Top10VPN is editorially independent. We may earn commissions if you buy a VPN via our links.
What Is a VPN (Virtual Private Network)?
Our Verdict
A Virtual Private Network (VPN) is a type of software that runs in the background while you’re using the Internet. It establishes an encrypted connection between your device and a remote server, hiding your physical location from the websites and applications you visit. This allows you to bypass geo-restrictions and other types of internet censorship, and it also prevents third parties from seeing your browsing activity or intercepting your data on hostile networks.

Summary: What Is a VPN and Why Do You Need One?
Use the Q&A sections below for a quick summary of what VPNs are, what they do, and what their limitations are.
What is a VPN?
VPN stands for Virtual Private Network. It’s a type of software that establishes secure and private connections over the internet (or any other type of public network).
There are lots of different types of VPN, but by far the most common are personal VPN services, which are applications that run in the background on your device.
Personal VPN services usually offer a network of different server locations to connect to. They’re used to bypass geo-restrictions and protect your privacy and security on the Internet.
Other common types of VPN include Remote Access VPNs and Site-to-Site VPNs, which are often used by businesses to securely access company files while working from home, or to create a combined network between two or more organizations in different physical locations.
How does a VPN work?
VPN software works by encrypting your web traffic and rerouting it through a remote server before reaching your desired website, service, or application.
All of the data transmitted between your device and the VPN server is encrypted. This ensures that your browsing activity and communications are indecipherable, even if your data transfers are intercepted.
It will also appear as though your connection is originating from the VPN server and not from your actual device. This hides your “true” IP address and location from the websites and applications you visit, who can only see the IP address of your chosen VPN server.
This can allow you to spoof your geographic location. For example, if you connect to a Japanese VPN server, it will seem to websites and applications that you are located in Japan.
What are VPNs used for?
A personal VPN service serves two main functions: encrypting your web traffic and hiding your IP address. This allows for a number of popular use-cases, including:
- Avoiding ISP surveillance and protecting your privacy online.
- Unblocking geo-restricted websites and streaming services.
- Bypassing local firewalls and evading government censorship.
- Avoiding ISP throttling and protecting P2P file-sharing activity.
- Staying secure on unprotected public WiFi networks.
Which devices can I use a VPN on?
Personal VPNs typically offer native applications and client software for:
- iPhone and Android phones
- Windows, macOS, and Linux computers
- Chrome and Firefox web browsers
- Apple TV, Google Chromecast, and Amazon Fire TV Stick devices
- WiFi routers
For streaming devices, including Roku, Smart TV, Xbox, or Playstation devices, you can install a VPN onto your WiFi router. This will protect every device that’s connected to your WiFi network.
It is also possible to set up your own VPN server at home using a router, personal computer or Cloud Computing Service.
While this is mostly free to do, it’s also technically difficult. You won’t be able to use it to flexibly spoof your geographic location, and it doesn’t protect your privacy from your ISP or anyone they share information with.
What are the drawbacks of using a VPN?
Using a VPN has limitations and disadvantages that are important to be aware of:
- Most good-quality VPN services charge a monthly subscription fee.
- All VPNs slow down your connection speeds to some degree.
- A VPN cannot make you completely anonymous online.
- Your safety depends on how trustworthy your VPN provider is.
- Using a VPN is illegal in a small number of countries.
- A VPN will not protect your device against most malware or cyberattacks.
- Using a VPN increases bandwidth consumption.
- Even the best VPN can’t unblock every website all of the time.
In the remainder of this article, we’ll take an in-depth look at everything you need to know about VPN technology and VPN services.
If you have a specific question about VPNs, feel free to email us or visit one of the following articles for a detailed answer:
Have a specific question about VPNs? You can find detailed answers in the articles below:
- How Do VPNs Work?
- What Are VPNs Used For?
- Which VPN Protocol Is Best?
- Are VPNs Legal?
- What Are VPN Logging Policies?
- VPN Leaks Explained
- How Do VPN Jurisdictions Affect You?
- Are Virtual Server Locations Safe?
- Do VPNs Use Mobile Data?
- How Much Does a VPN Cost?
- What Are the Disadvantages of VPNs?
- What Are the Different Types of VPN?
- What Does a VPN Hide?
- Are VPNs Really Worth It?
Why Trust Us?
We’re fully independent and have been reviewing VPNs since 2016. Our advice is based on our own testing results and is unaffected by financial incentives. Learn who we are and how we test VPNs.
| VPNs Tested | 62 |
| Total Hours of Testing | 30,000+ |
| Combined Years of Experience | 50+ |
Types of VPN Connection
There are different types of VPN depending on the type of connection a user requires.
Personal VPN services are designed for normal internet users who want to improve their privacy, security, and freedom online. For this reason, they are sometimes also called consumer VPNs.
By contrast, remote access VPNs, mobile VPNs, and site-to-site VPNs are all types of business VPN. They are designed for remote employees to gain secure access to internal resources.
Here is a quick overview of each type of VPN service and how they differ from one another:
Personal VPN Services
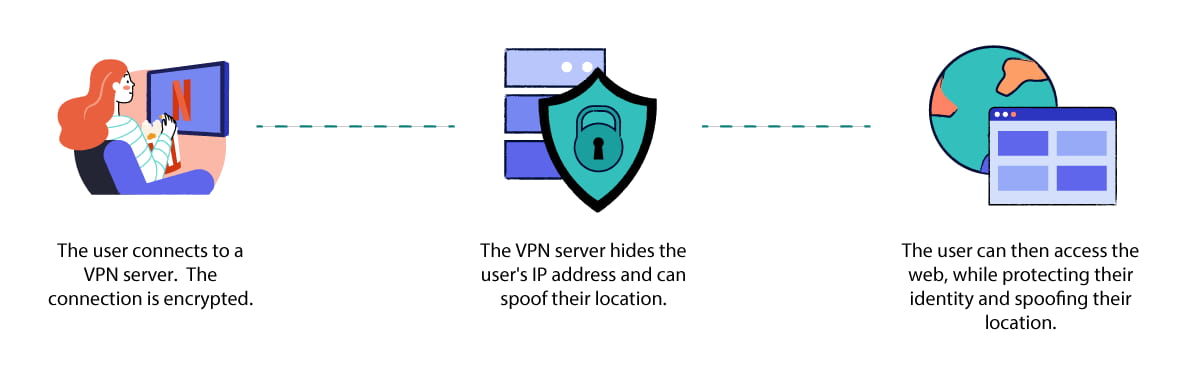
A personal VPN service hides your IP address and browsing history while you browse the internet in your free time.
A personal VPN service provides individual users with encrypted access to a remote VPN server that’s owned by the VPN provider.
It lets users create a secure connection to servers in a range of different locations, which they can then use to protect their identity, spoof their geographic location, and evade surveillance as they browse the internet.
Using Proton VPN, a personal VPN service, on an Android phone.
They can be used on most devices, including iOS and Android smartphones, macOS and Windows computers, and even installed directly onto your WiFi router at home.
Personal VPNs are the most common type of VPN service, and are also the type of VPN we focus on at Top10VPN.
Remote Access VPNs
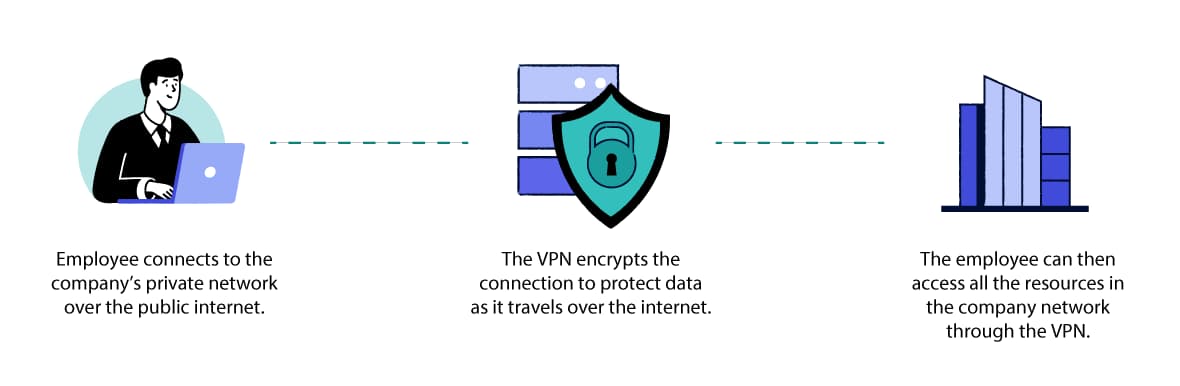
Companies use remote access VPNs to keep important information private.
Remote Access VPNs provide employees with encrypted access to a company’s internal network while working remotely. They are the most common type of business VPN.
Unlike personal VPN services, remote access VPNs aren’t designed for users looking to access online services and applications.
Instead, the purpose is to enable employees to access company resources, files, and applications securely regardless of their physical location, and to ensure that any company data transmitted is protected from unauthorized access or interception.
NOTE: Popular examples of remote access VPNs include Access Server by OpenVPN and Cisco AnyConnect.
