Top10VPN is editorially independent. We may earn commissions if you buy a VPN via our links.
The Best Free & Paid No-Logs VPNs
Our Verdict
Private Internet Access (PIA) is our top recommendation for no-logs, with a rating of 9.3/10. It collects zero connection or activity logs, has a diskless server network, and its zero-logs policy has been proven multiple times by independent auditors, in court, and via a server seizure.

It’s almost impossible to tell whether a VPN that calls itself no-logs actually collects no logs. Sadly, many VPNs claim to not keep logs just to convince you to buy their product.
The best way to find out if a VPN is truly no-logs is to pick apart its privacy policy and terms of service, evaluate its server infrastructure and jurisdiction, and find out whether its servers have been seized in the past.
That’s why we’ve spent over 50 hours collecting, analyzing, and assessing the very best no-log VPNs to find out which are the most private and won’t collect identifiable data.
Summary: The Best No-Logs VPNs
Based on our privacy tests, the best no-logs VPN services are:
- Private Internet Access: Best No-Logs VPN Overall
- ExpressVPN: Alternative No-Logs VPN
- Perfect Privacy: Zero-Logs Runner-Up
- Proton VPN Free: Best Free No-Logs VPN
Why Trust Us?
We’re fully independent and have been reviewing VPNs since 2016. Our advice is based on our own testing results and is unaffected by financial incentives. Learn who we are and how we test VPNs.
| VPNs Tested | 62 |
| VPN Logging Policies Analyzed | 50 |
| Total Hours of Testing | 30,000+ |
Comparison of the Best No-Logs VPNs
In the table below, you can compare the top four no-logs VPNs based on their logging policies, real-world history, jurisdiction, and more:
In the rest of this article, we’ll explain what no-logs VPN actually means, reveal which VPNs log your data, and why VPN services collect logs in the first place.
We’ve also collected data on the privacy policies of 70 VPNs to find out which collect your IP address, DNS requests, and more.
EXPERT ADVICE: To protect your online anonymity, install Private Internet Access, sign up with a throwaway name, email account, and pay using gift cards or Monero.
Detailed Analysis of the Best No-Logs VPNs
In our research, we only found five VPNs with genuine zero-logging policies that had been certified by real-world events, such as a subpoena or server seizure.
When choosing the best three, we considered which had regular third-party audits of their logging policies, which had diskless servers, and whether the VPN jurisdiction was privacy-friendly.
Here’s an in-depth table showing the exact data that each of these no-logs VPNs records:
You can see the full results of our tests in our detailed results table.
1. PIA VPN: Best No-Logs VPN Overall
Ranked #1 out of 62 VPNs for No-Logs Policy
Private Internet Access (PIA) is the best no-logs VPN, despite its US jurisdiction. Its zero-logs policy has been proven multiple times both in court and via a server seizure.
PIA VPN is not only the top VPN for privacy, but it’s also the overall best VPN for anonymous torrenting and accessing the dark web.
But, as with all other VPNs, there has to be a minimal amount of data collected in order to provide a quality VPN service. In this case, PIA must collect some account information: your email address, payment data (immediately deleted), and your territory or zip code.

PIA’s Privacy Policy confirms it doesn’t collect your browsing history, IP address, or connection timestamps.
We believe this amount of data collection is justified, as you wouldn’t be able to open an account or request a refund without it. Additionally, you can sign up with a throwaway email address and use gift cards to pay anonymously.
No-Logs Policy Proven in Multiple Real-World Cases
In July 2016, the Russian government seized PIA’s servers after a new privacy data law was passed that demanded all VPNs must log Russian traffic for up to a year. In response, PIA completely shut down its Russian servers and quit the country.
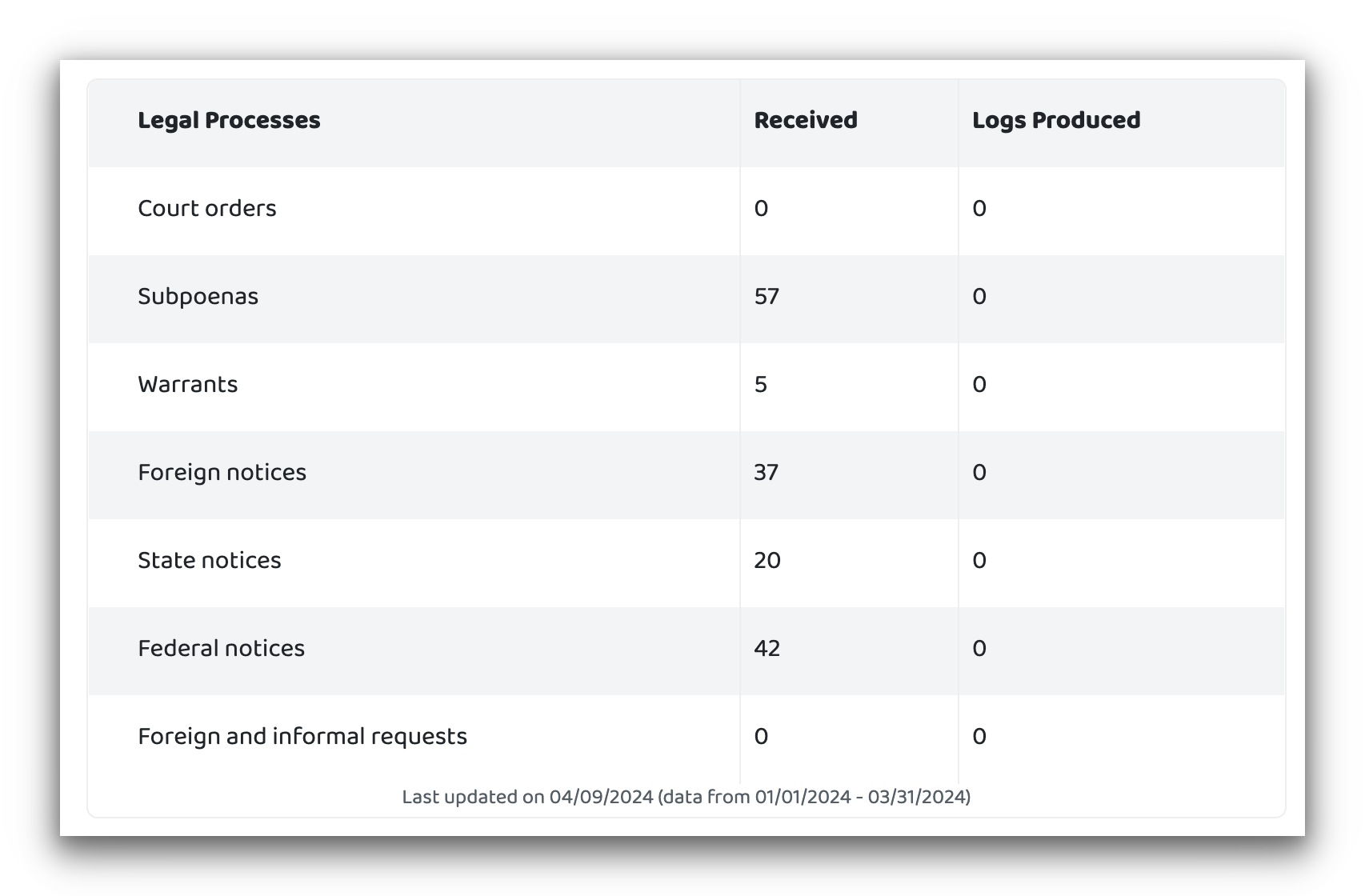
PIA’s transparency report verifies that it’s never provided logs for a court order, subpoena, or a warrant.
