Top10VPN is editorially independent. We may earn commissions if you buy a VPN via our links.
The 4 Main Types of VPN
In This Guide
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs. In this guide, we explain how each of these VPN types work and when to use them.

A VPN creates a private tunnel within a public connection (e.g. the internet). VPN software allows its users to send and receive data transfers securely.
VPNs use different types of VPN protocols to encrypt web connections and make them private. Furthermore, different versions of VPN software exist.
Quick Summary: The Four Main Types Of VPN
- Remote access VPNs provide remote access to a private network. They’re ideal for organizations that need to give employees or others out-of-office access to the company network.
- Mobile VPNs allow you to connect to a local network. They are the best choice when users are unlikely to maintain a stable connection.
- Personal VPN services give individual users encrypted access to a third-party server. Routing your traffic through this server allows you to protect your identity and hide from surveillance. Additionally, it enables you to bypass geo-restrictions and circumvent firewalls in highly-censored countries.
- Site-to-site VPNs enable organizations to combine their networks from different locations into a single network called an intranet. You can also use a site-to-site VPN to invite partner companies into your network, known as an extranet.
VPN review websites mostly write about personal VPNs. These are used to create secure and private connections to the open internet, as well as for bypassing firewalls and geographic internet restrictions.
By comparison, businesses use a remote access VPN, which enables employees to access the company’s private network when traveling or working from home.
If the employee doesn’t have a consistent or stable internet connection, then a mobile VPN may be used instead.
Finally, when there are multiple sites or multiple companies trying to connect to a single private network (not just a single employee), then businesses will need to use a site-to-site VPN.
Comparison of the Four Main VPN Types
Here’s a table comparing the four main VPN types:
| Remote Access VPN | Personal VPN | Mobile VPN | Site-to-Site VPN | |
|---|---|---|---|---|
| Who Connects Where? | User connects to a private network. | User connects to the internet via a third-party server. | User connects to a private network. | Network connects to another network. |
| Software Required? | Users usually need to install software on their device, or configure their operating system. | Users install a VPN service’s software onto their device. | Users usually need to install software on their device, or configure their operating system. | Users do not need to run additional software. |
| Best Used For | Connecting to your company’s network – or any other private network – from home or another remote location. | Protecting your privacy and bypassing geographic restrictions online. | Achieving a consistent connection to a private network while using an unstable internet connection. | Joining up two or more networks, to create a combined single network. |
In this guide, we’ll explain each of these personal and business VPN types in more detail. We’ll cover how they work, what they are useful for, and provide examples of products in each category.
Why Trust Us?
We’re fully independent and have been reviewing VPNs since 2016. Our advice is based on our own testing results and is unaffected by financial incentives. Learn who we are and how we test VPNs.
Remote Access VPNs
A remote access VPN lets you use the internet to connect to a private network, such as your company’s office network.
The internet is an untrusted link in the communication. VPN encryption is used to keep the data private and secure as it travels to and from the private network.
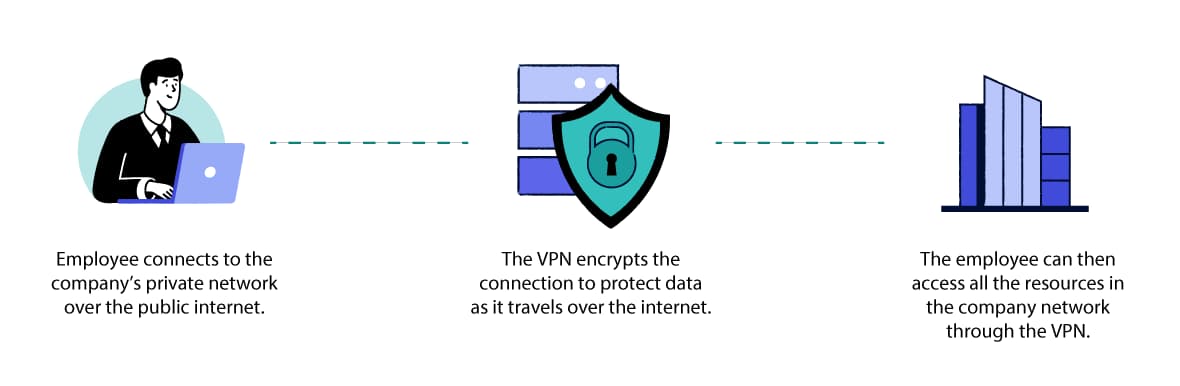
Companies use remote access VPNs to keep business information and documents private.
