Top10VPN is editorially independent. We may earn commissions if you buy a VPN via our links.
Virtual Server Locations & Rented VPN Servers Explained
Our Verdict
Virtual server locations are simply VPN servers that assign an IP address that’s different to their geographical location. This makes them just as safe as normal physical servers. VPN networks are usually a mix of colocated and rented servers, which can be just as safe as first-party servers, as long as the data center is vetted properly by the VPN service.

At the most basic level, VPN servers are simply computers designed to host and deliver encrypted tunneling services. VPN servers can be either physical or virtual, and companies can either rent or own the servers they use.
Every VPN’s server network is slightly different. Some VPN services rent large portions of their server infrastructure, so their users can access a wider range of locations.
It’s also common for VPN companies to use virtual server locations. These provide users with an IP address from one country, even though the server is physically located in a different country.
Both of these variables come with privacy and security concerns if not implemented correctly. It’s possible for a VPN to be hacked through compromised servers, which is why it’s important your VPN takes the management of every server seriously.
Summary: Virtual Server Locations & Rented VPN Servers
- Virtual server locations are servers that are not physically based in their advertised location. For example, a VPN server that offers an Australian IP address but is physically located in the US. These servers are safe to use, as long as VPNs are transparent about their real location.
- Virtual VPN servers are servers hosted on virtual machines. These are only a danger to users when the VPN service doesn’t also own or rent the underlying physical hardware.
- Rented VPN servers are servers leased from a third-party landlord, such as a data center. Rented servers are just as safe as first-party owned servers, as long as the VPN enforces a stringent vetting process and remotely monitors the server effectively.
In recent years, we’ve seen some VPN services come under scrutiny for how they manage their servers — the NordVPN hack in 2018 is a good example.
Some companies are upfront about how they control their network, while others are less transparent. It can be difficult to know exactly where your data goes and who is responsible for it.
In this guide, we’ll explain the different ways a VPN service can implement its server network, and how this can impact your online privacy and security.
Why Trust Us?
We’re fully independent and have been reviewing VPNs since 2016. Our advice is based on our own testing results and is unaffected by financial incentives. Learn who we are and how we test VPNs.
How Do VPN Services Implement Their Server Networks?
There can be huge variation in how commercial VPN services choose to implement their networks. Often, users aren’t aware of these nuances, or simply don’t consider them. This makes picking the right VPN service all the more important.
Here is a table comparing how the most popular VPN services implement their VPN server networks:
| VPN Service | Server Ownership | Virtual & Physical Servers | Virtual Server Locations |
|---|---|---|---|
| ExpressVPN | Rented | Physical | Yes |
| NordVPN | Colocated & Rented | Both | Yes |
| Private Internet Access | Colocated & Rented | Physical | Yes |
| Surfshark | Rented | Both | Yes |
| PrivateVPN | Colocated & Rented | Both | 1 – India |
| Proton VPN | Owned & Rented | Physical | Yes |
| Windscribe | Colocated & Rented | Physical | 1 – Antartica |
| Mullvad | Colocated & Rented | Physical | No |
NOTE: For security reasons, not all VPN release details about their server networks. The table above uses information available to subscribers and the public.
If you’re concerned about your online privacy, we suggest using a VPN that is transparent about its data center vetting procedures, the use of fake server locations, and rented servers.
While we can’t expect every VPN to own its entire server network — or openly discuss every detail of its operations — we should be holding the VPN industry accountable when it comes to server breaches.
You should be looking out for the following factors:
- Server Ownership: VPN providers can either rent or own the servers that form their network. As long as the VPN service is rigorous in its vetting of data centers and diligent in its remote monitoring of the server, rented servers shouldn’t be an issue for the majority of VPN users.
- Virtual and Physical Servers: From a user’s perspective, the difference between these two is usually unimportant. The only danger arises when providers use general-purpose cloud hosting services to rent just a virtual server. When providers don’t also own or rent the underlying physical hardware, they put their user’s privacy at risk.
