Top10VPN is editorially independent. We may earn commissions if you buy a VPN via our links.
VPN Logging Policies Explained
In This Guide
Understanding what type of data your VPN collects is a crucial factor when it comes to protecting your privacy. Find out which providers you can trust in this comprehensive guide to VPN logs.

When you browse the internet with a VPN you are trusting your VPN service provider with sensitive information.
Depending on its logging policy, your VPN service could monitor and store your IP address, choice of server location, and even the websites you visit.
In short, there are dozens of sensitive logs a VPN may collect and share if obliged to do so. What a VPN logs is therefore a critical issue if you’re concerned about your digital footprint. We explain what VPN logs are, and which types of logs actually matter, in the video below:

Our research found that some of most popular VPN providers collect their user’s web activity and share this information with third parties.
We thoroughly examined the logging policies of the 62 most popular VPN services on the market.
To our surprise, the majority of VPNs log some kind of data, under the grounds of service improvements or troubleshooting:
- 39% log connection timestamps
- 26% store original IP address
- 10% record browsing activity data
- 6% log server IP address
See which data the 62 VPNs we analyzed log in our guide to the best no-logs VPN services.
The best VPN services truly endeavor to protect their users’ privacy and security. The companies are transparent about what type of data they collect, why this data is necessary, and for how long they store it.
Sadly, this level of transparency is rare.
The logging policies of popular VPN services are often vague, complicated, or misleading.
Many VPN services falsely claim to collect a minimal amount of data, or no data at all. Others are deliberately vague about the exact type of data their policy refers to.
To add to the confusion, marketing statements on VPN websites rarely reflect actual privacy policies. With over 300 VPN services on the market, it’s difficult to know who to believe.
How can you find a VPN that’s worthy of your trust?
In this guide, we examine the different types of VPN logs, why certain VPNs keep logs, and what you can do to protect your privacy.
What Types of Data Do VPNs Log?
There are three types of data your VPN might record: activity logs, connection logs, and aggregated logs. Understanding what type of data falls into these categories is paramount if you’re to effectively protect your privacy.
1Activity Logs
Collecting activity data is the most invasive type of logging. It removes any privacy or anonymity benefit that a VPN might otherwise afford.
Also known as ‘usage logs’, this refers to any data explicitly related to your online activity.
Activity logs can include:
- Browsing history
- DNS requests
- URLs visited
- Usage metadata
Hola VPN’s privacy policy provides a good example of activity logging:
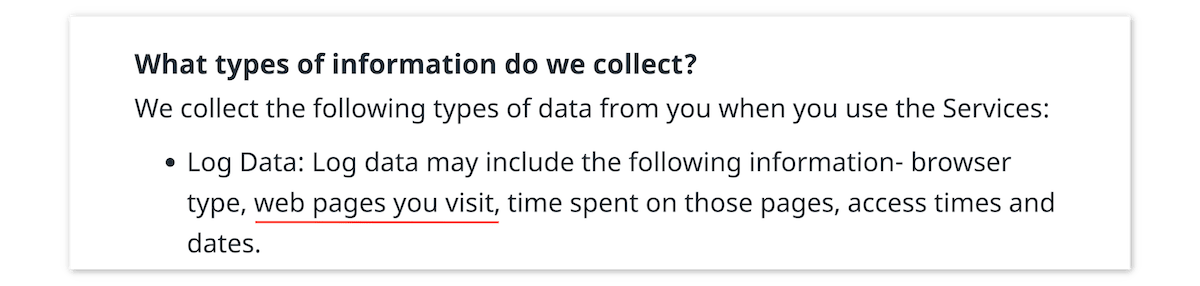
Screenshot from Hola VPN’s privacy policy.
Free VPN applications like Hola VPN are a common culprit for collecting activity data. This data is often shared or sold to third parties for advertising purposes, effectively subsidizing the cost of a subscription.
Some subscription-based ‘no-log’ VPN services monitor user activity if they are suspicious about an individual, or if they are legally compelled to do so. Others will record user activity in real-time and then delete it when the VPN session is over.