More recently in 2018, PIA was subpoenaed by the FBI but was again unable to provide any logs. What’s more, there was no record of the defendant even signing up for PIA as there was no applicable email address or payment information.
Diskless Server Network & Advanced Privacy Settings
PIA operates self-owned DNS servers, preventing exposure of your DNS traffic to third parties, and diskless VPN servers.
These servers are configured to routinely reboot, meaning all data is permanently deleted on a regular basis.
All of PIA’s apps come with advanced privacy and security settings you can easily configure. The video we recorded below shows the options available within the desktop app:
Easily changing privacy and security settings in the PIA VPN desktop app.
PIA’s advanced features include an effective VPN kill switch, split tunneling, malware blocker, and shadowsocks proxy.
Questionable No-Logs Audit
PIA has has had two successful no-logs audits in the past with Deloitte Romania – one in 2024 and one in 2022. But we’ve found some red flags that they might not be as in-depth as other audits.
We’re disappointed to see the 2024 audit seems to be a copy of the 2022 audit, with minor changes and updates to formatting. Half the audit is an index provided by PIA, and not insightful investigation into the VPN’s implementation of a no-logs policy.
In addition, you have to be a paying PIA customer to easily find the document – as there wasn’t a link in the website announcement. It’s common practice for VPNs to release audits on their websites for all readers and customers to view.
It’s important to keep in mind, though, that PIA has proven itself to be no-logs in a random server seizure. This is the strongest evidence a VPN can have that it’s no-logs. Nonetheless, we’d like to see PIA conduct a high-quality audit next time.
US Jurisdiction & Owned by Kape Technologies
There are two main drawbacks to PIA. Firstly, it’s based in the US. The US is one of the worst jurisdictions for privacy because it’s part of the Five Eyes data sharing alliance and state surveillance.
Secondly, PIA was acquired by Kape Technologies in 2019, previously Crossrider. The company was previously discovered to be infecting Windows and macOS systems with adware. Adware is a form of malware that shows you pop-up adverts for software and services.
But Crossrider shut down its ad platforms in 2016 and re-branded to Kape Technologies in 2019. We’ve since seen no reason to question the legitimacy or business practices of Kape Technologies.
Ultimately, you’re safe using PIA for general-purpose computing, such as protecting your data on public WiFi and bypassing streaming service geo-blocks.
But if you’re a journalist or a political dissident, you might prefer a smaller company like Perfect Privacy or Mullvad.
2. ExpressVPN: Alternative No-Logs VPN
ExpressVPN is a virtually no-logs VPN that’s extremely user-friendly and well-designed.
We call it “virtually no-logs” because it collects anonymous server usage data. But since this data is not personally identifiable, it’s still classified as a no-logs VPN.
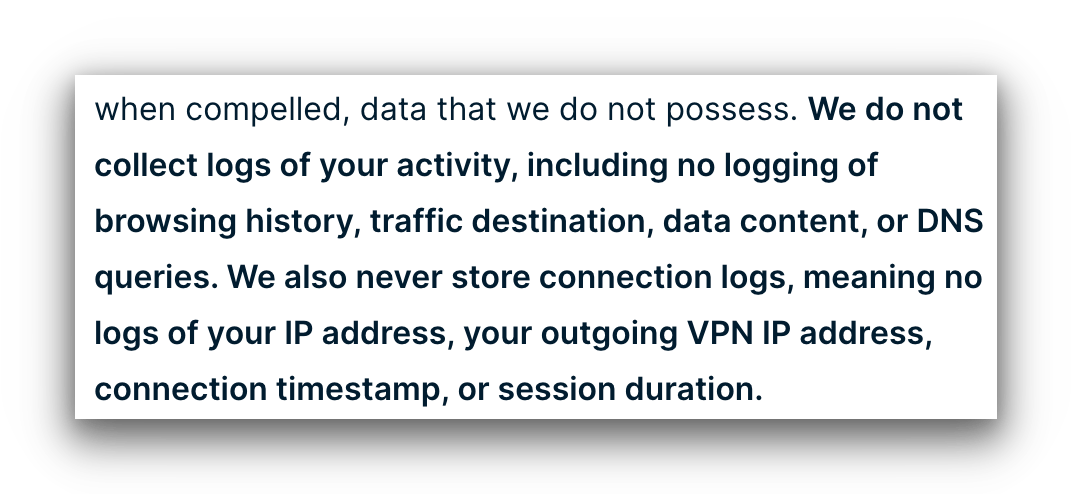
ExpressVPN’s privacy policy clearly lists what information it doesn’t collect from a user.
The VPN service is also based in a privacy haven, the British Virgin Islands (BVI), a self-governing territory that has strict laws protecting the privacy of individuals and businesses.