NOTE: Remote access VPNs are also sometimes called client-based VPNs or client-to-server VPNs.
When to Use a Remote Access VPN
There are different ways a remote access VPN can be used, for example:
-
A business traveler could use a remote access VPN to connect to their company’s network from the WiFi in the hotel lobby. They can access all the same files and software they would have in the office. The VPN also protects the data from anyone snooping on the public WiFi.
-
Somebody working from home could use a remote access VPN to access the company’s network from home. Their computer works as if it was connected to the company network in the office, and data is protected as it goes through the public internet.
EXPERT TIP: While remote access VPNs remain useful, cloud storage is a popular alternative if you just want people to be able to access files remotely. Cloud storage (such as Dropbox) uses an encrypted browser connection to protect your data, and is much easier to set up than a VPN is.
How Remote Access VPNs Work
To use a remote access VPN on your device you typically need to install client software or configure your device’s operating system to connect to the VPN. There also needs to be a VPN server on the network end of the connection.
There can be many client devices, as many different users can connect to the VPN server. Between them, the client software and VPN server manage the VPN connection.
Here’s how a remote access VPN works:
-
First, the VPN server checks that the user is allowed to access the network.
This might require the user to enter a password, or use biometrics such as a fingerprint to identify themselves. In some solutions, security certificates can be used to automatically authenticate the user in the background, enabling a faster connection. This is particularly helpful where the user needs to connect to multiple VPN servers – to access different site networks, for example.
-
Once the user is authenticated, the client and server establish an encrypted tunnel between them.
This is a wrapper of encryption that protects the traffic going over the internet. There are lots of different VPN protocols that can be used to set up the encryption tunnel: IPsec and SSL are two that are often used.
-
The user can now access resources through the VPN server.
This gives them access to a company’s internal network to access files or software.
Examples of Remote Access VPNs
Examples of remote access VPNs for business include:
- Access Server by OpenVPN, which is free for up to two simultaneous VPN connections.
- Cisco AnyConnect, which integrates with Cisco’s enterprise security solutions.
- Perimeter 81 Next-Gen Secure VPN Solutions.
NOTE: This type of VPN is typically licensed according to how many simultaneous users need to access the VPN.
Personal VPN Services
A personal VPN service connects you to a VPN server, which then acts as a middleman between your device and the online services you want to access.
The personal VPN – sometimes also called a ‘consumer’ or ‘commercial’ VPN – encrypts your connection, hides your identity online, and lets you spoof your geographic location.
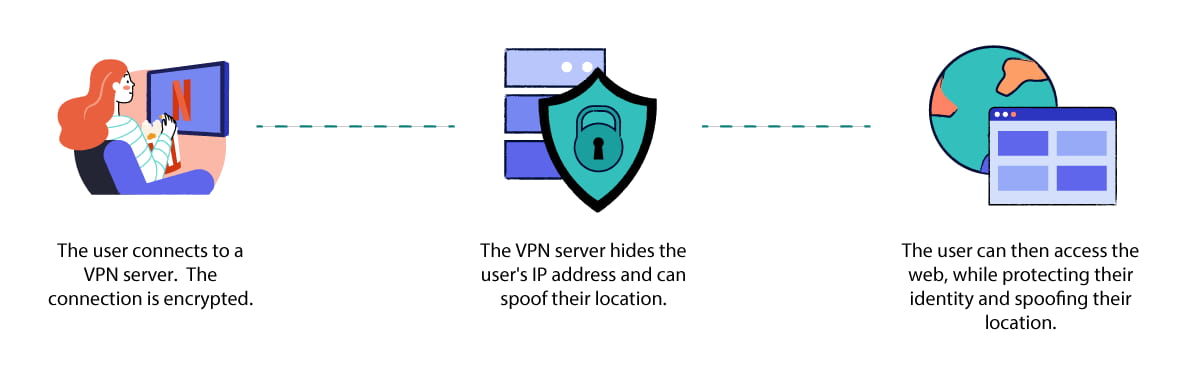
A personal VPN service hides your IP address and browsing history while you browse the internet in your free time.
A personal VPN service differs from a remote access VPN in that it doesn’t give you access to a private network.
Instead, a personal VPN works by giving you access to the public internet, but over an encrypted connection.