For example, our review of SkyVPN found the service logs personally identifiable information such as your originating IP address and location information:
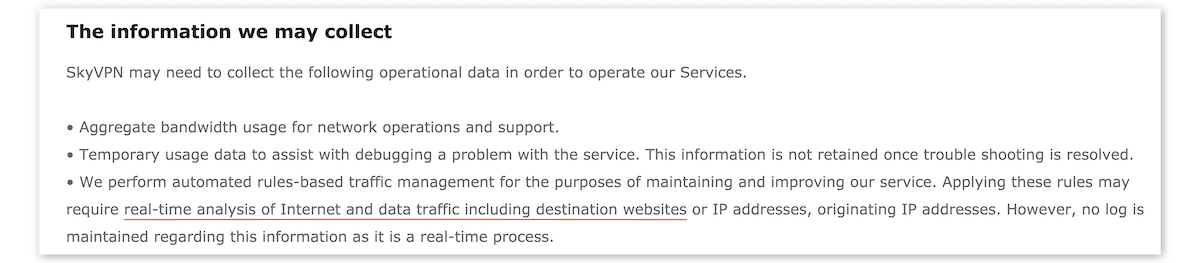
Screenshot from SkyVPN’s privacy policy.
Because the data is deleted so quickly, this type of activity logging isn’t too much of a concern. That being said, it’s best to avoid it where possible.
Other providers like Hide.me are technically incapable of collecting activity logs due to the configuration of their network. From a privacy standpoint, these providers are your best option.
Needless to say, any VPN storing activity data should be avoided at all costs. If you’re concerned about activity logging, take a look at the most popular VPNs that log your activity data.
2Connection Logs
Connection logs can include:
- Bandwidth usage
- Dates and times of connection
- Originating IP address
- VPN server IP address
Connection logs can be collected at the server-level (e.g. total server bandwidth usage) or the user-level (e.g. your originating IP address).
Typically, this data is used to optimize network performance and troubleshoot customer queries.
Server-level connection logs are a great example of why not all logging is a problem. It’s practically impossible for a VPN to maintain performance without logging any data whatsoever.
In fact, monitoring and storing the right, non-identifiable data will help ensure you get the best possible experience from your VPN.
However, storing the wrong connection logs could allow a VPN service to match you to your activity. This could be used to personally identify you, which is a major problem for privacy-conscious users.
If you’re concerned about the type of connection data your VPN is logging, continue reading to find out exactly what kind of logging is unacceptable.
Here is an example of detailed user-level connection logs from Thunder VPN’s logging policy:

Screenshot from Thunder VPN’s privacy policy.
Claims that this data is only used to “deliver the best possible experience” or “improve customer service” are rife, but we know from experience that this level of detail isn’t necessary to maintain a well-performing VPN network.
3Aggregated Logs
Some of the most popular VPNs on the market collect aggregated logs. This means the VPN is collecting information that is supposedly anonymized and impossible to link to a specific user.
A VPN service might collect the websites that you visit, the bandwidth you use, or the dates and times you connect to a server. They will then strip this information of any identifying factors and add it to a larger database.
It’s important to be aware that some VPNs claim that they don’t keep logs when in fact they keep aggregated logs. Anchorfree’s privacy policy is a good example of what to look out for:

Screenshot from Anchorfree’s privacy policy.
Ultimately, aggregated and anonymized data is not always the magic bullet that marketing teams will have you believe.
The exact type of data being aggregated and the efficacy of the anonymization process will dictate whether or not this type of logging is acceptable. You just have to trust that your VPN service is anonymizing your data effectively.
If this is a leap of faith you are uncomfortable with, you’re better off choosing a truly no-logs VPN service.
What Is a No-Logs VPN?
A truly no-logs VPN service does not collect or store any activity or connection data that could be used to personally identify you. Most importantly, it will not collect or hold any information transmitted through the VPN tunnel whatsoever.
This will ensure that no user can be tied to any specific activity or connection on the VPN network. Every user will be private, anonymous, and unknown even to the VPN provider.
The only identifying information a no-logs VPN will have is your email address (for registering your account) and billing (in case you want a refund).
NOTE: Some VPN services, like ExpressVPN, allow you to pay with Bitcoin in order to avoid the identifying payment process. Mullvad VPN even lets you pay in cash.
No Log VPNs can’t be compelled to make user data available to authorities or third parties, as the data simply doesn’t exist.
This is how a strong logging policy can offset the issue of an unsafe VPN jurisdiction.