Mobile VPNs
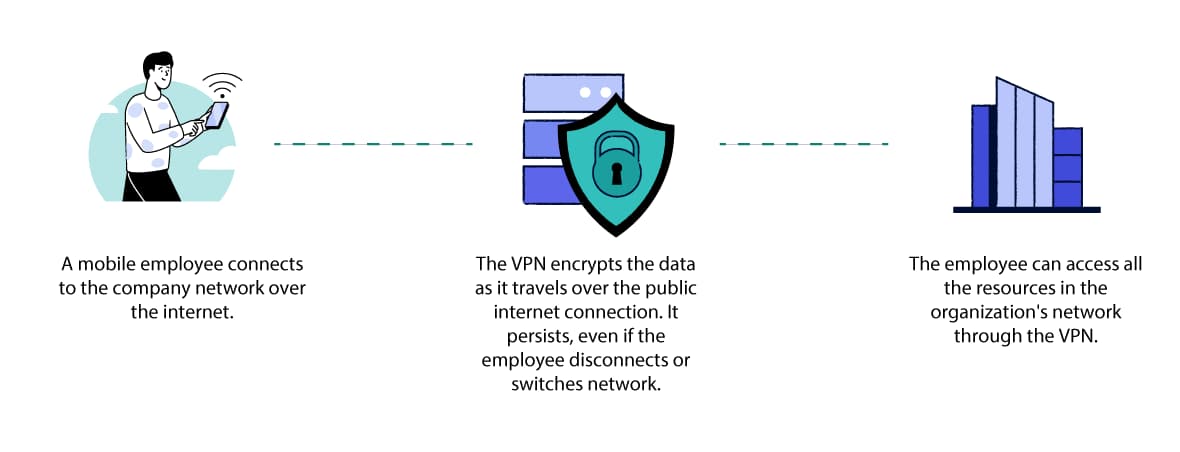
A mobile VPN connection persists even when there’s poor signal.
A mobile VPN is similar to a remote access VPN in that it safely connects remote employees to a company network.
However, while remote access VPNs are designed for users working from a static location, mobile VPNs are designed for users who are regularly switching between cellular and WiFi networks or whose connection is likely to drop from time to time.
A mobile VPN is designed to stay connected despite these interruptions and instability. They are therefore particularly useful for mobile workers, such as firefighters or police officers.
NOTE: Mobile VPNs are compatible with any device and any network connection. They are not only for smartphone users.
Site-to-Site VPNs
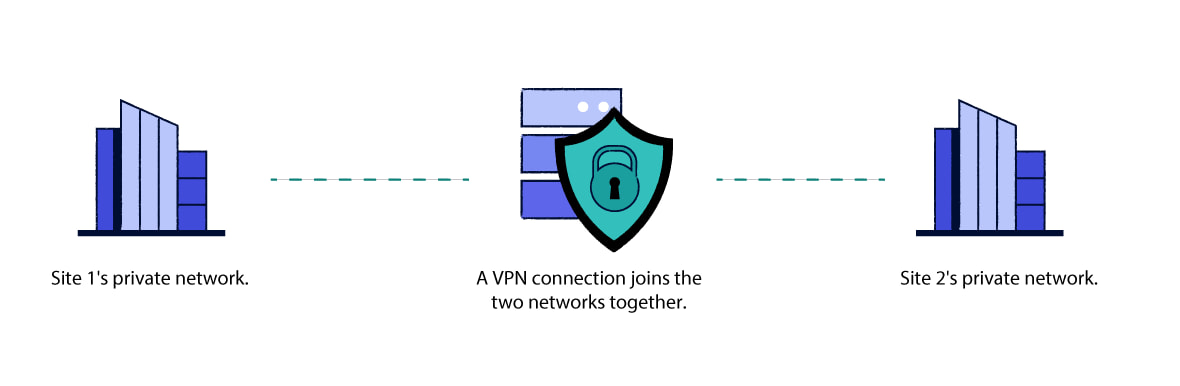
Companies might use site-to-site VPNs if they offices in different locations.
Site-to-site VPNs are used to securely expand a single company network to include multiple different premises or office spaces in different physical locations.
They differ from the other types of business VPN in that they are designed to connect two or more networks together, rather than connecting an individual employee to the office network.
NOTE: In the remainder of this article, we focus on personal VPN services. However, you can learn more about business VPNs by reading our dedicated guide to VPN types.
What Are the Benefits of a VPN Service?
There is a large amount of false or misleading information online regarding what a VPN can and cannot do, which can make it difficult to decide whether you actually need to use one or not.
A personal VPN has two primary benefits:
- It hides your IP address and geographic location from the websites, services and applications you use. Without this information, it’s much harder to link your online activity to your identity, which makes it more difficult to track, profile, or block you.
- It hides your activity from your ISP or network administrator. Encrypting your data transfers makes it almost impossible for your ISP, mobile carrier, WiFi administrator, or eavesdroppers on a public WiFi network to see which websites you’re visiting, the files you upload or download, or any personal details you enter into HTTP websites.
With these two basic functions, a VPN can be used for a number of different purposes related to improving your privacy, security and freedom online.
Here are the most popular reasons people give for using a VPN, from a survey we conducted in collaboration with GlobalWebIndex:
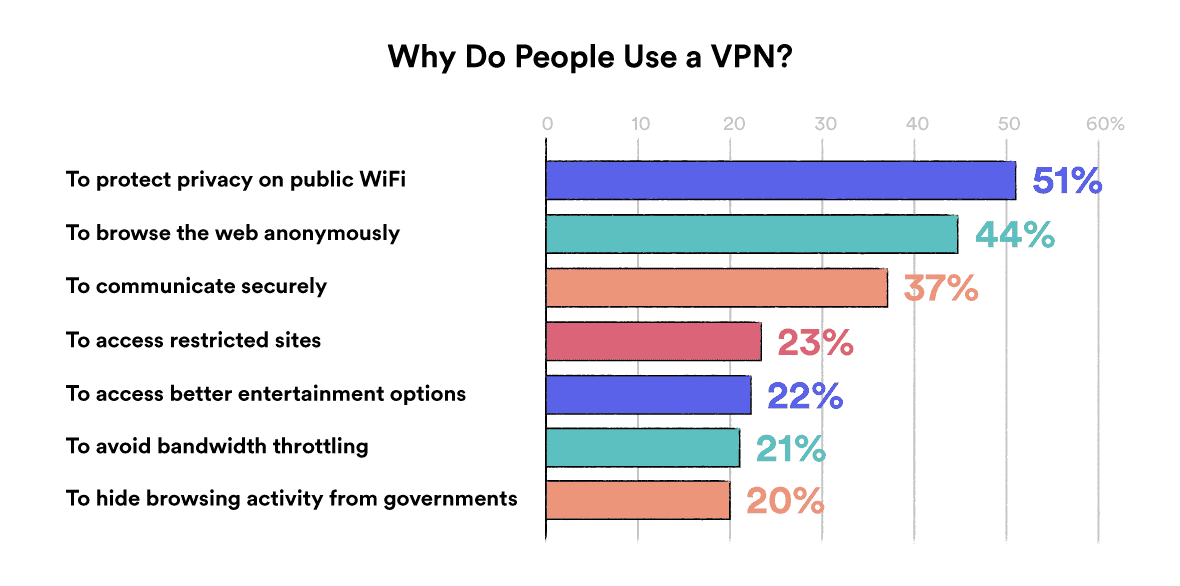
Data taken from the 2020 Global VPN Usage Report.
Here is a table summarizing everything you can and cannot do with a VPN:
| What you can do with a VPN | What you cannot do with a VPN |
|---|---|
| Protect yourself from traffic interception and Man-in-the-Middle attacks when using unsecured public WiFi networks. | Protect yourself from all forms of cyberattack, particularly those that trick you into downloading malware or disclosing personal information. |
| Spoof your location in order to unblock geo-restricted movies and TV shows, video games, or sport events that are not available in your geographic region. | Hide your physical location from websites and applications that use WiFi Location Tracking. Most VPNs can’t spoof your device’s GPS location data, either. |
| Make it harder for ISPs, advertisers, schools, employers, and government agencies to monitor and record your browsing activity. | A VPN will not stop a determined entity from tracking you via cookies, fingerprinting, or behavior profiling, for example. |
| Prevent your ISP from throttling your connection while streaming, gaming and torrenting. | Watch Netflix, HBO Max, or any other streaming service for free. |
| Access websites and material that’s censored by the government, or unblock websites at school and work. | Hide your browsing activity from employers and school WiFi admins that use screen monitoring software. |
| Bypass IP-based website bans. | Prevent your ISP from knowing your real IP address and location. |
| Avoid location-based price discrimination while shopping online. | Avoid price discrimination tactics that rely on tracking cookies or other forms of profiling based on browsing behavior. |
| Give remote employees reliable and secure access to sensitive files and resources on the company’s internal network. | Bypass email- or account-based website bans. |
| Hide how much data you are consuming from your ISP or cell phone carrier. A VPN will actually increase how much data you use. |
In the rest of this section, we cover in detail exactly what you can do with a VPN, while also addressing common misconceptions about what VPNs cannot do.
Alternatively, you can skip ahead to our dedicated section on whether you really need a VPN, or learn more about the technical aspects of how VPNs work.
1. Secure Your Web Traffic
By encrypting and securing your data transfers, a VPN protects you from criminals who exploit unprotected public WiFi hotspots in coffee shops, airports, or hotels.
