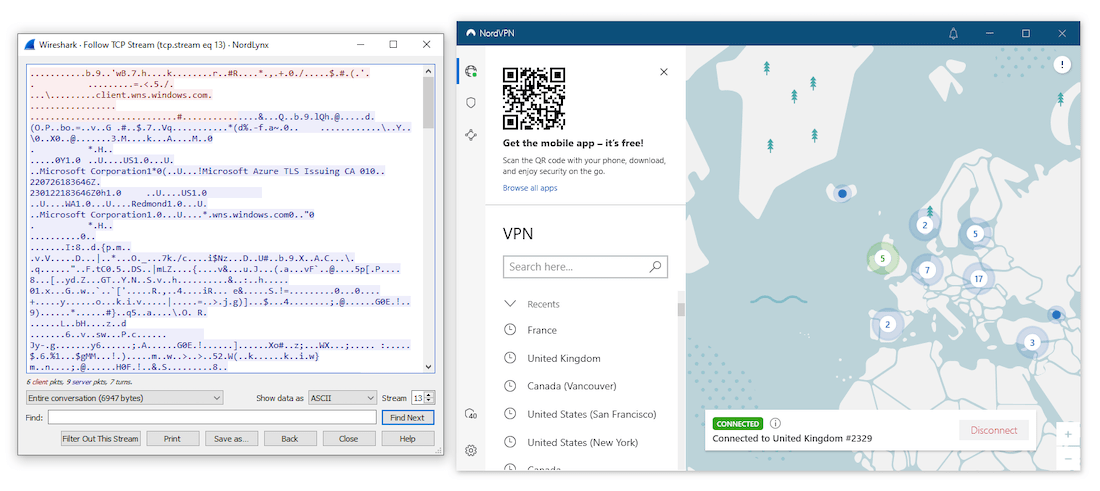
Importantly, HTTPS doesn’t protect DNS queries, which can be intercepted and manipulated. For comprehensive protection, we recommend using HTTPS in combination with a VPN.
EXPERT TIP: HTTPS ensures encrypted connections but doesn’t guarantee you’re on the intended website. Even with a padlock in the address bar, always verify you haven’t been redirected to a similar-looking domain.
HTTPS prevents WiFi providers from seeing individual pages visited, but domain names remain visible.
Most popular websites use HTTPS, but be cautious of those that don’t. Unencrypted (HTTP) traffic can be:
- Monitored by attackers
- Injected with malicious code
- Logged by WiFi providers
Some secure sites don’t default to HTTPS. 3 of the top 100 non-Google websites don’t. For these, use a VPN or browser extension to force HTTPS.
5% of Google’s visitors use outdated devices incompatible with modern encryption. If your device doesn’t support HTTPS, consider upgrading if possible.
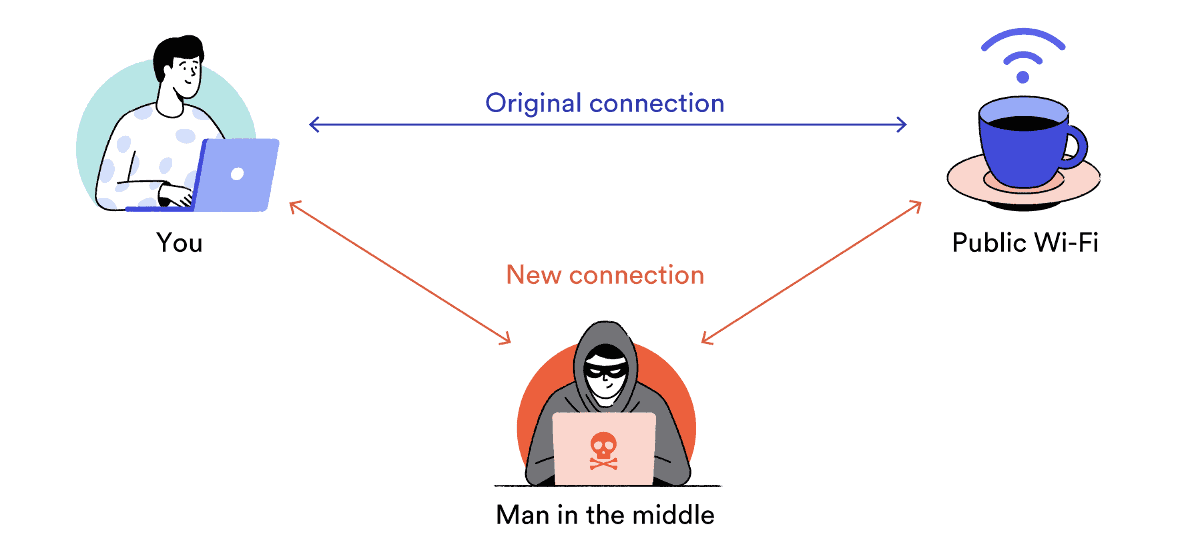
Man-in-the-Middle (MitM) Attacks
A Man-in-the-Middle (MitM) attack occurs when a malicious third party interrupts or alters the communication between two systems.
On public WiFi, MitM attacks target the connection between your computer and the web server.