The BVI are also an excellent location for a VPN because they are not part of any data sharing alliance (such as Five Eyes or EU). Other countries’ authorities aren’t able to force the BVI government to hand over any data collected in the jurisdiction.
Investigation Proves ExpressVPN Is No-Logs
In 2017, ExpressVPN’s servers were seized by Turkish authorities investigating the death of the Russian ambassador, Andrei Karlov.
However, the authorities were unable to find any personal information about the individual on ExpressVPN’s servers, proving ExpressVPN to be a genuine no-logs VPN service.
This stands in stark contrast to other VPNs, such as PureVPN and HideMyAss, which have cooperated with law enforcement and handed over personal information that lead to arrests of their users.
Very Easy-to-Use on All Devices
While PIA VPN is better for slightly more advanced VPN users, ExpressVPN is ideal for beginners. In our experience, it’s the easiest anonymous VPN available.
All of the VPN service’s apps benefit from a well-designed user interface (UI) across all popular platforms.
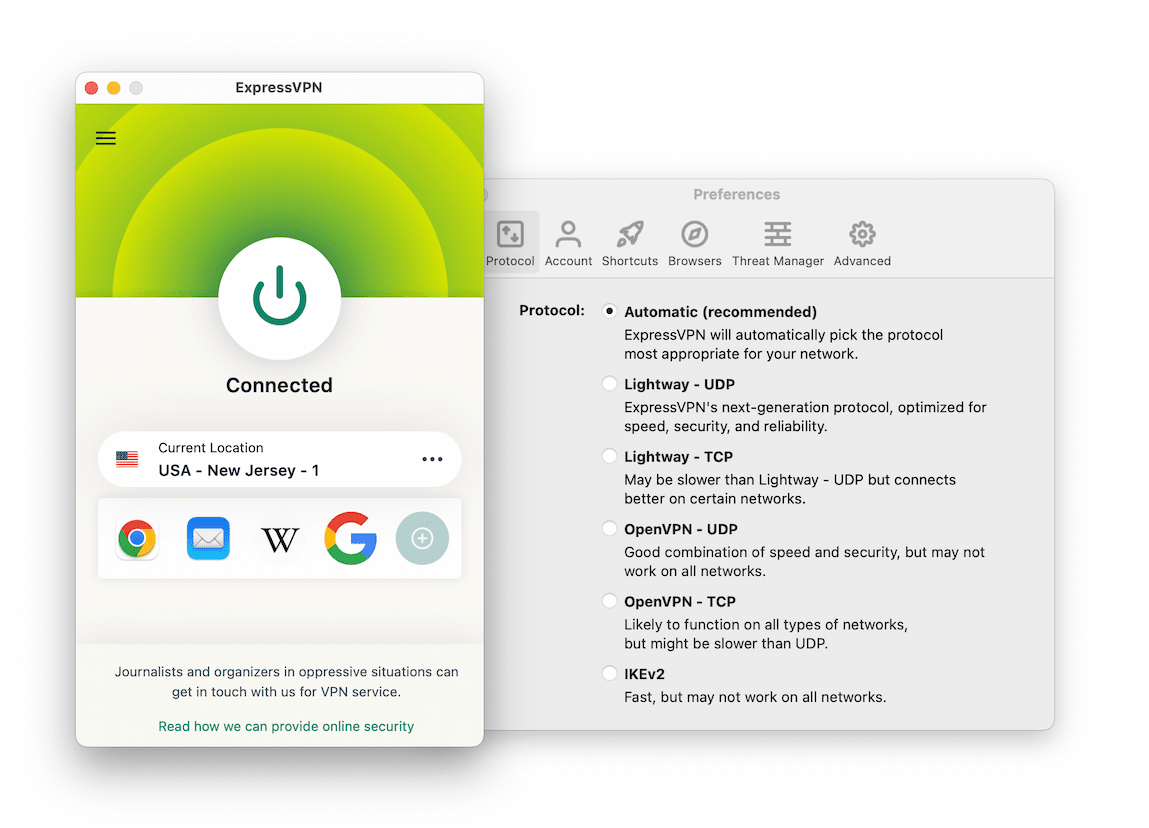
It’s easy to change settings and servers in ExpressVPN apps.
There aren’t as many customizable settings as with Private Internet Access, but ExpressVPN does offer all key privacy features, including a VPN kill switch on all platforms as well as IPv6 and WebRTC leak blocking.
A Great VPN for Anonymous Streaming & Unblocking Geo-Restricted Videos
Being no-logs isn’t ExpressVPN’s only benefit: it’s also extremely fast and one of the most reliable VPNs for anonymous streaming.
For instance, Kodi users will find it very easy to stream anonymously using the VPN’s highly secure and user-friendly Fire TV Stick app.

ExpressVPN streams US streaming sites from anywhere.
ExpressVPN is also extremely effective at unblocking geo-restricted streaming services. It works with 18 international Netflix libraries, HBO Max, Disney+, Hulu, BBC iPlayer, and more.
Expensive & Owned by Kape Technologies
With its best price at $6.67 per month, ExpressVPN’s subscription is more expensive than the average VPN.
However, we believe it’s still good value for a private VPN that offers IP and DNS leak protection, access to all major streaming services, and Diskless servers in 106 countries.
Similar to PIA, another potential drawback for those skeptical of big business is that ExpressVPN was acquired by Kape Technologies in 2021.
However, ExpressVPN continues to operate independently and there’s no evidence that it doesn’t provide the same level of privacy protection as it did before the acquisition.