- Virtual Server Locations: VPN servers can be physically located in a different location to the IP address they assign. This practice is only problematic for VPN users when providers are not transparent about it.
With this information, you can make an informed decision about which VPN is the best fit for your needs.
In the next sections, we’ll discuss the issues of server ownership, virtual machines, and virtual server locations in more detail.
VPN Server Ownership & Rented Servers
VPN services have the choice between renting or owning the servers in their network. This can have important consequences for privacy, security, and performance.
While investigating VPNs, we found some VPN services are reluctant to disclose when they are using rented servers.
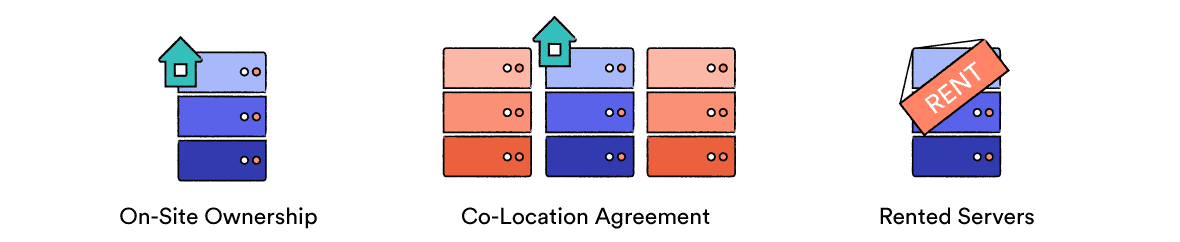
Here are the three main options when it comes to server ownership:
- On-Site Ownership: The VPN purchases, installs, and maintains its servers itself. The servers are owned outright and stored somewhere on company premises, so only trusted employees have physical access to them.
- Colocation Agreement: The VPN owns and operates its servers but stores them off-site, usually in a data center. For a fee, the data center provides storage, air conditioning, and bandwidth. The company’s staff monitor the server remotely and visit the data center to repair hardware when needed.
- Rented Servers: The VPN service rents its servers straight from a data center. This allows it to avoid the expense, time, and expertise required to purchase, install, and maintain a physical server. The data center handles the hardware, and the VPN company is given remote access to handle the software.
Below, we’ll explain the different ownership options available to VPN services, along with their advantages and disadvantages.
On-Site Ownership
| Pros | Cons |
|---|---|
| Complete control over hardware and network | Huge up-front costs |
| Prevents third parties physically accessing the server | Weakened connection speeds |
| Prevents third party logging server data | Smaller server networks |
From a privacy and security perspective, the ideal VPN service owns its entire server network and stores it on-site. This way, the VPN service knows everything about the hardware they use and no one can physically access the VPN servers other than the provider’s employees.
Importantly, it also prevents other third parties from logging server activity. VPN logging policies apply only to the VPN company, and not to any other parties they might work with. A zero-logs policy is useless if there is a data center monitoring server activity and collecting logs.
For this reason, first-party on-site ownership is the only way to ensure that there is absolutely no third-party involvement beyond the company that users have explicitly chosen to place their trust in.
However, although it’s great for security, there are some reasons why on-site ownership isn’t a practical solution for most VPNs.
Firstly, it’s extremely expensive. VPNs need to fund and power a network of servers, bandwidth and cooling facilities, back-up hardware, and a team of administrators. With each new server location, these costs are multiplied, making it far cheaper to host in a data center instead.
On-site servers sometimes have slower speeds and higher latency than rented or colocated servers, too. This is because they’re often based further away from internet exchanges — in terms of network hops — than large data centers.
Top-tier VPNs want to offer large server networks for their users. Strict on-site ownership restricts a VPN’s ability to expand their network, as the VPN service would have to own land in every location they want to place a physical server.
Colocation Agreements & Rented Servers
| Pros | Cons |
|---|---|
| Remote management ensures servers are not tampered with | Third parties might have access to servers |
| Data centers provide faster speeds | Data center servers might be vulnerable to traffic monitoring |
| Larger server networks | |
| Faster connection speeds | |
| Cheaper than on-site ownership |
If a VPN service wants the security benefit of owning its VPN servers without the drawbacks of storing them, the best option is a colocation agreement with a trustworthy data center so they can physically inspect and audit server hardware.