It’s important to note that “no-logs” doesn’t necessarily mean that absolutely no data is kept at all. Genuine “zero logging” is effectively impossible to implement while maintaining a strong network or enforcing restrictions like device limits.
Most VPNs will keep very basic data like aggregate server load information (the number of users or bandwidth used per server). This is a justifiably minimal approach to logging which involves absolutely no identifying information. This is still classed as a no-logs VPN.
EXPERT ADVICE: If you’re looking for a VPN you can trust with your privacy, we’ve created a list of no-log VPNs that have been verified by third parties.
What Kind of Logging Is Acceptable?
Some of the best providers on the market keep basic connection data that cannot be used to identify a given individual. It is justifiable for a legitimate VPN service that is committed to its users’ privacy to collect the following information:
- Aggregated Bandwidth Usage
- Aggregated Connection Logs
- VPN Server Location
- Server Load Data
- Subnet of Originating IP address*
*A fragment of your IP address. This can be used to identify your ISP, but not you personally.
What Kind of Logging is Unacceptable?
Virtual Private Networks are privacy tools above all else. For this reason, there are certain types of data that should not be collected under any circumstances.
Avoid any VPN service that records the following data:
- Browsing activity
- Originating IP Address
- Assigned VPN Server IP Address
- Individual Timestamps*
- Individual Bandwidth Usage*
- DNS Queries
*This type of data is only dangerous if logged in combination with other detailed connection data.
Popular VPNs That Keep Activity Logs
The following VPN services log your browsing history and activity data. This is the most egregious form of logging and should be avoided at all costs.
This is by no means an exhaustive list of all VPNs that keep activity logs. You should always personally check your provider’s policy before trusting them with your data.
| Provider Name | Data Logged | Storage Time |
|---|---|---|
| Hola Free VPN |
|
“As long as necessary” |
| McAfee Safe Connect |
|
“As long as necessary” |
| Psiphon |
|
90 days |
| VPN99 |
|
5 years |
*Collected by default through the ‘report operational errors’ feature within the application.
What Are the Reasons for VPN Logging?
There are lots of valid reasons a VPN provider might maintain some basic logs. This could include the following:
1Bandwidth Limits
Free or ‘freemium’ VPNs often impose caps on the amount of data a user can transfer within a given time period. Limiting the amount of bandwidth used by a specific account obviously requires a degree of logging.
While this type of logging isn’t typically an issue, if a VPN claims to be completely ‘zero logs’ but also imposes bandwidth limits, it’s likely their claims aren’t entirely true.
2Device Limits
Limiting the number of devices used per account is one of the most common reasons for maintaining logs. Enforcing these restrictions will almost always require some form of temporary logging, at least during each VPN session.
Exactly how each provider enforces its device limits is subjective. Some privacy policies are transparent about logging the number of simultaneous connections per account. By contrast, some ‘no-logs’ VPNs impose device limits without explaining exactly how.
NordVPN is a great example of a VPN going the extra mile to protect user privacy despite enforcing device restrictions. Rather than storing user connection data, NordVPN relies on a unique algorithm to keep track of simultaneous sessions:
“To limit the number of simultaneous sessions of an active user, an algorithm keeps their username and the timestamp of the last session status while the session is active. This data is wiped within 15 minutes after the session is terminated.”
3Virtual Private Servers
To save on costs, some VPN services rent Virtual Private Servers (VPS). These are significantly cheaper than dedicated physical servers, especially in countries without strong digital infrastructure.
While this might reduce a VPN provider’s overheads, it can be problematic in terms of privacy.
Rental servers can maintain logs of activity regardless of the VPN company’s logging policy. Depending on the jurisdiction of the rented server, local authorities could compel the server host to log or share this data.
In this case, the logging policy of the VPN company is redundant. Local authorities can go directly to the server host to find the information they need.
This problem was demonstrated in 2014 when an EarthVPN user was arrested in the Netherlands. Despite EarthVPN’s no-logs policy, the relevant authorities compelled the virtual server host to hand over the data needed to identify their suspect.
4Legal Obligations
National intelligence agencies like the NSA and GCHQ have the power to force organizations to log and share private information. Given the scope of their bulk surveillance programs, targeting a particular company or server network is particularly easy.