You can use a VPN to help protect yourself against all of these cyberattacks:
- Eavesdropping: By intercepting and reading your web traffic, an attacker can see all of the information you disclose on unencrypted HTTP websites, including sensitive details such as credit card information, passwords and medical records.
- Man-in-the-middle attacks: By intercepting and manipulating your web traffic, attackers can divert you toward clones of a particular website to trick you into disclosing sensitive information like log-in credentials or bank details. This is known as DNS spoofing.
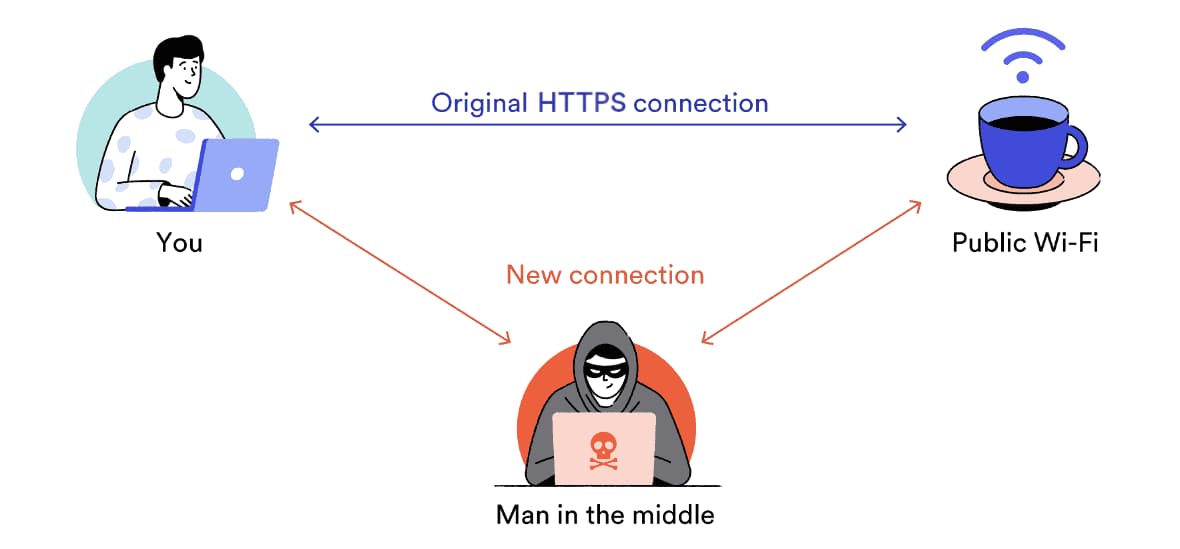
Attackers might also manipulate your web traffic by injecting malware that track or alter your internet activity, steal personal information stored on the device, or even lock you out of your own files and accounts entirely.
- Session Hijacking: Attackers can intercept your web traffic in order to steal the session cookie associated with your connection to an HTTP website.
Session cookies are the small text files that authenticate a user’s connection to a website or service during a logged-in session.
By stealing these session cookies, an attacker can continue using your account after you log off. This may allow them to make bank transfers from your account, send and receive messages on your behalf, or change your passwords.
VPN encryption assures that even if your connection is intercepted, your traffic will be illegible, an attacker will not be able to steal your session cookies, and they will not be able to see the destination of your original traffic request.
EXPERT ADVICE: Fortunately, the majority of websites and services use HTTPS encryption nowadays. This makes eavesdropping attacks far less common than they used to be. You can check whether you’re using an HTTPS website by looking for the padlock on the left-hand side of the browser’s address bar.
It is important to know that a VPN does not give you complete protection against cyberattacks on public WiFi networks. You can still be hacked, even when you use a VPN.
There are two reasons for this:
- Not all VPN protocols are secure, and not all VPN services support safe VPN protocols. Depending on your VPN provider, the protocol they use, and the way you have configured your VPN connection, it is still possible for cybercriminals to break your VPN’s encryption and expose your web traffic.
- VPNs do not offer protection against all forms of malware. A VPN will do nothing to prevent you from revealing confidential information or downloading spyware or viruses onto your device as a result of a phishing scam.
2. Unblock Geo-Restricted Content
When you connect to a VPN server, the websites and applications you use will see the IP address of the VPN server instead of your “true” IP address.
By connecting to a VPN server in a different country or region, you can use a VPN to spoof your location and unblock geographically-restricted websites from anywhere in the world.

We used a VPN to unblock geo-restricted content from other Netflix regions.
Some of the benefits of using a VPN to unblock geo-restricted content include:
- Accessing additional movies and TV shows on streaming platforms. Due to licensing regulations, many websites and services will change or limit the content they display based on the user’s IP address and physical location.
Streaming services like Netflix and Disney+, for example, show an entirely different catalog of movies and TV shows to users from different countries.
Using a VPN, you can ‘unlock’ the full range of streaming material available on these websites.
- Unblocking geographically-restricted content. Other platforms, such as BBC iPlayer or Hulu, are only accessible to users from a particular country. By connecting to a VPN server in that country, you can unblock these services and view their restricted content.
NOTE: Regional news websites can also block access to visitors from outside the local area, in order to prevent server congestion. You can use a VPN to unblock these sites in exactly the same way.
- Bypassing sports blackouts in order to stream local games. Broadcasting restrictions occasionally prohibit NBA and MLB games from being streamed in the local area.
You can use a VPN to change your IP address to outside of the local blackout zone, thereby re-gaining access to MLB.tv, NBA League Pass, and other blocked live streaming services.
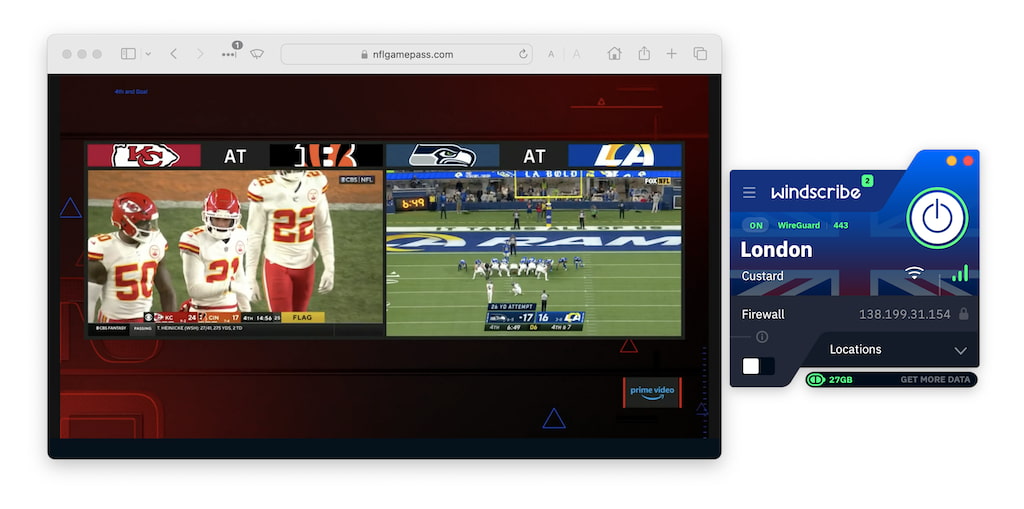
We watched out-of-market NFL games for free with Windscribe.
- Playing geo-restricted video games or finding easier gaming lobbies. You can use a VPN to access and play video games that are blocked in your location. For example, gamers in India can use a VPN to play PUBG Lite.
Another benefit of using a VPN for gaming is that it can help you avoid skill-based matchmaking (SBMM) algorithms on games like Call Of Duty.
These algorithms only apply in locations with a sufficiently large pool of players. By using a VPN to change your location to one with a smaller player base, you can often evade the SBMM algorithm and access easier gaming lobbies.
NOTE: On some eCommerce platforms, such as Steam, you can also use a VPN to access earlier release dates for certain video games and other products.
- Avoiding price discrimination while shopping. Car rental companies, airlines, and other eCommerce sites often use your IP address to inflate the prices you see based on your location. Using a VPN will let you spoof your location and thereby ‘unblock’ cheaper prices.
When it comes to unblocking geo-restricted content with a VPN, it’s important to note that no VPN service will work 100% of the time.
Streaming, gaming, and shopping websites are always trying to detect and block VPN connections, and there are inevitably times where they succeed. Premium VPN providers are always updating their pool of IP addresses to stay ahead of these blocks, but they still happen occasionally.
Your IP address isn’t the only way that websites can identify your location, either. Companies including Google, TikTok, Snapchat, Uber, and Tinder all use alternative sources of information, such as GPS, WiFi Location Tracking, HTML5, and DNS data, to get a more comprehensive view of your geographic location. Most VPNs will not hide your location from these websites.
3. Bypass Censorship & Surveillance
Using a VPN makes it much harder for websites, advertisers, big tech companies, governments, employers, and WiFi administrators to track and surveil your browsing activity.
Not only does this help to protect your privacy online, it also helps you to bypass website blocks at school and work or evade government-enforced censorship.
Here is a more in-depth look at each of these use-cases:
Evading censorship and mass surveillance
Governments in dozens of countries use tracking and profiling techniques to carry out mass surveillance of their citizens.