Rented VPN servers are installed, monitored, and maintained entirely by data center employees. In theory, this third party has the ability to tamper with the server’s hardware.
In reality, most modern (rented and colocated) servers are equipped with a Remote System Management Card. Combined with real-time system logging, VPN services can remotely monitor almost everything about a server’s operation.
If anything suspicious happens, the VPN service can investigate it and shut down operations accordingly. However, to keep mitigating this risk, the VPN service must regularly check on its rented or colocated server.
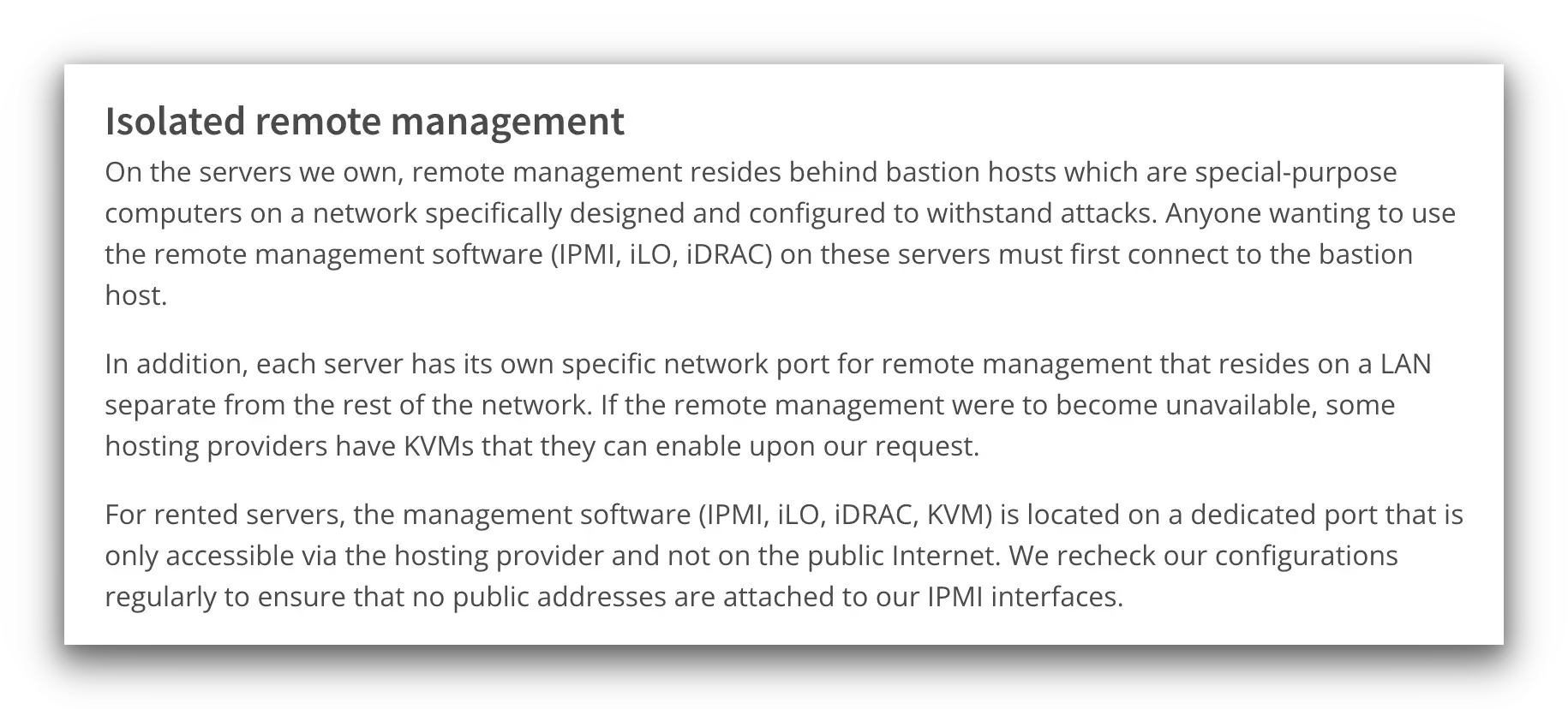
Mullvad checks its physical and rented servers regularly using remote management software.