3. Perfect Privacy: Zero-Logs Runner-Up
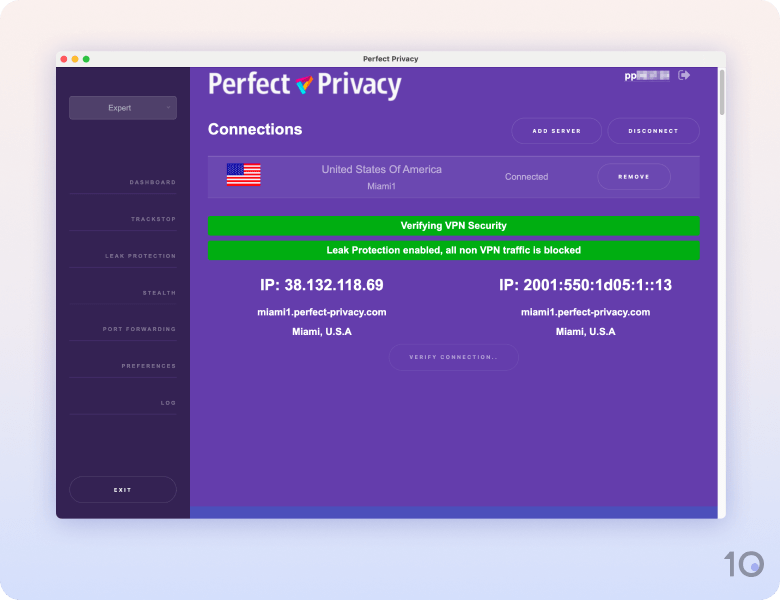
Perfect Privacy is owned by a small company in Switzerland, which stands in contrast to PIA and ExpressVPN. Its privacy policy confirms that it doesn’t collect “IP addresses, access time or duration, nor bandwidth caused by individual users.”
It also clarifies that it does save “general server information in its website” but doesn’t record any individual usage. This means it can never be linked back to a user.
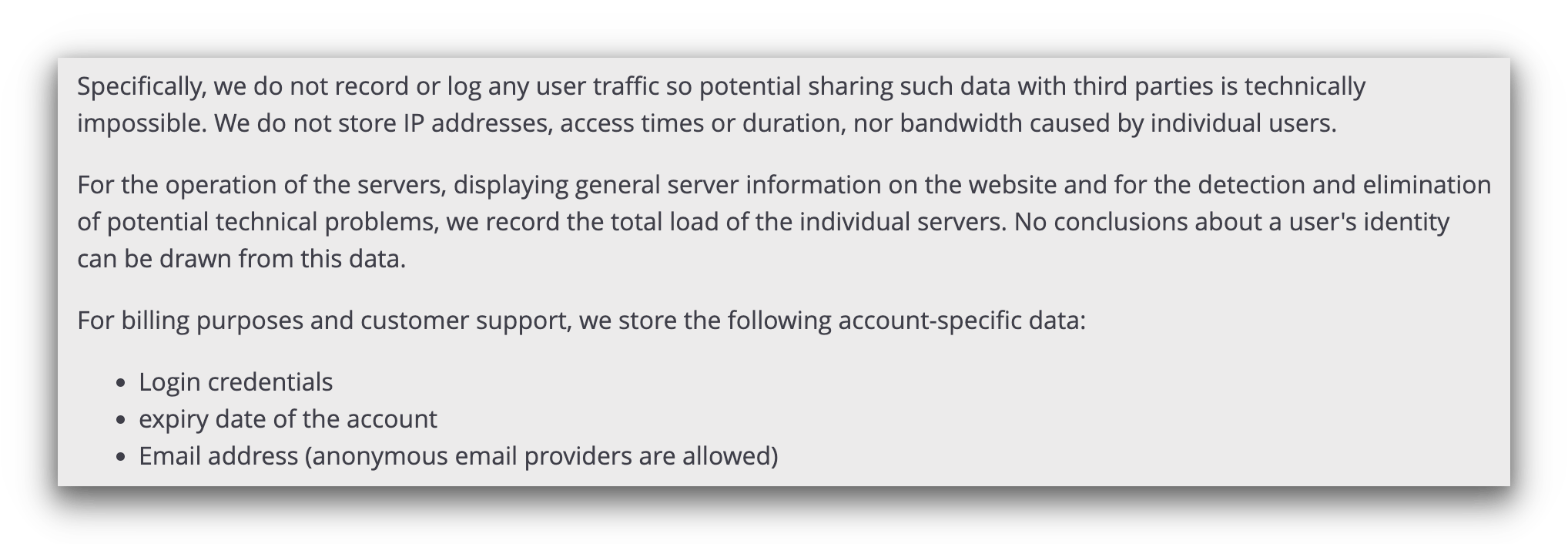
A screenshot of Perfect Privacy’s privacy policy that shows it doesn’t keep any activity logs, but does collect some personal information for billing.
Perfect Privacy’s no-logs policy even suggests that you can use an anonymous email provider to open an account. You can also pay using Bitcoin, which can be more difficult to trace.
Perfect Privacy Is a Proven No-Logs VPN
Perfect Privacy’s no-logs policy was put to the test in September 2016 when Dutch authorities seized two of Perfect Privacy’s Rotterdam servers.
Fortunately “no customer information was compromised due to the seizure” because Perfect Privacy keeps no logs and all the information was fully encrypted.
Diskless Servers & Excellent Security Features
Perfect Privacy has an entirely RAM-based server network which can be trusted to erase any data stored if there’s ever a server seizure.
It also offers a unique proprietary routing algorithm called Neurorouting. This novel feature ensures that your traffic stays encrypted for as long as possible.
However, Neurorouting is only available on Windows — frequent macOS or mobile users might prefer to use ExpressVPN, which has intuitive and easy-to-use apps on all platforms. In comparison, Perfect Privacy’s apps are much less attractive.
Perfect Privacy also offers an effective kill switch, multi-hop VPN servers, an ad blocker, and includes port forwarding in its subscription.
The suite of security features offered by Perfect Privacy is great for advanced VPN users, but can be intimidating to a complete beginner.
Perfect Privacy Is Expensive & Hasn’t Been Audited
Despite its merits, Perfect Privacy has some serious flaws that prevent it from being a VPN we would recommend to all users.
Firstly, it hasn’t been independently audited. We feel this isn’t too much of an issue, though, as its no-logs claims have been proven in a server seizure. Nevertheless, it’s good to show commitment to continued security by implementing audits.
Secondly, at $8.95 per month, it’s expensive in relation to other VPNs. To compare, Surfshark has a cheaper subscription with diskless servers, unlimited device connections, and is better than Perfect Privacy for streaming.
Lastly, Perfect Privacy has a very small server network, relatively slow speeds, and doesn’t unblock Netflix. Though the VPN service excels in privacy and security, it fails to impress in many other areas.