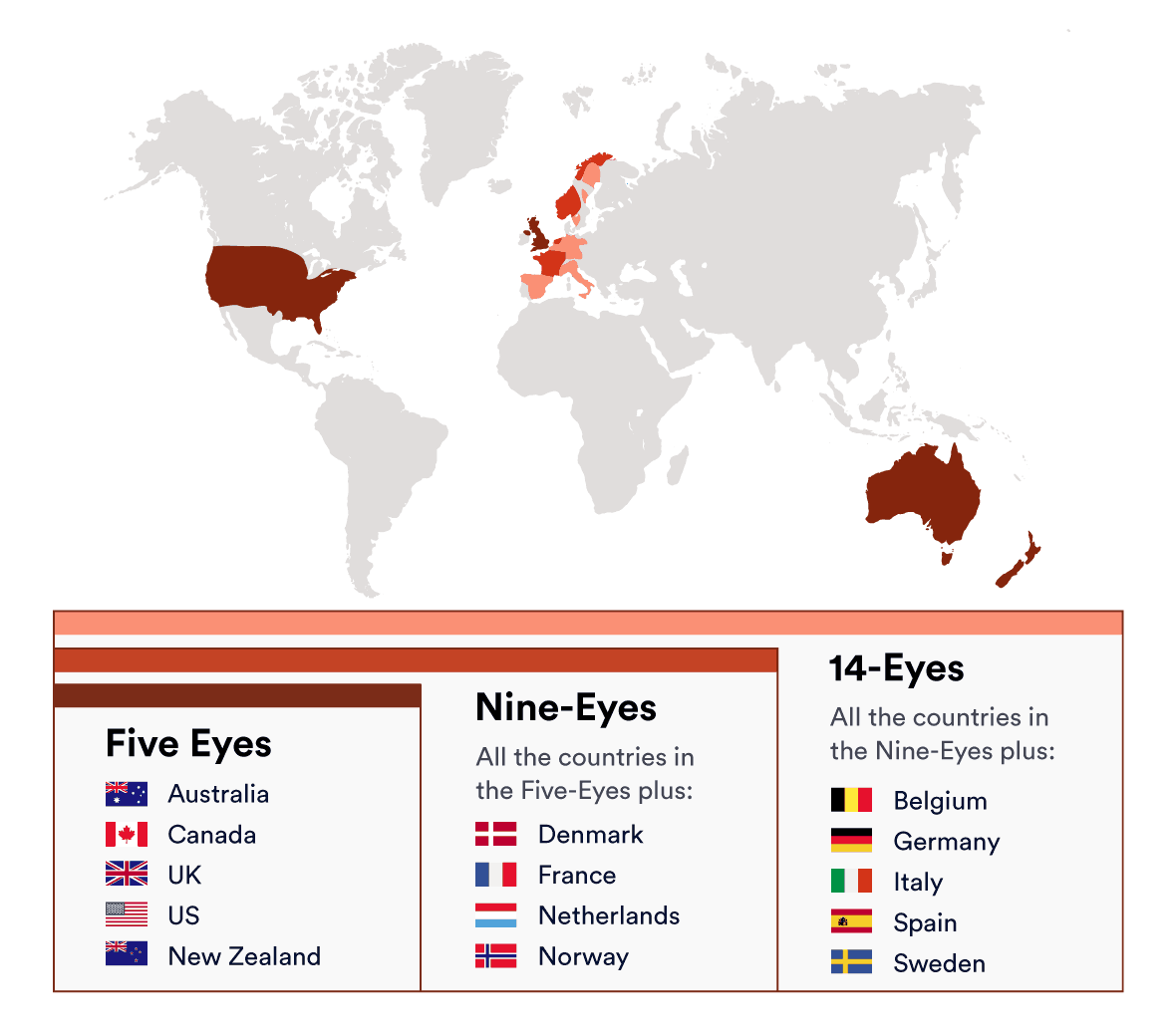
In some cases, the governments of these countries then combine their efforts to form global surveillance alliances. The strongest of these is known as the Five Eyes Alliance.
These surveillance measures are often accompanied by internet censorship regimes that use firewalls to block access to particular websites, resources, and information online.
Almost every country censors its citizens’ internet access to some degree. Examples of such internet censorship can include:
- Banning gambling or pornographic websites in the interest of public safety.
- Censoring particular social media posts, news publications, or blogging platforms in order to limit citizens’ access to information.
- Blocking communication tools and messaging applications, such as WhatsApp, Viber, and Skype in order to prevent protest and silence political opposition.
- Shutting off the internet entirely in order to maintain control during significant events.
Using a VPN can help you hide from government surveillance measures, and the best VPNs will even let you bypass some forms of state censorship.
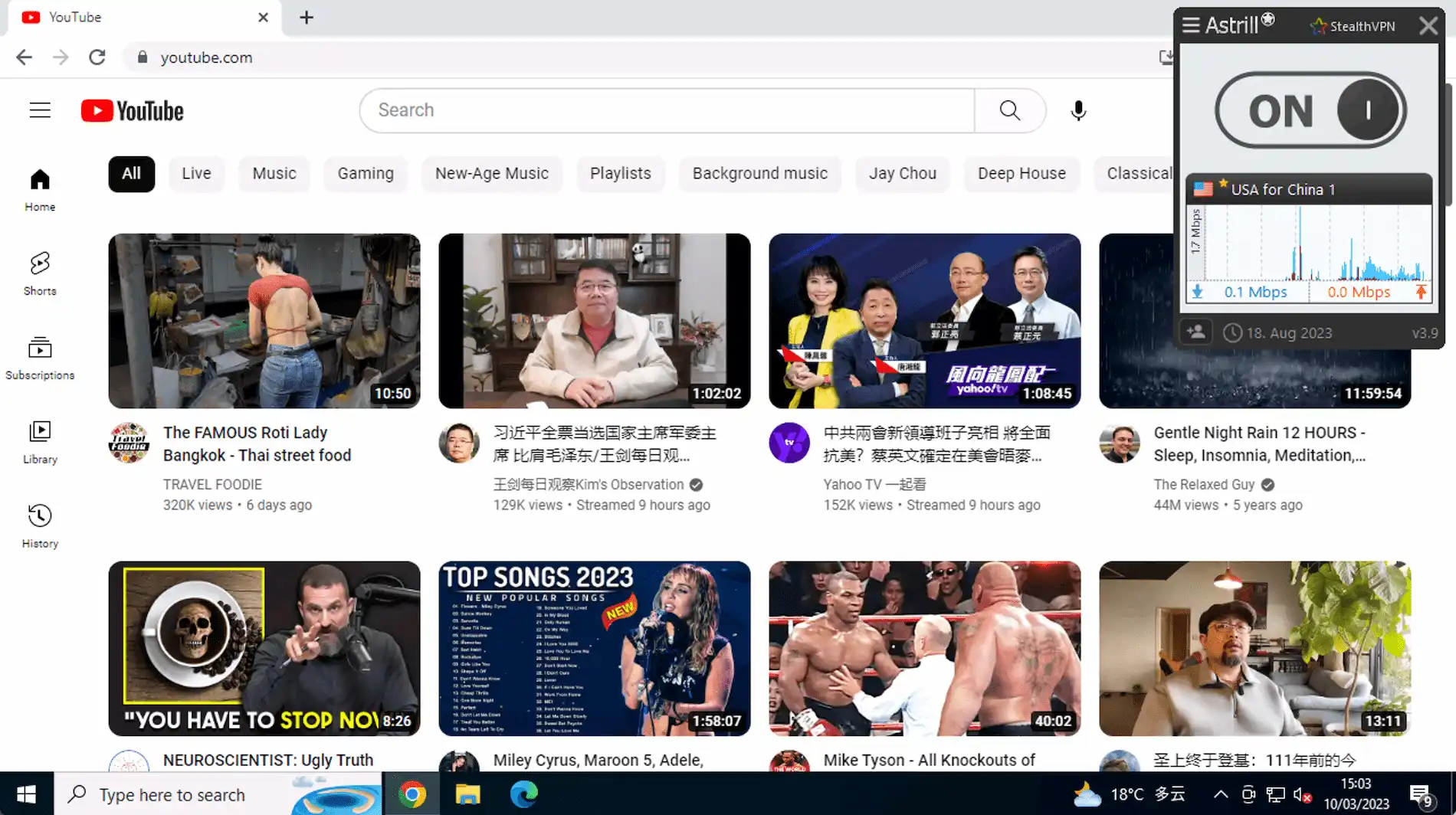
We used Astrill VPN to unblock YouTube in China.
They do this by encrypting the true destination of your traffic requests. This prevents your ISP from seeing the websites you visit, and allows you to avoid being detected by the firewall, thereby granting you access to the free and open internet.
It’s worth noting that using a VPN does not completely protect you from government surveillance. Authorities have the power to compel ISPs, the owners of the websites and applications you use, and sometimes even VPN providers themselves to record and share logs of your web browsing activity.
If they inspect your connection, government officials will also be able to see that you are using a VPN. This could get you into serious trouble if VPNs are illegal in your country. The only way to hide the fact you’re using a VPN is to use VPN obfuscation technology.
Unblocking websites at school and work
Schools, colleges, and workplaces regularly monitor the web activity of students and employees on the local network. They may even implement content blocks and censorship restrictions of their own.