When to Use a Personal VPN Service
There are several reasons to use a personal VPN. Some of the most popular ones include:
-
Streaming online movies and TV shows unavailable in your geographic location. For example, you can connect to a VPN server in USA and access American Netflix, which is one of Netflix’s largest content libraries.
-
Evading web censorship and surveillance in authoritarian states, such as China and the UAE. A VPN gives you access to content blocked by national firewalls, and hides your web traffic from state surveillance systems.
-
Safeguarding your internet privacy by stopping your internet service provider (ISP), governments, hackers, and anyone else from snooping on your activity. ISPs sometimes throttle (or slow down) your connection if they can see you are streaming games or movies. Using a VPN stops them from knowing what you’re doing online and prevents them from throttling your internet connection.
For a more extensive list, read our dedicated guide to what VPNs are used for.
How Personal VPNs Work
Here’s how a personal VPN works:
-
Install software from your VPN service provider onto your device.
Personal VPN apps are available on all sorts of devices, including smartphones. Alternatively, you can install the VPN software on your router to protect all the devices that connect to it.
-
Connect to a server in your VPN provider’s network.
Personal VPNs tend to have large server networks to choose from. If you just want to protect your privacy, connect to a local server for the fastest speeds. If you want to unblock streaming content, choose a server in the country where that content is accessible.
-
Browse the internet like normal.
While connected to the VPN, all your internet traffic goes through the service provider’s server. Your connection is encrypted, your IP address is hidden, and you can access geographically restricted content from other countries.
EXPERT ADVICE: There are many protocols available for encrypting the connection. One of the most popular and most secure protocols is OpenVPN. Emerging protocols such as WireGuard and ExpressVPN’s proprietary Lightway protocol can be faster, and also work well.
Avoid using PPTP (which is easily hacked), L2TP/IPSec (which may be compromised by the NSA), and SSTP (which is vulnerable to attack).
Examples of Personal VPN Services
We’ve tested over a hundred personal VPNs since 2016. Currently, our three highest-rated VPNs are:
- ExpressVPN
- NordVPN
- Private Internet Access
NOTE: Personal VPNs are typically sold on a subscription basis, with discounts available when you pay upfront for a year or more. There’s also a small number of free VPN services that are safe to use.
Mobile VPNs
While remote access VPNs let you connect to a local network from anywhere, they do assume that the user will stay in one location. If the user disconnects, the IP tunnel closes.
A mobile VPN is a better option than a remote access VPN if the user is unlikely to have a stable connection, on the same network, for the entire session.
With a mobile VPN, the VPN connection persists even if the user switches WiFi or cellular network, loses connectivity, or switches their device off for a while.
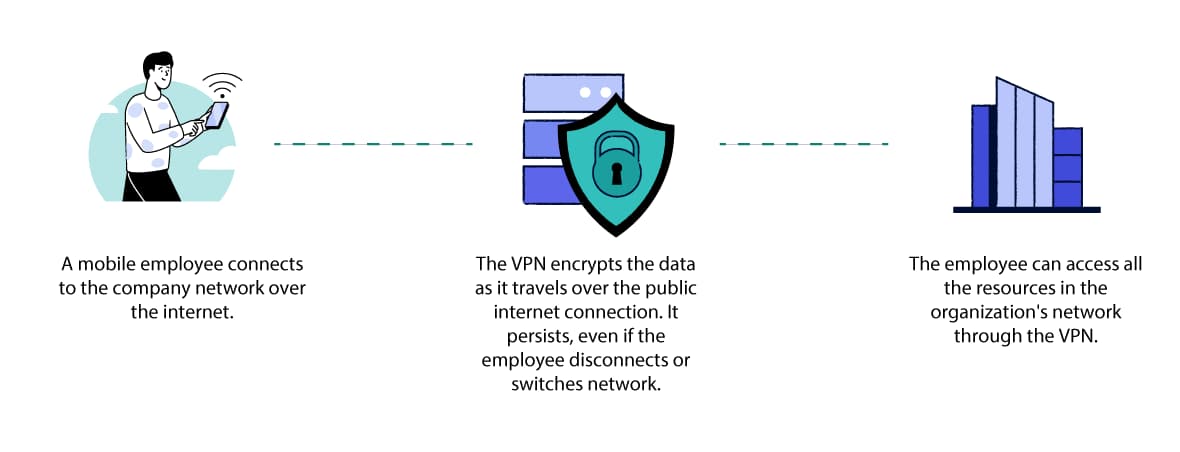
A mobile VPN connection persists even when there’s poor signal.