4. Proton VPN Free: Best Free No-Logs VPN
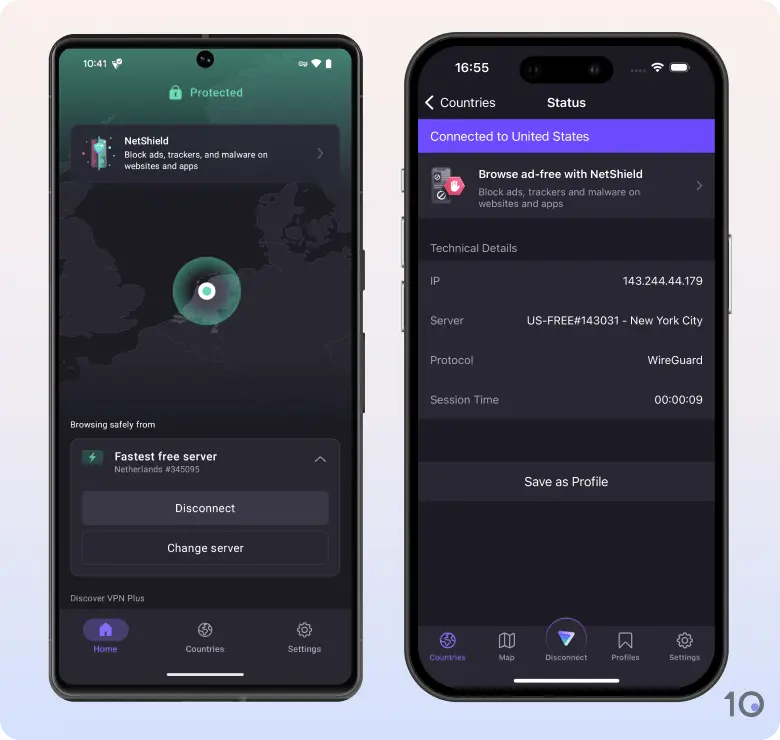
Out of the 62 we’ve tested, Proton VPN Free is the most private free VPN we’ve reviewed. It outperformed other strong free VPNs like Windscribe, Hide.me, and PrivadoVPN in our privacy tests.
Proton VPN does not log any user data, and its Swiss jurisdiction means that it doesn’t have to abide by any data retention laws, either.
In addition to its no-logs status, Proton VPN Free delivers fast speeds on nearby connections, has uncapped data (which is rare among safe free VPNs), and doesn’t require you to enter payment details upon signup, either.
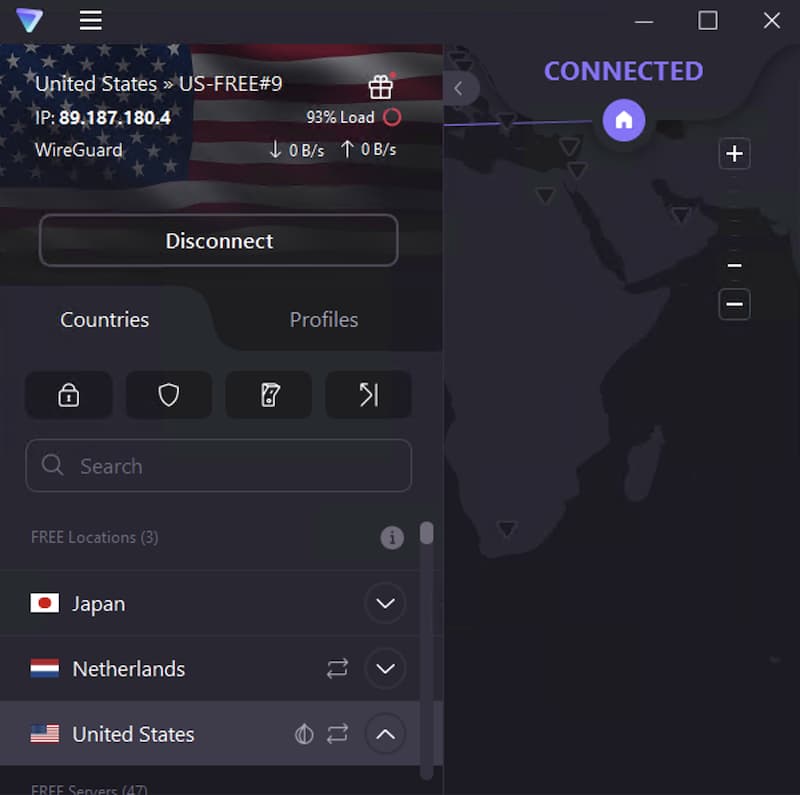
Proton VPN’s free server list on Windows.
The free version of the software has almost the exact same privacy policy as the paid version — a robust no-logs policy that has been independently audited and verified in a legal case. As its warrant canary states:
A data request from a foreign country was approved by the Swiss court system. However, as we do not have any customer IP information, we could not provide the requested information and this was explained to the requesting party.

The only difference in privacy policy between the free version is the detection and blocking of BitTorrent traffic using the nDPI library, or deep packet inspection, in order to reduce server congestion.However, we aren’t so worried as the 2022 independent audit concluded: this “does not affect the privacy of their users” as “the packet content (e.g. a torrent name) is not being analysed or logged.”
Proton VPN Free has many of the privacy features we look for in a VPN, including a working kill switch, DNS and IPv6 leak blocking.
The free VPN’s biggest flaw is its very limited range of free server locations. It’s only got three — the Netherlands, Japan, and the US.
Other VPNs We Considered
There are many high-quality VPNs that claim to be no-logs, even backed up with in-depth audit results and extensive online resources on digital privacy. We assessed over 62 of these VPNs when choosing our recommendations.
However, there are very few VPNs that have been actually verified by real-world cases, such as law enforcement seizing servers or hackers exposing customer data.
Some of these VPNs haven’t made the list simply because they’ve avoided these circumstances.
Here’s some of the most private VPNs that haven’t been proven no-logs in real-world cases, but still have extremely strong no-logging policies, anonymous payment methods, and AES-256 encryption.
NordVPN
NordVPN isn’t as private as its rivals.