Typically, these are related to productivity. For example, schools tend to block gaming websites and messaging services, while employers might block social media sites and video streaming platforms like YouTube.
Schools often impose restrictions on gaming websites.
You can use a VPN to access blocked websites and services at school and work. The VPN’s encryption hides the true destination of your web traffic, allowing you to bypass the network’s firewall.
Keep in mind that your employer or WiFi administrator will see that your web traffic is going to a VPN server, even if they can’t see where it goes after that.
They may also monitor what you’re doing online using pre-installed screen monitoring software or keyloggers, which a VPN won’t help with.
Avoiding advertising networks and IP-based bans
Your IP address and geographic location isn’t the only personal information that gets exposed to the websites and applications you use. They can also see details about:
- Your device, its operating system, and how it is configured.
- Your browsing activity on their site, including any files you download or upload.
- How often you visit the site and the specific timestamps of when you visited.
When all of this information is combined with your IP address and additional elements like cookies and tracking scripts, websites are able to form a comprehensive picture of who you are and what you like to do online. This is known as profiling.
These ‘profiles’ can then be used to target you with personalized advertising, increase prices for products you’ve previously shown an interest in, or even ban you from their website entirely.
Worse still, this information can be sold onto data brokers and advertising networks, who can combine it with ‘profiles’ from other websites to build up an even more holistic picture of you.
Using a VPN won’t hide your activity on these websites, but it will make it much harder for them to identify who you are. Your activity will be associated with the VPN server’s IP address, so it’s much more difficult to piece together your activity across a range of different websites and services.
4. Prevent ISP Tracking & Throttling
Your internet service provider (ISP) is the company that provides you with access to the internet.
Whether you’re connecting through your home WiFi router or via your phone’s mobile data network, all of the data that travels to and from your device has to be transmitted through the ISP’s network infrastructure in order for you to stay connected to the internet.
Your ISP can therefore see lots of details about your online activity, including:
- Which websites and applications you use
- Timestamps of when you access them and how long you spend there
- Any files you download or upload
- The specific web pages you visit, videos you watch, and information you enter on these sites, if they are not HTTPS-encrypted
- Details about the device(s) you use, such as screen resolution, operating system information, and MAC address
- Your IP address and geographic location
In many countries, including the UK, the US, Australia, and most of the EU, ISPs are legally obligated to record this information and retain logs of its users’ activity for an extended period of time.
These logs can then be:
- Shared with law enforcement agencies
- Used for commercial gain
- Stolen by cybercriminals
Your ISP can also use their tracking capabilities to actively reduce your connection speeds during periods of high demand or if you’re engaged in high-bandwidth activities, such as streaming, torrenting or gaming. This is a practice known as ISP throttling.
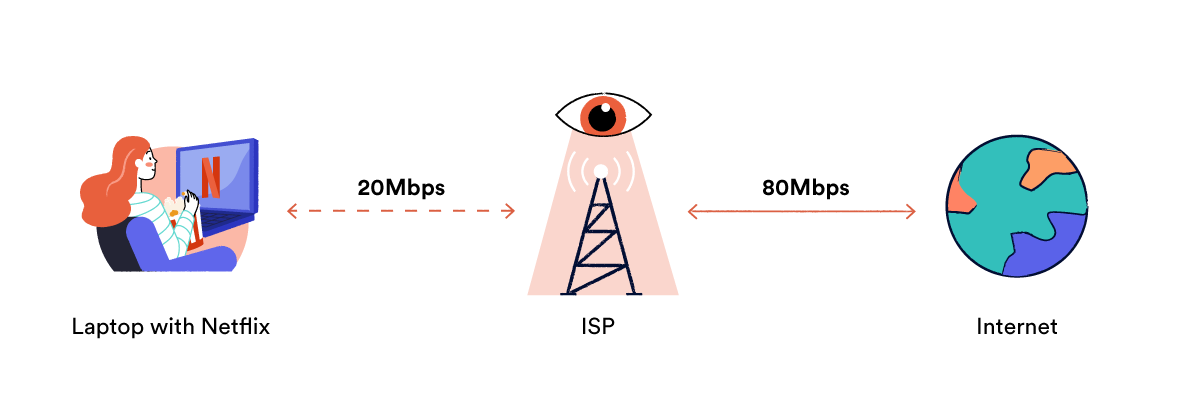
Internet throttling reduces the speed of your connection and your available bandwidth.
Using a VPN can prevent ISP tracking and limit ISP throttling. The VPN’s encryption transforms all of your browsing data into an unreadable string of letters and numbers. Your ISP will be unable to see the websites you’re visiting, and therefore unable to throttle your speeds based on your activity.
This encryption won’t stop your ISP from keeping logs of your online activity, but it will make these logs effectively useless for advertising, surveillance, and even criminal purposes.
Though this won’t prevent all types of ISP throttling, it can stop certain automated measures from being triggered, thereby offering a smoother gaming, streaming or torrenting experience.
EXPERT ADVICE: Using a VPN will hide the websites you visit from your ISP, employer, or school. However, specific web pages, searches, and videos are almost always already hidden by HTTPS encryption. You therefore don’t need a VPN to protect your privacy in this way.
Using a VPN will not hide your overall data usage from your ISP or mobile carrier. Since the data still needs to pass through their network infrastructure, they can still see how much bandwidth you are using, even if they can’t decipher exactly what you are doing with it.
Your ISP will also know that you’re using a VPN, because it needs to know the VPN server’s IP address in order to send your traffic there. This means that the government, police, and anyone else your ISP shares information with also knows that you’re using a VPN.
What Are the Limitations of VPN Services?
VPN services are not without their limitations or drawbacks. Indeed, the biggest threat to the most VPN users comes from believing that using a VPN makes them invincible online. This is simply not the case.
Here are some of the most common misconceptions about VPN services:
- Using a VPN does not make you completely anonymous online. There are a number of different identification and tracking techniques that a VPN will not protect you from. A VPN is just one layer of protection, and should not be seen as a catch-all solution.
- A VPN does not let you watch streaming services for free. A VPN lets you access geo-restricted videos, but you still need a valid subscription in order to access the streaming service.
- VPN services do not have servers in every single country or region. Before you purchase a subscription, you should check whether your chosen provider has a VPN server in the location you require.
- A VPN will not let you purchase video games at discounted prices or before their scheduled release dates. On Playstation, this is not possible without creating a new PSN account. On Xbox, it is possible, but you do not need a VPN to do it.
- Using a VPN does not provide complete protection from price discrimination. Websites may also use cookies and other tracking measures to register your location and interest in a product, and then increase the price accordingly.
As we have already seen, even the best VPNs cannot provide total anonymity online, nor complete protection from malware and cyberattacks. These are common misconceptions that lull users into a dangerous false sense of security.
Worse still, some VPN services are actually more dangerous to use than browsing without a VPN. That’s because you are placing your privacy and security entirely in the hands of your VPN provider.
In this section, we outline some of the main limitations and dangers of using a VPN. You can read our complete guide on the disadvantages of using a VPN for a more in-depth analysis, or skip ahead to find out how VPN software actually works.
Centralization of Risk
When you use a VPN, the VPN company is the only entity that can see both who you are and what you’re doing as you browse the web.
This places an extraordinary amount of trust in the VPN provider. You’re trusting them with access to:
- Your name and contact details (e.g., email address)
- Your payment information
- Your IP address and geographic location
- Your browsing activity, including:
- Which websites and apps you use,
- When you accessed them and how long for,
- any files you download or upload,
- the specific contents of any HTTP traffic (e.g. passwords and messages)
Premium VPN services completely ignore this information, and the best VPNs even put explicit measures in place, such as diskless servers, to prevent them from accessing it.
However, there are untrustworthy VPN providers that monitor and log your information in order to sell it to advertising networks and cybercriminals.
Even when they’re not being actively sold, these VPN logs still put you at an increased risk of cyberattacks and identity theft.
NOTE: Some VPN providers have also been known to inject adverts or malware into user sessions themselves, and to include backdoors in their products that allow law enforcement agencies to spy on their users’ activity in real-time.
The VPN provider is your greatest vulnerability when you use a VPN.
If the VPN company is run by someone malicious or incompetent, then your identity, browsing activity, and sensitive information is actually more exposed than it would have been if you’d connected to the web without a VPN.
Big Tech Profiling
By hiding your IP address and spoofing your location, a VPN makes it much harder for the websites and services you use to trace your activity back to you. But it does not make it impossible.
Big tech companies such as Google, Meta, and Amazon have a number of techniques they can use to identify you, many of which a VPN won’t protect you from.
The simplest of these is your personal account or profile. If you’re logged into your Google or Facebook account, it is extremely easy to trace your activity back to you and your account. It makes no difference that you’re using a VPN to hide your IP address while you browse.
Even if you’re not signed into an account, these companies have enough money and resources that, if you use their products regularly enough, it is likely that they could identify you via other means fairly easily.
Using a VPN is a hindrance to this type of big tech profiling, but it cannot prevent it on its own.
Even if you used a VPN over the Tor network, without logging into any accounts, on a device without GPS, it is almost impossible to stay completely hidden from these companies without making huge changes to the way you browse and the online services you use.