Public WiFi increases MitM attack risk.
On unsecured networks, attackers can:
- Alter network traffic
- Redirect traffic
- Inject malicious content
Hackers can display fake websites, replace links, add images, and trick users into revealing personal information.
MitM attacks are popular because they’re cheap, easy, and effective. All a hacker needs is a device like the WiFi Pineapple, costing just $120.00.

The $120.00 WiFi Pineapple allows virtually anyone to exploit public networks to collect personal data.
These devices allow anyone to create fake WiFi access points for MitM attacks. They’re commercially available in computer hardware stores.
The WiFi Pineapple is a useful tool for researchers to test the security of WiFi networks but is very dangerous in the wrong hands. The device can:
- Interface with hundreds of devices simultaneously
- Gather sensitive data from public WiFi users
- Run SSLstrip software to convert HTTPS requests to insecure HTTP
Web servers can instruct modern browsers to use HTTPS, but this protection only activates on your second site visit.
Fake Hotspots & Evil Twin Attacks
Fake hotspots or ‘Evil Twin attacks’ are common public WiFi threats that steal data and infiltrate devices.
Attackers create networks with names like ‘Free_Cafe_WiFi’ or ‘FREE INTERNET’. Even a seven-year-old can set one up in 11 minutes.
WiFi Pineapples can scan for SSID signals, impersonating known WiFi networks and tricking devices into connecting automatically.
WiFi Pineapples can scan for the SSID signals used by device to find and connect to known WiFi networks, then impersonate them in order to trick devices into connecting automatically.
At the 2016 US Republican Convention, over 1,200 people connected to fake networks with names like ‘I Vote Republican! Free Internet’ that were set up by Avast in a stunt to demonstrate the dangers of free WiFi. 68% of users exposed their identities as a result.
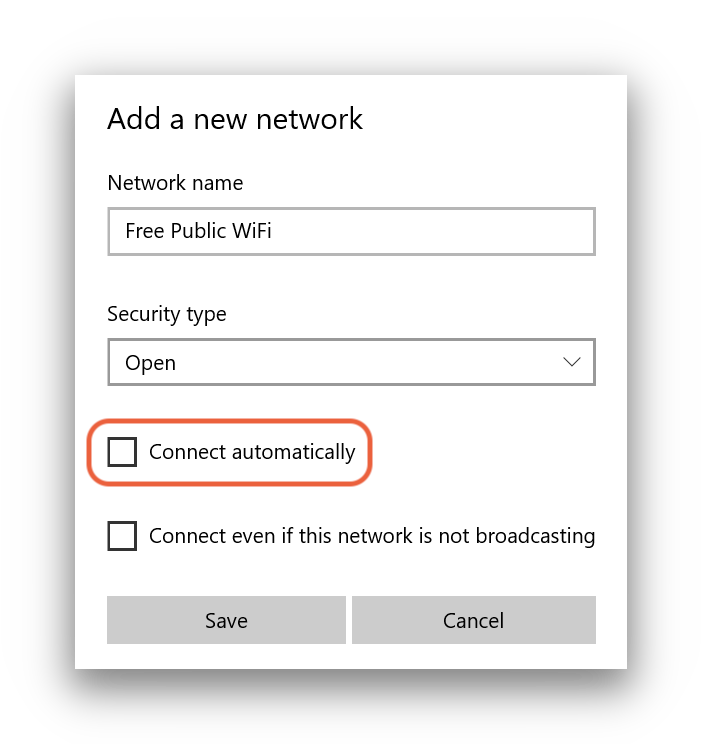
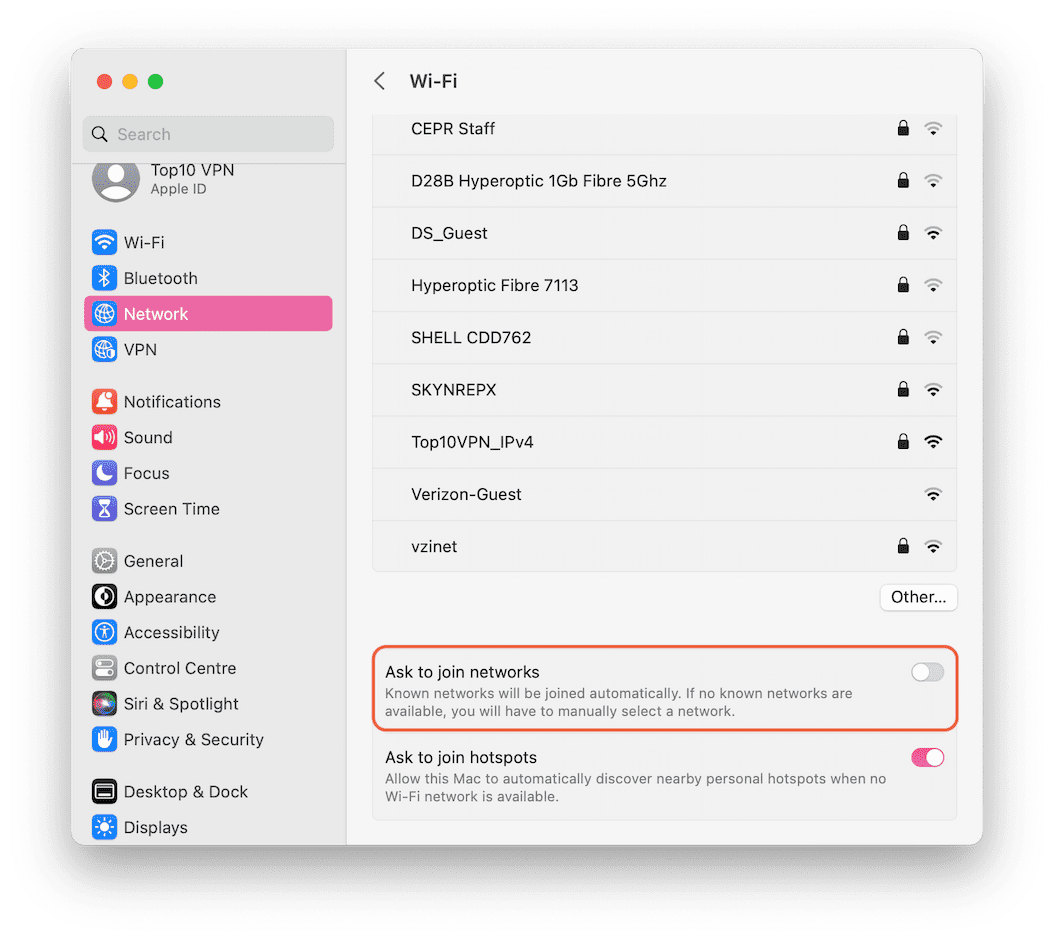