What we do like:
NordVPN’s privacy policy is regularly audited by a third party to prove its validity. It’s also implemented diskless servers, which make sure that no data is saved onto a physical server and is instead deleted permanently.
NordVPN is based in Panama, a privacy-first nation. It publishes regular transparency reports, and it also offers Bitcoin as an anonymous payment method.
What we don’t like:
NordVPN takes your email address and payment data upon signup if you use a credit card, which is common among VPNs and can be avoided by providing a fake email address. It also logs your connection timestamp for 15 minutes after a session ends.
NordVPN’s Threat Protection feature makes sure you don’t save any harmful malware onto your device, but the “scanned files are stored and used to improve NordVPN.”
You can disable this feature, and files aren’t tied to any specific user, but we’d prefer these files to be deleted immediately after being scanned for malware.
IVPN
IVPN’s no-logs policy hasn’t been proven in court or server seizure.
What we do like:
IVPN doesn’t require an email for signup, instead you receive a random identifier. You can pay using cash or cryptocurrencies.
It’s based in privacy-friendly Gibraltar, is transparent in its ownership, and it publishes a regular warrant canary and independent audit to verify its no-logs policy. All of IVPN’s code is also open-source and available on GitHub to scrutinize.
What we don’t like:
IVPN doesn’t have diskless servers and the no-logs policy hasn’t been tested in a real-world case, so we can’t be 100% sure it’s truthful. It’s also got a relatively small server network of only 29 countries.
Additionally, IVPN automatically saves device information on mobile for crash logs.
Mullvad VPN
Mullvad is based in the EU and doesn’t publish third-party logging policy audits.
What we do like:
Mullvad doesn’t ask for your email address when you sign up – similar to IVPN, it gives you a unique account number. Mullvad’s server network, including VPN and private DNS servers, are all completely diskless.
It doesn’t save any activity logs of its users and offers PGP email communication.
Mullvad also offers anonymous payment methods, such as cryptocurrencies and cash, so you won’t be traced by your credit card details. The VPN service offers multi-hop servers, SOCKS5, and an automatic kill switch.
What we don’t like:
Mullvad is based in the EU, which means it has to adhere to General Data Protection Regulation law (GDPR). It also hasn’t completed a third-party audit on its privacy policy or implemented transparency reports.
How We Test & Rate No-Logs VPNs
Unfortunately, you can never really know when a VPN is recording your data. There always has to be an element of trust when using a service that could have access to your credit card information, browsing history, and IP address.
However, we’ve identified the best VPN services that claim to be no-logs and put them through our rigorous testing methodology to determine whether they are truly no-logs, and whether they are worth a subscription.
In the table below, you can compare how the top VPNs performed in each of our testing categories:
Here’s a more detailed explanation of our methodology and review process:
1. Real-World Case: 30%
Real-world cases are the most reliable way to tell if a VPN is lying about its logging policy. It’s also an efficient way of assessing whether the security of a VPN’s server infrastructure and software is adequate.
Unfortunately, it’s only when a server has been seized by a third party, hacked, or requested in legal proceedings and information is leaked, that we can know if the server ever stored information about its users.
2. Privacy Policy: 30%
Our experts analyzed and dissected the privacy policies of 70 VPNs in order to identify which were actually no-logs, and which were claiming to be while storing information.
All the no-logs VPNs we recommend truly do not store any logs, by which we specifically mean: no activity or connection logs.
However, this doesn’t mean absolutely no information is kept about the user. Our definition of no-logs includes VPNs that store personal information (an email address, username, password, and any payment information provided) and aggregated anonymous logs.
Personal information is included because virtually all VPNs collect this information in order to open an account or issue a refund to a user. Whereas, aggregated and anonymous logs cannot be used to identify any single user, meaning your data is safe.
3. Logging Policy Audit: 10%
Besides real-world cases that prove a VPN’s no-logs policy, there’s also verification through independent audits performed by third-parties, such as Deloitte and Cure53.
It’s important to differentiate between server or software audits and a logging policy audit. The latter is what we want a VPN to do in order to prove it’s following a no-logs policy.
In comparison, a software or server infrastructure audit only analyzes a small section of the service and can’t fully determine whether a VPN is no-logs.
4. Diskless Servers: 20%
Diskless servers are incredibly rare among VPNs because they cost a lot of money and require a considerable amount of time to set up.
But they are the best way to ensure that your data isn’t saved onto a hard drive, which could then be exposed.
Surfshark announced in a blog post in 2020 that it had introduced diskless servers.
With RAM servers, when a session or process is terminated, any data associated with it is permanently deleted. This way, it’s almost impossible for government agents or anyone else to seize the server and retrieve information like they could with a physical VPN server.
Basically, it’s almost a guarantee that the no-logs policy is being adhered to as it’s hardwired into the servers.
5. Jurisdiction: 10%
Where a VPN is incorporated will affect its legal obligation to log and store data, or even share it with governmental authorities.
For example, a VPN based in the US could be compelled by the government to record user data. The US is part of the Five Eyes international intelligence sharing alliance, which puts your data at risk of being passed from the US to another country’s authorities.
In contrast, a VPN based in the British Virgin Islands benefits from having complete sovereignty over its data privacy legislation.
However, a watertight no-logs policy that’s been independently audited and verified in a real-world case can overrule a bad jurisdiction.
VPNs to Avoid: Popular VPNs that Log User Data
A secure, no-logs VPN will boost your online privacy. But a VPN that logs your connection data and has a poor technical infrastructure will put your data at risk of leaks and could even be sold to advertisers.
Read on for a shortlist of VPNs that log your data and that you should absolutely avoid. We also have a detailed table showing all the user data logged by the top VPNs.
1. Hola Free VPN: A Dangerous Proxy That Logs Your Data
Despite VPN being in the name, Hola Free VPN is actually an insecure peer-to-peer proxy network that doesn’t provide any encryption whatsoever.
Hola Free VPN’s privacy policy also states that it may log your activity logs and connection logs, which is more than enough information to identify you and your online activity.
Even worse, Hola VPN doesn’t even specify for how long it’ll store the information collected. It might be for months or even years.