Both colocated and rented VPN servers face a single privacy issue: the networking environment around them.
Any server in a data center is connected to that data center’s network. This means VPN providers have little knowledge or control of the network infrastructure that is upstream of their servers.
This means VPN service can never be sure that their server isn’t being monitored. Attackers and intelligence agencies can use the upstream network switch to record all the activity going in and out of a targeted server.
This is particularly relevant to data centers in countries with invasive data privacy laws. Local authorities could monitor upstream traffic or even compel the data center to store information locally and share it with them. This effectively amounts to logging on behalf of the data center without the VPN provider’s knowledge.
Encrypted VPN traffic should be safe from snooping. However, traffic correlation attacks are still a possibility and attackers might still get access to certain metadata, like the user’s originating IP address.
Both rented and colocated VPN servers share the benefits of being in a data center. This allows them to be close to (and sometimes even peer directly with) an internet exchange, which greatly improves speed performance.
However, VPN services with rented server networks have a lot more flexibility. Rental agreements can be scaled up or down to match user demand. They can quickly offer new locations, IP addresses, and offer faster connection speeds.
In contrast, colocation agreements keep providers tied-down to the hardware they have purchased and installed.
Which VPNs Rent Their Servers?
A majority of VPNs combine both rented and co-located servers in their networks. Here is a list of safe VPNs that rent some of their server network:
- Mullvad
- NordVPN
- Private Internet Access
- PrivateVPN
- Proton VPN
- Windscribe
To ensure their rented servers are safe for users, high-quality VPNs like PIA and NordVPN, carefully select server providers that respect user privacy and aren’t affiliated with authoritarian governments.
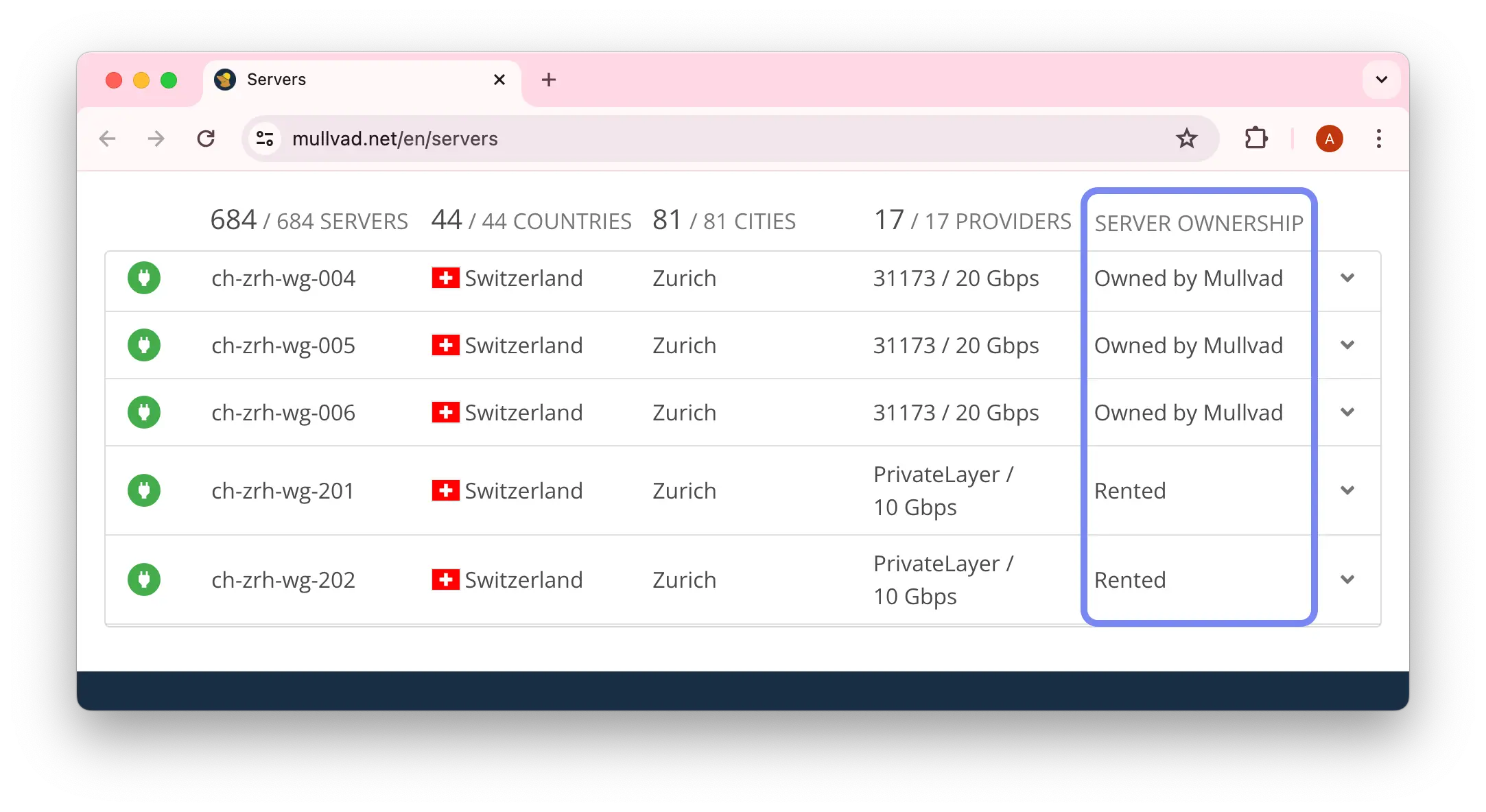
Some VPNs, like Mullvad, clarify whether they own or rent specific VPN servers.
The best VPNs will rigorously vet the data center it is renting servers from. This vetting process will include a full hardware audit and an inspection of the data center’s networking environment in order to understand any potential threats.
We urge any VPN service with rented servers to be more transparent about their data center vetting process, so users can have full confidence that their servers are safe to use.
Physical Servers & Virtual Servers
Physical servers/bare-metal servers are machines with a hard drive, CPU, processor, network connection, and more. They are probably what you picture when thinking of a VPN server.
Virtual/Virtual machine servers are run on a virtual machine that’s running on a physical server. Virtual servers aren’t so common among VPNs because they can be vulnerable to cyberattacks. But they are cheaper to run, environmentally-friendly, and are easier to migrate.
Physical servers are far more common in the VPN industry, and have been the industry standard the past decade. However, physical servers are less energy efficient, and most VPN users won’t notice a difference in performance.
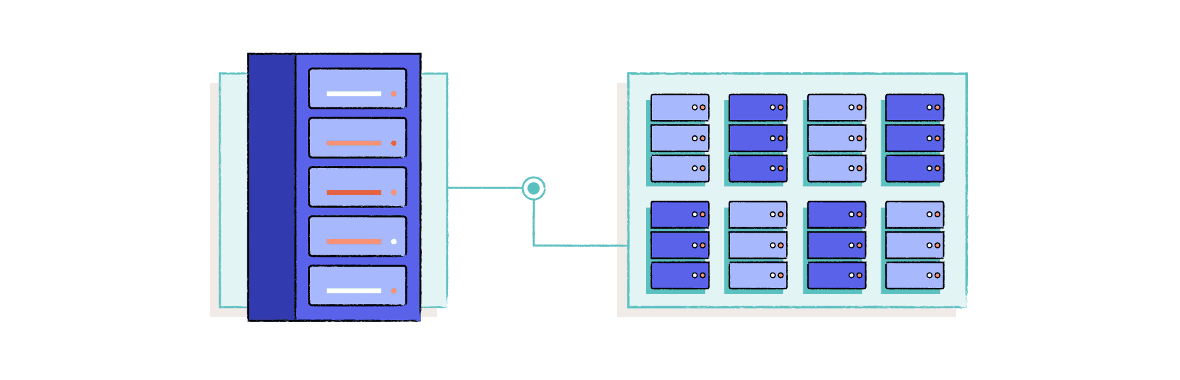
One physical server can host a single VPN, or host multiple virtual machines, each with their own VPN server.