These logging requests may be accompanied by a gag order, which makes it illegal for the company to publicly disclose what they’re being compelled to do. Some VPN companies publish warrant canaries in an attempt to tackle this problem.
For more information on warrant canaries, mass surveillance, and how a VPN’s location might affect your privacy, read our guide to VPN Jurisdictions.
5Performance Optimization
Maintaining a fast, private, and reliable VPN service doesn’t necessarily require logging, but it definitely helps. Basic connection data can help in selecting the most appropriate server to connect to, or allocating resources to the most popular server locations.
Many VPN providers use performance optimization to justify extensive and invasive logging practices. It’s important to be aware that in most cases, anything above basic connection data is not necessary to maintain a well-performing VPN network.
The Problem with VPN Logging Policies

Unsuspecting VPN users are commonly misled by vague, false, or deliberately confusing logging policies designed to create the illusion of privacy.
If you don’t know what to look for, you could end up using a VPN service that puts you at risk.
If you’re assessing a VPN’s privacy policy or investing in a subscription, you should be aware of the following common problems.
If you’re already familiar with these issues, you can skip straight to How to Protect Yourself.
1False Advertising
With the exception of independent auditing, it’s almost impossible to truly verify a VPN’s logging policy until it’s too late.
To prove this point, there are several examples of supposedly ‘private’ or ‘no logs’ VPN providers that have been caught sharing detailed logs with authorities.
In 2011, London-based VPN service HideMyAss (HMA) played a key role in the arrest of Cody Kretsinger, a 23 year-old Phoenix resident. Kretsinger was a member of LulzSec, a spin-off of the hacker-activist group Anonymous.
HMA claimed to be a privacy-first service that allowed users to “surf anonymously online in complete privacy”:
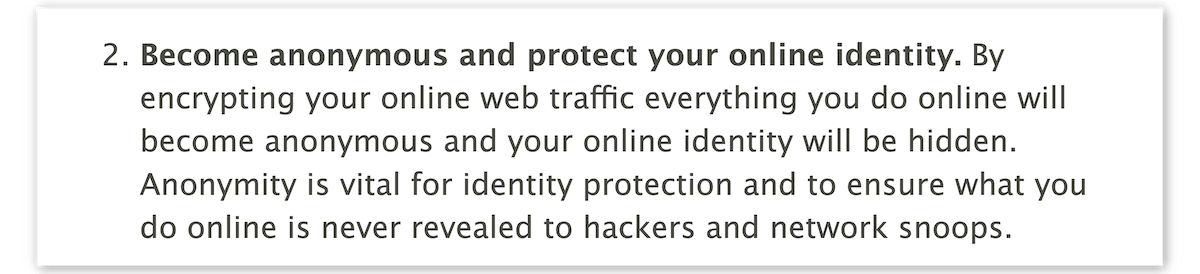
Screenshot from an archive of HideMyAss’s homepage, July 18th, 2011.
The FBI traced Kretsinger’s hack to an IP address owned by HMA, and promptly issued a UK court order demanding logs. HMA complied and shared the connection logs that eventually identified Kretsinger.
While it is clear that illegal activities should not be condoned under any circumstances, this incident is just one example of a serious flaw in the VPN ecosystem. Selling a product that explicitly claims to protect a user’s identity and then doing the opposite is undeniably deceptive.
HideMyAss isn’t the only VPN with a history of false advertising — IPVanish also has a troubled past when it comes to data logging.
In 2016, IPVanish cooperated with the FBI to assist with a criminal investigation. Despite a privacy policy that was explicit about its zero-logging practices, IPVanish ultimately conceded to legal requests and provided detailed connection data to authorities.

Screenshot from an archive of IPVanish’s privacy policy, March 13th, 2016.
While this is obviously concerning, it’s important to note that this incident occurred while the company was under entirely different ownership and management. For more information on this case, you can read our full IPVanish review.
It’s likely that there are many more examples of supposedly ‘no-logs’ VPNs sharing data with authorities or making false claims that we will simply never know about. As it stands, it’s important to look into your provider’s history before making a decision.
2Deliberate Ambiguity
In an ideal world, all VPN logging policies would clearly explain what data is kept during and after a VPN session. Unfortunately, many providers rely on ambiguity to help create a false sense of security.
Most users don’t realize that broad phrases like ‘no-logs’ aren’t always what they seem. Some VPN providers take advantage of the fact that there is no standard definition of ‘logs’ across the entire industry.