2. Yoga VPN: Unsafe VPN that Has a Vague Privacy Policy
Yoga VPN is simply one of the worst VPNs we’ve reviewed. Its privacy policy is extremely short and vague.
Ironically, Yoga VPN’s privacy policy used to be hosted on a website called Pastebin. It’s a site popular with hackers for sharing stolen data, as you don’t need to create an account to share documents.
The privacy policy is now hosted on Yoga VPN’s own website, but it’s still the exact same text and even in the same font.
Overall, we don’t recommend downloading Yoga VPN. Beyond its questionable privacy policy, it’s also based in Hong Kong and has links to the Chinese government.
3. SkyVPN: Invasive Logging Policy & Has Links to China
SkyVPN logs your original IP address, new IP address, websites you visit, device information, location information, a list of apps on your device, and “other technical information about your device.”
Not only is the logging policy somewhat vague on what information it collects, while also admitting to the fact it collects way too much information to be anonymous, it also doesn’t clarify for how long it actually stores that data.
Lastly, it’s based in Hong Kong and has hidden links to Chinese ownership. Our extensive research into free VPN ownership in China flagged SkyVPN as a Chinese entity, but it was extremely difficult to find this information.
What Does “No-Logs” or “Zero-Logs” Actually Mean?
A no-logs or zero-logs VPN is a provider that doesn’t log any identifiable data that can be used to track your online activity.
The no-logs claim – or a ‘no-logging policy’ — can be misleading, as it implies that absolutely no data is stored at all. But all VPN services have to collect at least some amount of data to provide customer support, maintain device limits, collect subscription payments, and issue refunds.
Moreover, some VPNs claim to be no-logs but implement cookies in their website that track your browsing activity (such as when you click buttons, purchase a subscription, or log in).
In short, each VPN that defines itself as no-logs actually has a different interpretation of what that actually means.
We explain what VPN logs are, and which types of logs actually matter, in the video below:

This is why you should always read through a VPN’s privacy policy and terms of service before buying a subscription to make sure you’re aware of its real logging practices.
EXPERT TIP: When researching a VPN’s privacy policy, look out for these three things:
- What types of data does the VPN store?
- Is the data stored aggregated and anonymized?
- How long is this data stored for?
It’s best to avoid a VPN that has an excessively short privacy policy or ambiguous terms that don’t address these three things.
As an example, we’ll go through NordVPN’s website and compare it to the privacy policy. NordVPN markets itself as a “zero-log VPN service” on its website.
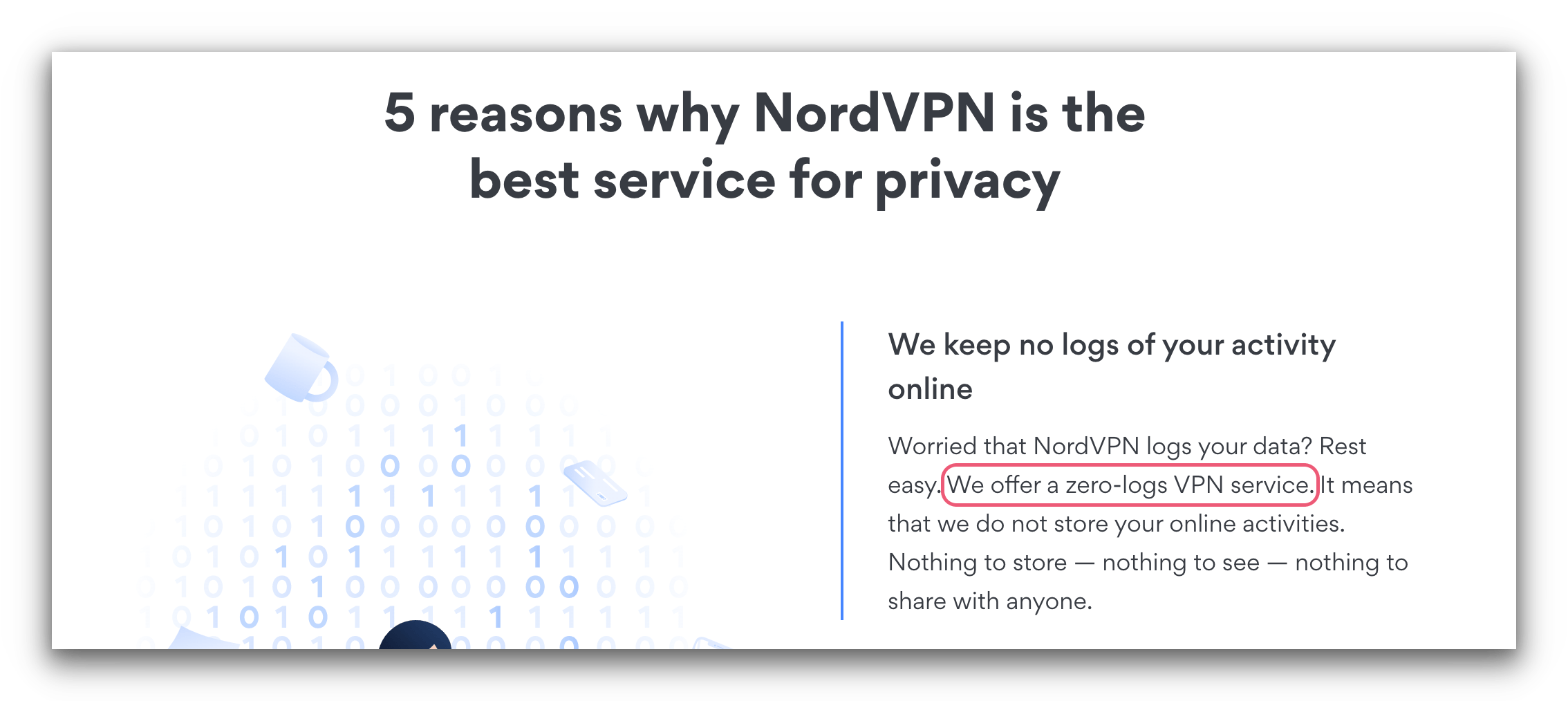
NordVPN’s website states that it’s a zero-logs VPN service.