Physical servers offer slightly better performance because they use all of the server’s resources. In contrast, virtual servers can only use a fraction of their physical server’s resources.
Virtual servers are cheaper to run because they maximize server utility. Running multiple virtual machines on physical servers helps reduce costs, which results in cheaper subscription fees.
Migrating virtual machines for hardware repairs or updates is much easier with virtual servers than physical servers. Having a virtual server can dramatically decrease a server’s downtime when conducting necessary updates.
Data centers typically have large carbon footprints. A VPN service can greatly reduce their environmental impact by making physical servers run multiple virtual VPN servers. Some VPNs that use virtual servers include: NordVPN and Hotspot Shield.
The main drawback to virtual servers: dangerous general-purpose cloud hosting or Virtual Private Servers (VPS). This is when a VPN rents a virtual space on a physical server and hosts their VPN there, instead of renting the whole physical machine.
We advise only using VPN services with virtual servers that own or rent the entire underlying physical machine.
A cloud-hosting service that owns the physical server can run multiple virtual machines, renting them out to different clients, who might be running websites or storing databases.
Until recently, this was considered a secure way to host a VPN server. However, a series of CPU side-channel attacks – such as Spectre, Meltdown, and Zombieland – have rendered general-purpose cloud hosting a privacy red-flag for VPN services.
Importantly, a VPN provider that owns or rents the underlying hardware and not just the virtual machine, is not at risk of CPU side-channel attacks. This is because they have complete control over what is happening on the physical server’s other virtual machines.
Virtual VPN Server Locations
| Pros | Cons |
|---|---|
| Larger server networks | Harder to assess privacy laws |
| Avoid poor internet infrastructure | Slower speeds |
| Avoid authoritarian governments eavesdropping |
A virtual server location is when a VPN server’s physical location differs from where its IP address is registered.