Cookies & Profiling
Advertisers, ISPs, and governments still have the means to track and profile you, even when you use a VPN.
While these entities don’t have the luxury of tracking your account activity, there are still a number of other techniques and methods available to them. These include:
- Cookies & Tracking Scripts: These are small files used by websites and applications to identify you across browsing sessions. They are stored in your web browser and contain information such as your name, location, and browsing preferences, thereby enabling websites to recognise you without using your IP address.
- Device & Browser Fingerprinting: Every time you connect to a website or online service, you reveal pieces of information about your device, browser, and operating system. This can include the type of device you’re using, its screen resolution and brightness, your browser settings, and any extensions you have. Collectively, these details form a distinctive ‘fingerprint’ that is unique to you.
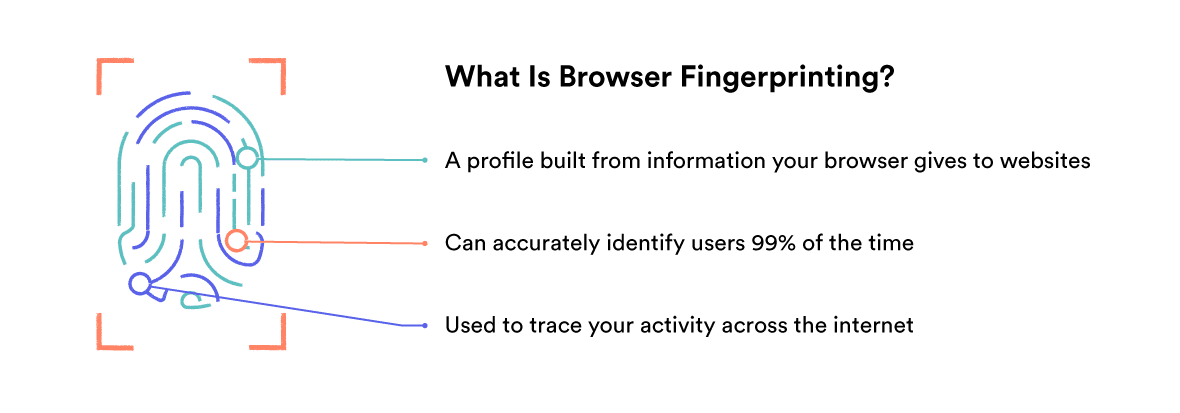
Using a VPN is not a guarantee of anonymity online. There are still many ways for authorities, ISPs, advertisers, tech companies, websites and even cybercriminals to identify, track and profile you, even with a VPN.
If online privacy is your goal, you should supplement your VPN use by:
- Turning off JavaScript
- Blocking third-party cookies
- Using Ad and Tracker Blockers (e.g. EFF’s Privacy Badger)
- Using Incognito/Private Browser or deleting tracking cookies after each session.
Malware & Cyberattacks
VPN encryption helps to prevent malicious actors from seeing or manipulating your web traffic.
However, there are many other ways for malware to infect your device, and a VPN cannot protect you against all of them.
Most notably, a VPN cannot protect you from social engineering attacks that convince you to click on a link or download a file that contains malware. It won’t stop you from replying to phishing emails or SMS messages with sensitive information, either.
Slower Connection Speeds
When you use a VPN, your traffic takes a longer route to your desired website or application.
This inevitably increases the amount of time it takes for your data to reach its endpoint, and therefore slows down the speed of your connection.
According to our tests, even the very fastest VPN services reduce your connection speeds by between 4% and 6%. This can rise even further if you use a poorly-configured VPN service or connect to a highly-congested VPN server.
For some, this will be an acceptable trade-off for the added benefits of using a VPN. But for others, the increased load times, video buffering, and reduced image quality may not be worth it.
Safety Risks (Logging, Leaks, Jurisdictions)
VPNs are not safe by default. As we have already seen, a VPN is only as safe as the VPN company is trustworthy. If the company decides to keep logs of your activity, or is compelled to do so by law, then the VPN is essentially worthless from a privacy and security perspective.
To avoid these risks, you need a VPN with an independently-verified zero-logs policy. It is also worth checking the jurisdiction of the VPN company itself. This tells you a lot about how likely it is to be instructed by its government to keep logs of your activity.
You also need a VPN that’s run by a competent company. If your VPN service uses weak encryption protocols or is poorly configured, there is a high chance it could leak your true IP address or otherwise fail to secure your web traffic.
How Does a VPN Work?
A VPN works by establishing an encrypted connection between your device and a remote VPN server. This secure connection is known as the VPN tunnel.
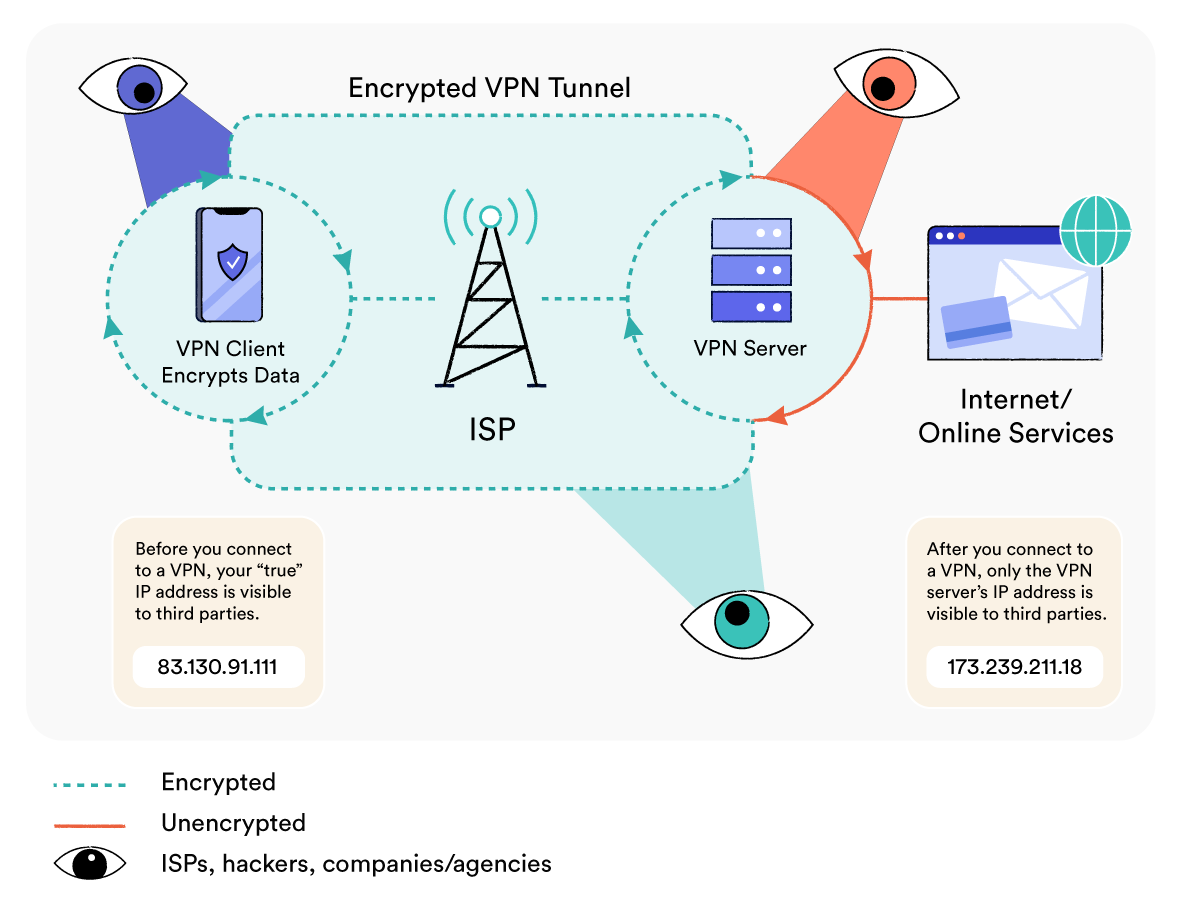
Once connected, all of the data leaving your device is routed through the VPN tunnel to the VPN server. The VPN server then forwards it on to the website you’re visiting, application you’re using, or company network you’re accessing remotely.
Data from the website or application then travels back to your device along the same route. It is first sent to the VPN server, which then transfers it through the VPN tunnel to your device.