This loophole allows VPN services to avoid explicitly stating what type of data their ‘no logging’ claims refer to.
A provider might legitimately advertise ‘no-logs’ for activity data, but continue to record personally-identifiable connection data.
Put simply, many VPN providers are labeling themselves as ‘no logs’ by their own standards alone.
While some connection logs are not necessarily bad, making false or contradictory statements only adds to the confusion and distrust when selecting a VPN.
In a similar vein, it’s fairly common for a VPN’s marketing claims to directly contradict its privacy policy. Typically, they will make a bold ‘zero-logging’ claim on the homepage, and then carefully disclose the data they actually keep in the terms and conditions.
ThunderVPN provides a great example of these tactics. The company clearly advertises a “strict” no-logging policy on its Google Play Store listing:
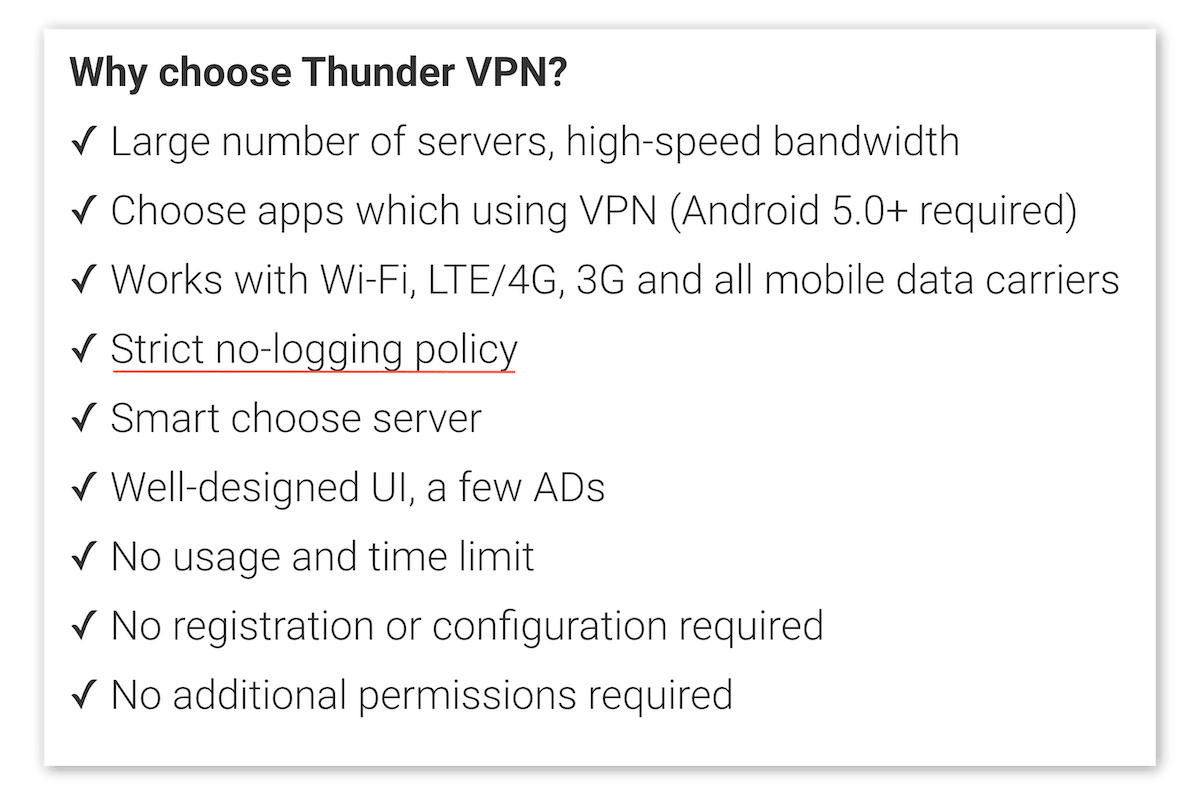
Screenshot from ThunderVPN’s Google Play Store listing.
However, a quick read of its privacy policy proves this to be completely untrue:

Screenshot from Thunder VPN’s privacy policy.
Not only are these practices dishonest, they’re potentially dangerous for unsuspecting VPN users that haven’t read their provider’s policy in full.