Virtual server locations are typically looked down upon. But in reality, the issue is far more complex and there are actually great advantages to using virtual locations.
Virtual locations allow VPN providers to increase the size of their server network. This is a fringe case, but if the virtual server is physically closer to you, then it will deliver faster speeds than a physical server in your target location.
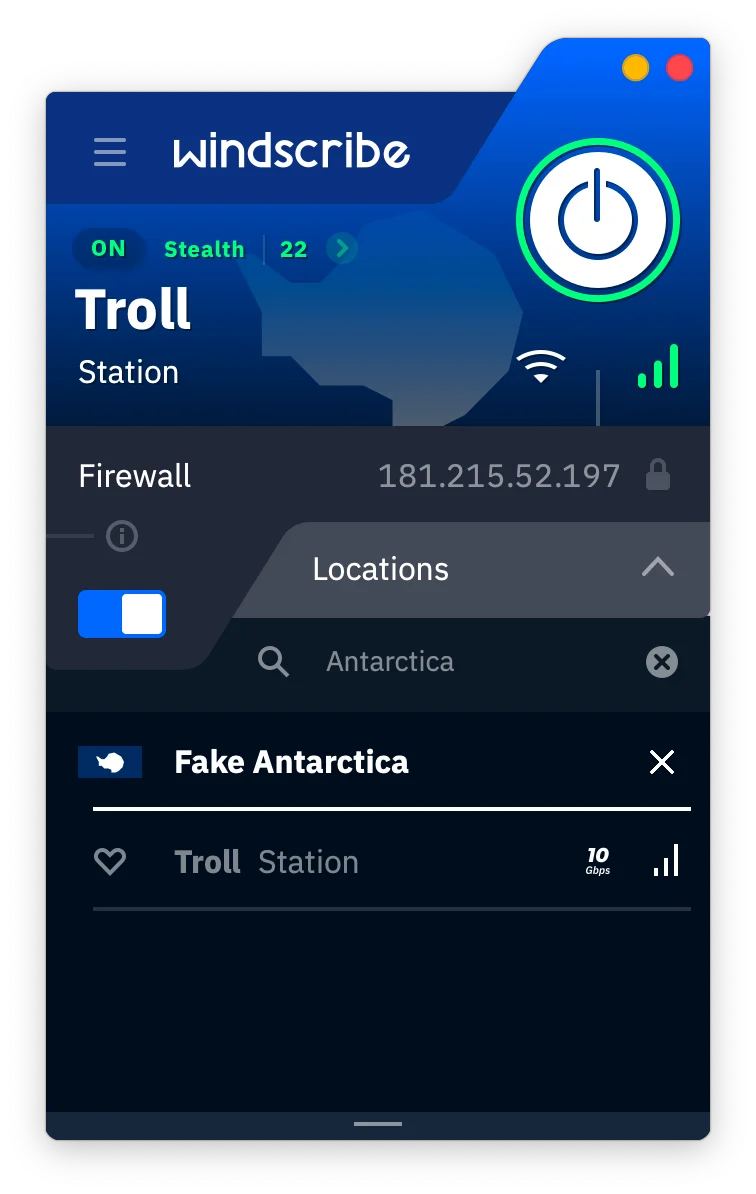
Windscribe offers a Fake Antarctica server that’s actually based in Toronto.
In addition, some countries don’t have the network infrastructure to support a reliable and secure VPN server network. Here, VPN companies can use virtual server locations to provide users with an IP address in those countries without using unreliable data centers.
Importantly, a majority of VPNs avoid placing physical servers in countries with authoritarian or censorious governments. Instead, they deploy VPN servers in safer countries and utilize virtual locations to provide IP addresses from those countries.
However, there are some legitimate concerns when it comes to using virtual server locations.
Depending on where a VPN is based, every country has different logging and data sharing laws. Virtual server locations make it much harder to assess the impact of a jurisdiction on your privacy.
You might purposefully connect to a VPN server close to your real location in order to maximize speeds. If the VPN server is physically located elsewhere, the user will experience slower speeds than anticipated.
Which VPN Providers Use Virtual Server Locations?
Some VPN services state exactly where each server is based. However, many VPNs use virtual server locations without publicly disclosing it, or make it very difficult for users to decipher between the two.
Some VPNs, like Hide.me, Mullvad, and Astrill VPN advertise their all-physical server network, ensuring the VPN server is physically located in the country advertised.
IPVanish similarly emphasizes its physical sever network — save for India, which is a virtual server location due to concerning data sharing laws.