NOTE: A mobile VPN can be used with any device and any connection: it doesn’t have to be a mobile phone on a mobile network.
When to Use a Mobile VPN
Mobile VPNs tend to be used to ensure consistent availability for mobile workers, or for the convenience of having a VPN that tolerates connection changes. For example:
-
Firefighters and police officers can use a mobile VPN to stay connected to applications such as vehicle registration databases, automatic vehicle location, and computer-aided dispatch, even as they travel around.
-
Professionals working from home in an area with poor connectivity could use a mobile VPN to maintain VPN access to the office all day, even when the connection is lost.
How Mobile VPNs Work:
Here’s how a mobile VPN works:
-
The user connects to the VPN and is authenticated.
Authentication options might include passwords, physical tokens such as smart cards, or biometric devices such as fingerprint scanners. In some cases, certificates can be used so the authentication happens automatically in the background.
-
The VPN tunnel is established between the user’s device and the server.
In a remote access VPN, the VPN tunnel connects to the device’s physical IP address, which is tied to its internet connection. In a mobile VPN, the VPN tunnel connects to a logical IP address, which is tied to the device, and so is independent of the internet connection.
-
The VPN connection persists as the user switches between different networks.
If the user is mobile, they might switch between networks (for example, between cellular or WiFi networks). Their physical IP address can change, but the logical IP address the VPN tunnel uses stays the same. The virtual network connection remains intact, so the user can continue working seamlessly as long as they have any connection.
If the device is turned off to preserve the battery life, the VPN connection is still available when the device is switched back on.
Examples of Mobile VPNs
Mobile VPN examples include:
- Bittium SafeMove Mobile VPN: automatically connects users and provides seamless roaming.
- Radio IP software: enables mobile VPNs across all wireless network technologies.
NOTE: Many personal VPNs offer mobile versions of their service that you can download onto your cell phone. These are not the same as mobile VPNs. Mobile VPNs are usually a form of business VPN, used by employees to access the company network.
Site-to-Site VPNs
Whereas a remote access VPN is designed to let individual users connect to a network and use its resources, a site-to-site VPN joins together two networks on different sites.
If a company had two offices on the east coast and west coast, for example, a site-to-site VPN could be used to combine them into a single network.
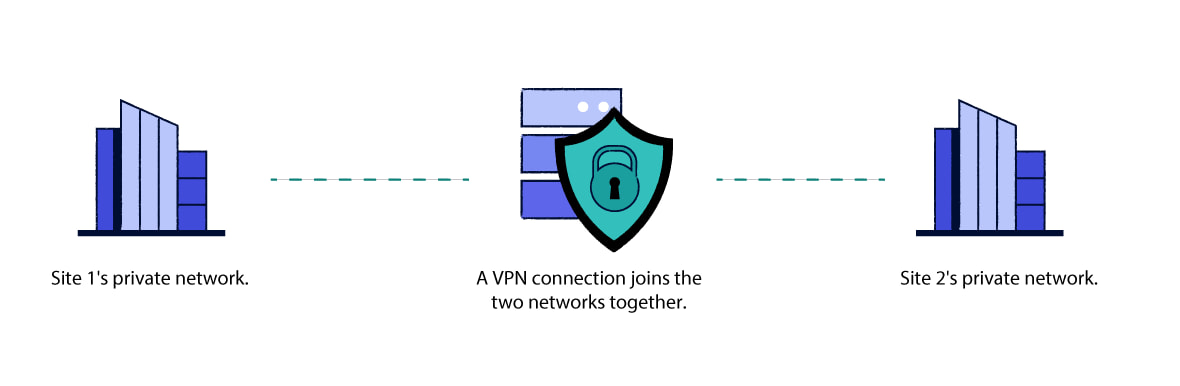
Companies might use site-to-site VPNs if they offices in different locations.
Different technologies can be used to implement a site-to-site VPN. These include IPsec, Dynamic MultiPoint VPN (DMVPN), and L3VPN.
NOTE: Site-to-site VPNs are also sometimes known as network-based VPNs.