Be cautious of auto-connecting to networks, especially if the name or location seems suspicious.
DNS Spoofing
DNS Spoofing or ‘DNS cache poisoning’ is a MitM attack that diverts traffic from legitimate servers to fake ones, often exploiting unprotected public WiFi networks.
When you enter a URL, your device contacts a DNS nameserver to find the matching IP address.
DNS spoofing occurs when an attacker changes the entries in a nameserver’s resolver cache, redirecting users to a different IP address.
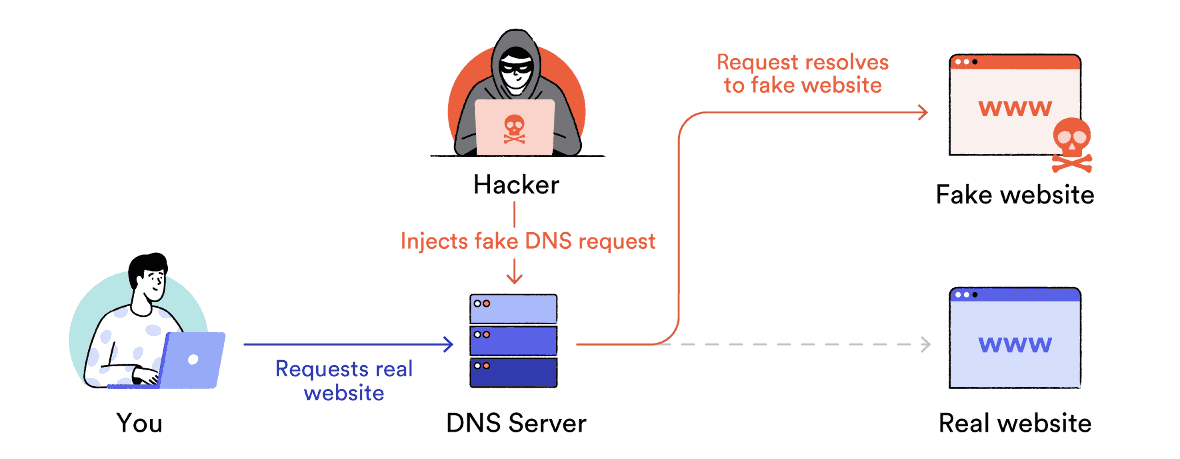
DNS Spoofing works by redirecting your traffic to fake servers.
This allows attackers to send users to phishing sites mimicking legitimate websites, designed to capture sensitive data like usernames and passwords.
Public WiFi hotspots can be vulnerable as they are often managed by small businesses lacking the technical knowledge to maintain adequate security measures, such as changing default passwords and updating firmware.
Hackers can exploit these weaknesses to install malware on routers, redirecting DNS queries to malicious servers, enabling them to divert traffic.
Session Hijacking
Session hijacking is another MitM attack that grants attackers full control of your online accounts. The risk has decreased with the widespread adoption of HTTPS.

Hackers can steal your identity through session hijacking.
‘Sessions’ are temporary states between communicating devices, such as your device and a web server, established using authentication protocols.
When logging onto a website, you’re assigned a session cookie containing details about your interaction with the web server. As you browse, the server requests this cookie for authentication.
Session hijacking copies these cookies to impersonate your device and steal your identity, targeting valuable cookies from secure websites like banking or shopping platforms.
On unsecured networks, attackers use ‘session sniffers’ to intercept session cookies. This software is easily accessible, despite being illegal for eavesdropping and data snooping.