However, virtual server locations aren’t inherently bad, and can even protect you from authoritarian governments. Most top-rated VPNs are open about their use of virtual server locations, like:
- ExpressVPN
- Private Internet Access
- CyberGhost
- Surfshark
How to Test Your VPN Server For a Virtual Location
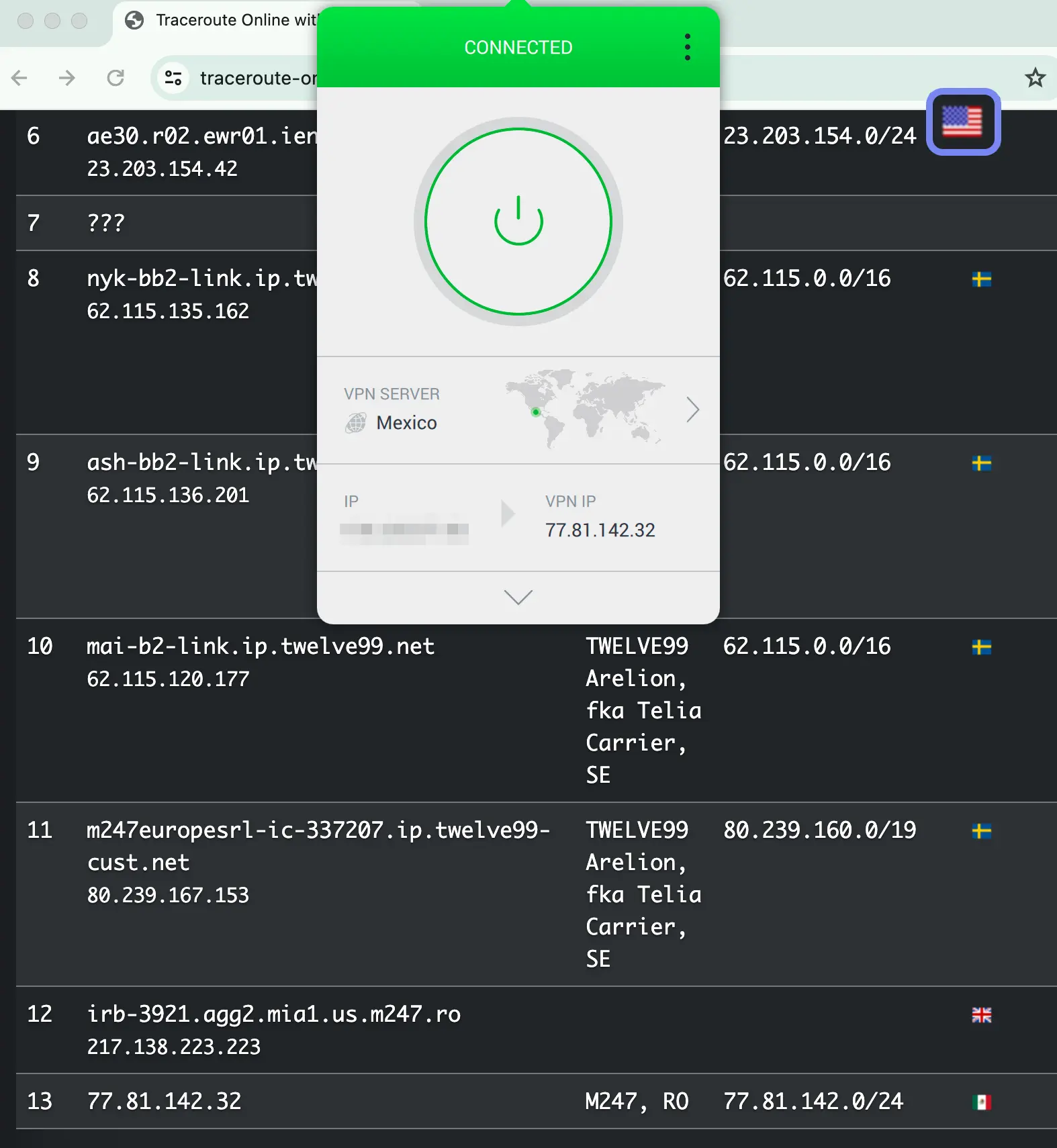
We traced PIA’s Mexico virtual server location back to a US-based VPN server.
In this section, we’ll teach you how to discover where a VPN server is really located. Follow these instructions to find out whether your provider is being honest about its use of fake server locations:
- Find the VPN server IP address: connect to your VPN server of choice and check your new IP address.
- Conduct a world ping test to find your VPN server’s nearest location: go to world ping test, type in your VPN server IP address and click start. Now find the location with the lowest ms. This will be your VPN server’s closet location.
- Run traceroute test to find out where your data packets are being sent: go to traceroute, enter your VPN server IP address, and click traceroute. Scroll down to the results to see the first country your data packets leave before arriving at your virtual server location. This will be the real location of your VPN server.
- Verify your results with another ping tool: open a separate ping tool and verify your findings.
It’s worth noting that this is not an exact science. Ping time is an indicator of geographic location, but a number of factors can distort it, such as your internet speeds and overloaded routers or servers.