When to Use a Site-to-Site VPN
Depending on who owns the networks being joined, there are generally two different forms of site-to-site VPN:
-
Intranet-Based VPN: When the networks being connected belong to a single company, the combined VPN is known as an intranet-based VPN. This enables a company to establish a single wide area network (WAN) that spans two or more of its offices. Users in the company can access resources from other sites as easily as if they were on their own site.
-
Extranet-Based VPN: When the networks being connected belong to different companies, the combined VPN is known as an extranet-based VPN. An extranet VPN is used, for example, when a company wants to connect to its supplier’s network, so they can trade more efficiently.
EXPERT ADVICE: A site-to-site VPN and a remote access VPN can be combined. For instance: a site-to-site VPN could be used to create a single network that spans the company’s offices across the globe. Then, a remote access VPN could provide access to that network to any employees working from home.
How Site-to-Site VPNs Work
There are three main ways a site-to-site VPN can be implemented:
- Using an IPsec tunnel
- Using a Dynamic MultiPoint VPN (DMVPN)
- Using a Layer 3 VPN (L3VPN)
IPsec tunnel
An IPsec tunnel can be used to join sites together, in much the same way it connects individuals to a private network within remote access VPNs.
In this case, however, the VPN is implemented by routers at the two or more sites that are connecting to each other. For this reason, it’s sometimes also called a router-to-router VPN.
Whereas a remote access VPN creates a tunnel for one device to connect to the private network, with a site-to-site VPN, the IPsec tunnel encrypts the traffic between the connected networks. This can take two forms:
- A route-based IPsec tunnel allows any traffic between the networks through. It’s like wiring the networks together.
- A policy-based IPsec tunnel sets up rules that decide what traffic is allowed through, and which IP networks can talk to which other IP networks.
IPsec tunnels can be built using most firewalls and network routers.
Dynamic MultiPoint VPN (DMVPN)
The problem with IPsec tunnels is that IPsec connects two points to each other. In a site-to-site network, for example, IPsec could be used to connect two routers to each other.
That doesn’t scale well in large companies with thousands of sites, where thousands of connections might need to be established.
Instead, Cisco’s Dynamic MultiPoint VPN (DMVPN) technology offers a solution. It enables sites to connect to the DMVPN hub router using dynamic IP addresses.
The network architecture is a hub-and-spoke design, which reflects the fact that most traffic goes between branch sites (spokes) and the main site (hub), rather than between one branch and another.
That said, it’s still possible for branch sites to connect to each other using a DMVPN. It just takes a little additional configuration.
NOTE: DMVPN requires Cisco routers. Here’s a comprehensive guide to designing a DMVPN architecture.
MPLS-based Layer 3 VPN (L3VPN)
The IPsec and DMVPN approaches both sit on top of the internet, which means they can’t offer consistent or guaranteed performance.
By contrast, Multi-Protocol Label Switched (MPLS) Layer 3-based VPNs can provide a guaranteed quality of service, with global connectivity. This is because MPLS is a way of routing packets across a network via any transport medium (such as fiber, satellite, or microwave) and any protocol.
Service providers can therefore use MPLS to create a Layer 3 VPN. The ‘Layer 3’ refers to the OSI network model, which uses multiple layers to explain how communications are converted between electrical, radio, or optical signals into application data. Layer 3 means the VPN is created in what’s called the ‘network layer’.
While some large companies might set up their own MPLS VPNs, they’re usually created by communications service providers.
The service provider can create a separate virtual network for each customer, which it resells as a wide area network (WAN). The virtual networks are isolated from each other, even though they may share some of the same physical network resources.
If you buy a WAN service from a communications service provider, it could well be using an MPLS L3VPN, without you necessarily knowing.
With an MPLS VPN, it’s possible to prioritize certain types of high-priority traffic, such as voice traffic, to ensure a better quality of service. The route through the network can be precisely controlled, too, to enable consistent and well-optimized performance.
Private WAN services are expensive, so there’s a trend for companies to decommission MPLS services in favor of cheaper internet-based VPNs. The main exceptions are for situations where any latency is critical – for example, in applications that detect faults and outages in the power grid.
NOTE: L3VPNs are also sometimes known as Virtual Private Routed Network (VPRNs).
Examples of Site-to-Site VPNs
Examples of the different types of site-to-site VPN include:
- Access Server by OpenVPN, can be used to create a site-to-site VPN.
- Cisco’s Dynamic Multi Point VPN (DMVPN), is described in more detail here.
- Nokia provides instructions for setting up a VPRN service (L3VPN).