There are five key stages to this process:
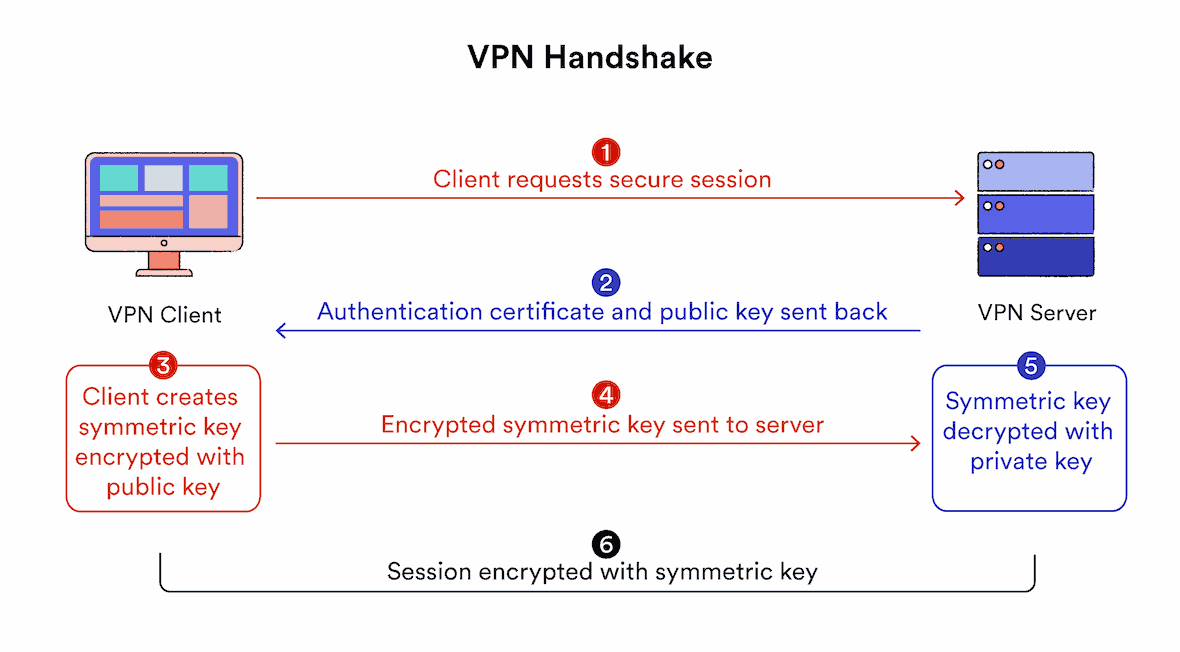
1. Handshake & Authentication
The VPN software on your device and the VPN server first authenticate themselves to each other. This is known as the VPN handshake.
During the handshake, the VPN client initiates a connection to the VPN server, indicating the intention to establish a secure tunnel. The two computers then verify their identities to each other using a password, digital certificate, or another authentication method.
Once authentication is complete, this connection is then used to securely share an encryption ‘key’ between client and server. This key is what is used to encrypt and decrypt the data at either end of the VPN tunnel for your entire browsing session.
EXPERT ADVICE: For the fastest and most secure VPN handshakes, look out for VPN services that use the RSA-2048 or RSA-4096 algorithm (not RSA-1024). For extra protection, we also recommend using VPN protocols that are set up with Perfect Forward Secrecy.
2. Encryption
With the connection to the VPN server established, the VPN client on your device then uses the agreed-upon ‘key’ and an encryption cipher to encrypt all of your internet activity.
In simple terms, this means that all of the plaintext data associated with your web traffic requests will be converted into strings of letters and numbers that are only intelligible to someone with the decryption key.
Web traffic before and after connecting to a VPN with AES-256 encryption.
3. Encapsulation
Your encrypted traffic is then wrapped in an additional layer of unencrypted traffic, which contains information about how to route it to the VPN server. This process is known as encapsulation, and is performed by dedicated VPN tunneling protocols.
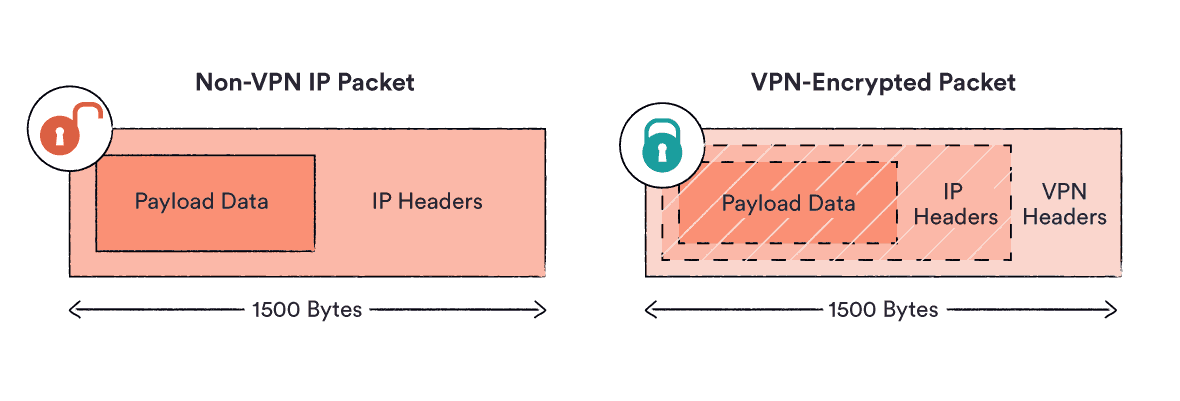
This is like taking an envelope with a written letter inside, and putting it inside a second envelope with a new address on. Your actual message becomes completely hidden from the outside world.
Your VPN client then hands the encapsulated traffic over to your ISP, which sends it to the VPN server. Due to the encryption, the only thing the ISP can see is the VPN server’s IP address.
4. Decryption, Forwarding, and Re-Encryption
Upon reaching the VPN server, this layer of encapsulation is removed, and the original data is decrypted using the encryption key.
This is like opening the outer layer of the letter to reveal the original message inside – thereby giving the VPN server access to the true destination of your connection request.
The server can then forward your request onto the website, service or application you require.
When the web server sends your request information back to you, it sends it to the VPN server where it is encrypted again and sent back through the VPN tunnel until it reaches your device.
The VPN client software on your device then decrypts the data, so that it can appear legibly on your screen.
5. Hash Authentication
As a final precaution, the VPN service also uses Secure Hash Algorithms (SHA) to authenticate the integrity of transmitted data and client-server connections. These ensure that no information has been altered in transit between source and destination.
If the alternative message the client generates differs from the alternative message the server generated, it means the message has been tampered with and so the data is rejected. If they are the same, it is accepted.
NOTE: SHA hash authentication is crucial for preventing man-in-the-middle attacks.
VPN Protocols & Encryption Ciphers
This process can involve different protocols and encryption ciphers, depending on the VPN service you’re using and how it’s configured.
The VPN protocol determines how the VPN tunnel is formed, while the encryption cipher is used to encrypt the data that flows through that tunnel.
Depending on the protocol in use, a VPN may have different speeds, capabilities, and vulnerabilities. Most services will let you choose which protocol you’d like to use within the app settings.
Here’s a quick overview of the most common VPN protocols:
- OpenVPN: Open-source, secure, and compatible with almost all VPN-capable devices.
- WireGuard: Very fast, safe, and data-efficient.
- IKEv2/IPsec: Excellent for mobile VPN users, but may be compromised by the NSA.
- SoftEther: Great for bypassing censorship, but not supported by many VPN services.
- L2TP/IPsec: A slower protocol that is also suspected of being hacked by the NSA.
- SSTP: Deals with firewalls well, but may be vulnerable to man-in-the-middle attacks.
- PPTP: Outdated, insecure, and should be avoided.
The encryption cipher is the algorithm (i.e. a set of rules) used to encrypt and decrypt data.
Ciphers are usually paired with a specific key-length. Generally, the longer the key length, the more secure the encryption is. For example, AES-256 is considered more secure than AES-128. Where possible, we recommend using a VPN with AES or ChaCha20 encryption.
To learn more about the specific VPN protocols and encryption ciphers that VPN services use, read our guides explaining how VPNs work and which VPN protocols are best.
Alternatively, you can keep reading to learn more about who really needs a VPN, or skip ahead to find out how to find a safe VPN service to use.
Do You Really Need a VPN?
A premium VPN service can cost anywhere between $2 and $13 per month when you sign up for a long-term contract — and even more if you subscribe for one-month subscription.
It’s likely to slow down your connection speeds, and it may attract some unwanted attention from your school, employer, or government. Depending on where you live, it can even get you into legal trouble. It’s therefore worth asking whether you really do need a VPN.
Ultimately, every internet user has to make their own decision as to whether a VPN is a worthwhile investment based on their budget, location, browsing habits, device(s), and more.
Here are our general recommendations for who should who should not be using a VPN:
You should use a VPN if:
- You regularly connect to public WiFi hotspots. The most common reason to use a VPN is to protect yourself from cyberattacks on public WiFi and other shared networks. While these networks are far less risky than they used to be, you are still putting yourself in danger of certain eavesdropping and man-in-the-middle attacks when you connect to one.
- You want to stream geo-restricted movies and TV shows from abroad. A VPN is by far the most effective way to unblock geo-restricted streaming content on platforms like Netflix, HBO Max, and BBC iPlayer.
If you frequently use streaming services while traveling or simply want to access ‘hidden’ movies and TV shows from home, then we definitely recommend using a VPN. - You don’t want your ISP tracking, logging, and profiting from your web activity. ISP tracking is an inevitable part of using the internet. You need an ISP to connect to the internet and, in many countries, there is little to dissuade them from recording or selling the details of your online activity.
A VPN is the most practical tool you can use to help stop this from happening on an everyday basis, but it won’t completely protect you from ISP surveillance.
You should consider using a VPN if:
- You are trying to bypass strict government censorship restrictions or evade mass surveillance. The best VPNs will bypass website blocks and access censored information in countries like China and Russia. Most VPN services will also give you some level of protection from both state and global surveillance measures.