If you find a VPN that makes contradictory or misleading statements about its logging practices, it’s sensible to think twice about its trustworthiness. In most situations, it’s unlikely to be a VPN you should trust with your sensitive data.
3Lack of Detail
It’s surprisingly common for less popular VPN providers to operate without a privacy policy at all. Needless to say, if there are no details about data collection on the provider’s website, the VPN should not be trusted.
Similarly, look out for unusually short policies. Lots of providers simply state:
“We do not log any of your activity while connected to the VPN service”
These statements explain nothing about how your data might be collected in other ways.
Yoga VPN’s privacy policy is a good example of what to avoid. At just 371 words long, the entire document barely explains a single thing about how Yoga VPN operates.
Some services are also worryingly vague about how the terms of service are enforced. Dozens of providers boast about ‘no-logs’ but also warn users that they will “investigate suspicious behavior” or “ban abusive users” in the same sentence.
The question then stands: if a VPN does not log your IP address or activity, how are they able to investigate suspicious behavior?
If a VPN’s logging policy is short or vague, contact the provider’s support team for more details. Don’t use a product that’s not willing to invest the time to be clear and transparent about its practices.
4Jurisdiction
Logging policies and jurisdictions are closely intertwined. While obscure jurisdictions can be great for privacy, they can also cause issues in terms of accountability.
It’s much harder to hold a remote business accountable for violating false advertising laws or deceiving customers. If a VPN in Panama deliberately misleads a customer in Germany, there’s not a lot that can be done.
More importantly, a VPN provider’s jurisdiction will affect its legal obligation to log data and share it with authorities. A service based in the US, for example, could be compelled to monitor its users in secret.
These invasive jurisdictions are less of an issue if a VPN is truly no-logs. However, choosing a service outside of these countries may offer more protection.
To learn more about data sharing amongst the five, nine, and 14 eyes alliances, read our VPN Jurisdictions guide.
How to Protect Yourself
If you’re concerned that your VPN might not be fully protecting your privacy, there are several steps you can take to further safeguard your sensitive data.
1Choose a Verified No Logs VPN
There have been several instances where legal cases and real-world events have verified a VPN provider’s zero-logging policy.
Services like ExpressVPN and Private Internet Access have had their servers seized and been unable to cooperate due to a lack of retained data. What’s more, both providers have had their logging policies verified by third party auditors.
Other VPN providers that successfully passed an independent audit include:
- Hide.me
- PIA
- IVPN
- Mullvad VPN
- Surfshark
- IPVanish
If you’re concerned about VPN logging, it’s safer to choose a VPN with a proven record.
2Combine a VPN with Tor
If configured correctly, using a VPN in combination with the Tor browser can move you a step closer towards anonymity.
It’s worth remembering that the Tor browser is slow at the best of times. Combining a VPN with Tor will considerably reduce your VPN’s performance and connection speed.
3Layer VPN Services
Using multiple VPN services concurrently will add another layer of protection to your identity.
The simplest way to do this is to set up a VPN router and connect your device. Install a VPN from a different provider on the same device and then run the application. You will then be passing your data through both providers simultaneously.
Just like using a VPN in combination with Tor, layering multiple VPN services will have a considerable impact on performance.
4Choose a Privacy-Friendly Jurisdiction
Subscribing to a VPN based outside of key intelligence-sharing countries is the safest option.
Remember that operating outside of these invasive jurisdictions doesn’t necessarily mean a VPN provider can be trusted. The VPN company could still cooperate with foreign authorities and even log your data if they are so inclined.
Don't Be Afraid to Ask Questions
VPN logs aren’t always a bad thing. Ultimately, their importance depends on the level of anonymity you’re looking to achieve.
The main issue, however, is a widespread lack of honesty and transparency. A legitimate VPN provider will leave you with absolutely no doubt that your personal information is in safe hands.
If you see that the claims on a provider’s homepage do not align with its privacy policy, take your money elsewhere. If something looks ambiguous or suspicious, don’t hesitate to contact the provider’s support team.
The key is to understand exactly how VPN services can manipulate their policies. Once you have a solid understanding, you can then look for honest providers and take extra precautions if you need higher levels of anonymity.
With your privacy at stake, it’s your right as a user to expect transparency at the very least.