A VPN is a useful tool to have as a visitor or citizen in one of these countries. However, governments can always use other methods to surveil you, and will sometimes even compel VPN providers to hand over logs of your activity.
We recommend using a VPN as a first measure, but you may also want to consider other tools such as the Tor Browser. - You are interested in improving your gaming experience. Using a VPN can let you play games that are blocked in your location or restricted on your local network. It may also help you access easier gaming lobbies, avoid ISP throttling, and protect you from Denial of Service (DoS) attacks.
If these benefits sound appealing to you, then consider using a VPN. Be aware that most games consoles don’t support native VPN applications, though. You will need to purchase a router VPN, instead.
For many gamers, however, using a VPN is not necessary. It will not quicken your connection speeds, reduce lag, or protect you from Distributed Denial of Service (DDoS) attacks.
You should not use a VPN if:
- You are looking for complete protection from malware, phishing attacks, and identity fraud. A VPN is not the same thing as antivirus software. It does not stop you from downloading viruses, spyware, and other forms of malware onto your device if you click a malicious hyperlink or email attachment.
It won’t prevent you from revealing personal information to scammers as part of a phishing attack, either, which could leave you susceptible to doxxing, hacking, or identity theft.
This is simply not what a VPN is designed for, so we do not recommend using a VPN for this reason.
Should You Use a VPN at Home?
VPNs work just as well on your home WiFi network as they do on public WiFi and on school, college, or work networks.
However, unlike with these shared networks, there is very little risk that your home WiFi has been replaced with a malicious ‘fake hotspot’, or that cybercriminals are eavesdropping on your connection.
Your home network is unlikely to block you from accessing certain websites and services. Nor should the WiFi administrator be monitoring and recording your activity, as they do in schools or workplaces.
Using a VPN at home is therefore not always necessary. For some users, it might simply slow your connection speeds down for no obvious benefit.
That said, a home VPN can still be worthwhile if you want to:
- Prevent your ISP from monitoring, recording and sharing your web browsing activity.
- Stop your ISP from throttling your connection speeds for high-bandwidth activity.
- Spoof your location in order to unblock geo-restricted websites and content.
- Evade IP-based site bans that have targeted your home WiFi IP address.
- Bypass state-imposed censorship regimes and browse the internet freely.
- Make it harder for governments to surveil you and for big tech companies to track you.
- Securely access company files and software while working from home.
- Protect yourself from cyberattacks by other users on the network (if your home WiFi is a residential network shared by other users).
Should You Use a VPN on Your Phone?
Given how much private and sensitive information is stored and shared on our phones, it is arguably more important to use a VPN on your phone than on a laptop or desktop computer.
We also tend to connect to a larger array of public WiFi networks when using our phones, which increases the risk of encountering unsecured, weak, or even fake hotspots.
We therefore recommend using a VPN on your phone if you regularly travel and connect to public WiFi hotspots in airports, hotels, cafes.
It is also worth noting that cell phone carriers, such as Verizon Wireless, are ISPs in their own right. In many countries, this means they are compelled to track and keep logs of your web browsing activity and app usage while your device is connected to cellular data (e.g., 3G, 4G, 5G). VPN encryption makes these logs indecipherable.
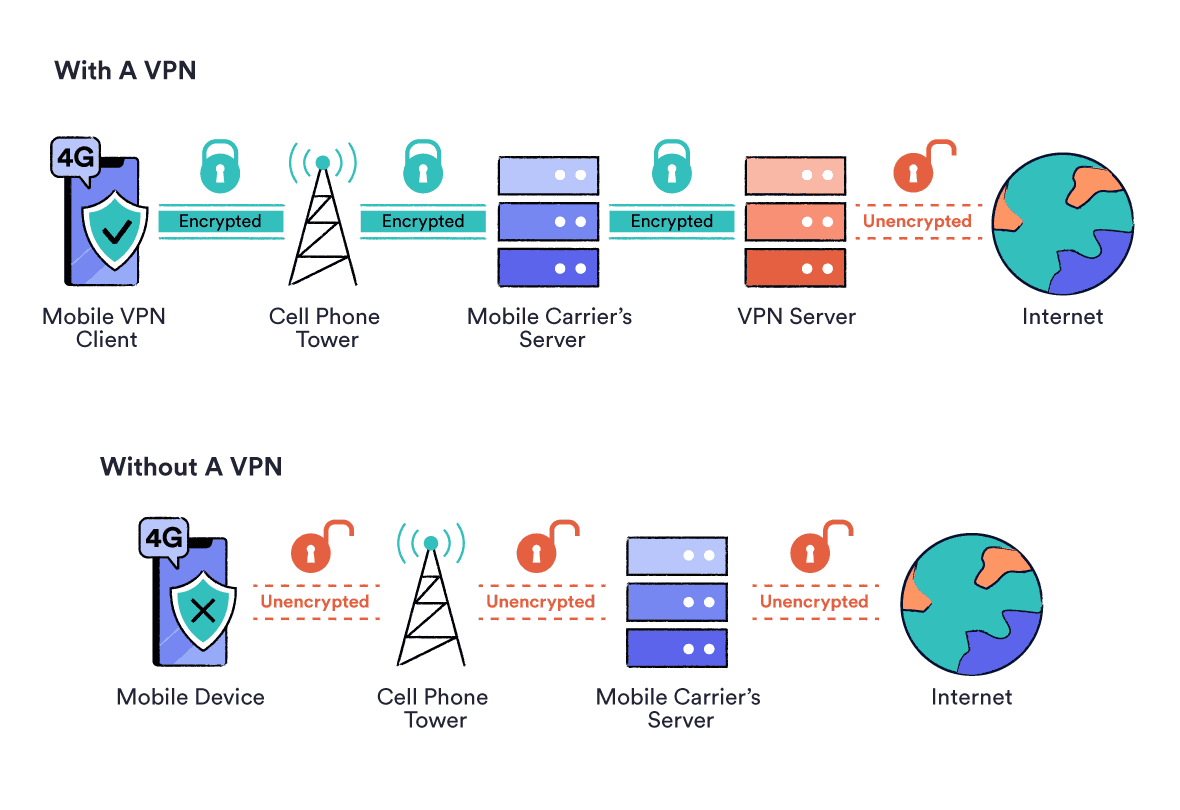
EXPERT ADVICE: We recommend using the IKEv2 VPN protocol when using a smartphone. It’s less secure than the standard OpenVPN or WireGuard protocol, but it is specifically designed to handle frequent switching between cellular data and Wi-Fi networks.
There are two important drawbacks to be aware of when using a VPN on your phone:
- VPN encryption means that using a VPN on your phone will increase your data consumption. If your cell provider caps your monthly data usage, or you’re paying for international roaming data, it might therefore be better not to use a VPN at all.
- Websites and services are less likely to use IP-based geolocation to determine your location when you connect from a mobile device. They may use the device’s in-built Global Positioning Systems (GPS), instead. Currently, the only VPN services that can spoof your GPS location are Surfshark, IVPN, and Windscribe.
Should You Leave Your VPN on All the Time?
If your primary concern is hiding your activity online, then it’s worth leaving your VPN on all the time. You’ll be exposed whenever you’re not using a VPN.
If you are more interested in unblocking geo-restrictions, bypassing specific IP-based bans, or accessing other types of blocked websites, then you don’t need to leave your VPN on all the time.
There is generally no harm in keeping your VPN switched on, but it will often lead to slower connection speeds, higher bandwidth consumption, and a higher chance that your connection will be blocked by websites and services that don’t permit VPN usage.
EXPERT ADVICE: Certain tasks on your local network, such as casting video content to your TV or connecting to a home printer, will not work while you are connected to a VPN.
What Should I Look for in a VPN?
Here are some of the most important features to look out for when choosing a high-quality, safe VPN service:
- IP Address Protection: Look out for VPN services that offer dedicated IP, DNS, WebRTC, and IPv6 leak protection tools to ensure your IP address is being protected.
- Robust VPN Protocols & Encryption: A VPN needs to use advanced protocols like OpenVPN or WireGuard, and a strong encryption cipher like AES-256 or ChaCha20.
- Zero-Logs Policy & Diskless Servers: A trustworthy VPN should not be keeping any logs that can be used to link your internet activity back to you. Look for a VPN service with an audited no-logs policy and diskless (or ‘RAM-only’) servers.
- Diverse Server Network: Look for a VPN service with a large server network that’s distributed across a diverse range of locations. This is important for accessing geographically-restricted content, ensuring fast connection speeds, and finding quick workarounds when your VPN connection gets blocked.
- VPN Kill Switch: A secure VPN needs to have a VPN kill switch that automatically disconnects you from the internet if the VPN connection falters.
- Additional Features: The best and most versatile VPNs include additional features like obfuscation, first-party DNS servers, and double VPN. These features are often particularly important for users in countries with strict online regulations, such as China.
- Device Compatibility: A good VPN service should offer native VPN applications on as many devices as possible, from iOS and Android smartphones to Windows and macOS PCs. It should also offer router compatibility and VPN extensions for Chrome and Firefox.
- Customer Support: Responsive and reliable customer support is essential. Look for a service with 24/7 live chat assistance to help you fix any connection problems, slow speeds, or streaming difficulties in a timely manner.
You can check out our VPN reviews or dive straight into our top-rated VPN services to help you find the right VPN for you.