But in reading NordVPN’s privacy policy, we’ve found it does store some sensitive data — as most VPNs will do. Importantly, it’s specified that NordVPN saves your username and a timestamp of the last session status.
This would be worrying if it were stored for a long time. However, NordVPN’s privacy policy clarifies that this data is promptly deleted within 15 minutes of your session ending.
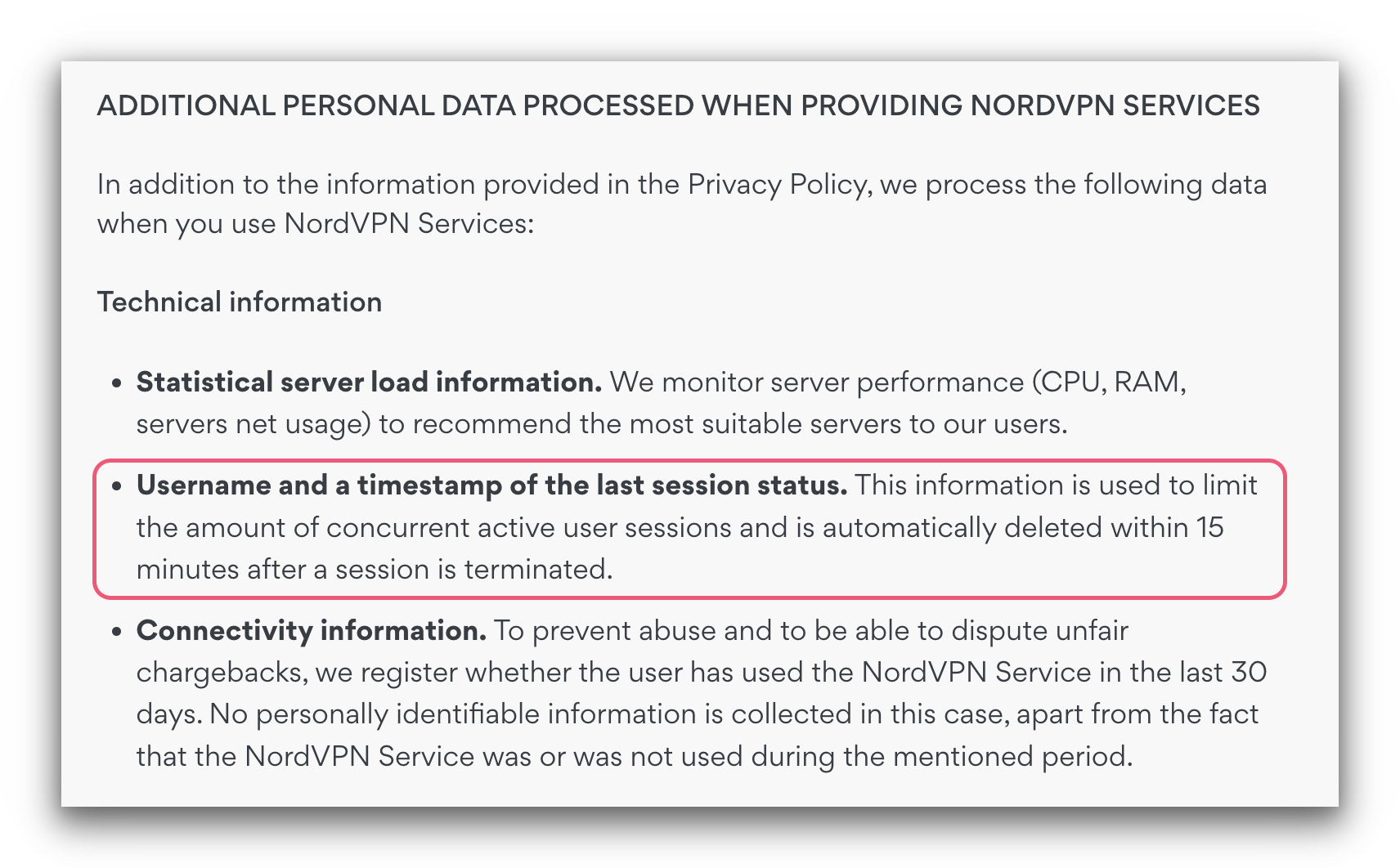
NordVPN’s privacy policy classifies this data as needed to provide its VPN service.
If you’re an average VPN user in a country with minimal internet restrictions, you should have no worries about this information being almost immediately deleted. The chance of it being leaked is low.
However, it does show the fine line between what VPNs claim to be no-logs and what they actually do log. In this case, NordVPN defines itself as no-logs because even though it does collect some data, it is deleted after a session is terminated.
Types of VPN Logs
VPN logs are records that VPN providers keep about who is using the service and how the service is used.
For example, a timestamp of when you connected to a server, your original IP address, your new IP address, and the URLs you visit, can give someone a full picture of what you’re doing online.
Since a VPN can have access to everything you do online, the less data it saves the better it is for your privacy. Ideally, as much data as possible will be deleted immediately to maintain as much anonymity as possible.
There are three different types of VPN logs:
- Activity or usage logs: browsing history, DNS requests, URLs visited, your Internet Service Provider (ISP), and usage metadata. This is the worst kind of data a VPN can store because it can be easily used to track a users’ online activity.
- Connection logs: individual bandwidth used, date and time you connected to a server, your original IP, and assigned IP address. This can be used in conjunction with activity logs to completely identify you and your browsing history or online activity.
- Aggregated logs can include any of the data points above as long as the data is completely anonymized. This means the information cannot be traced back to an individual user. For example, a single VPN server’s bandwidth usage (not of an individual user) and server load data are the most common types of aggregated logs. This is because a VPN will want to keep these numbers low to allow faster speeds on each server.
We recommend VPNs that only keep a minimal amount of logs. Some logging is acceptable, for example if it’s aggregated. But other types are completely unacceptable, like if a VPN saves your originating IP address and URLs visited for a long period of time.
Independent No-Logs Audits
The problem with no-logs VPN policies is that they are virtually impossible to prove from the outside. That’s why some VPNs hire external auditors to pick apart their no-logging policies and server infrastructure.
In theory, a third-party checking whether a server keeps logs will prevent bias and manipulation of audit results. But VPNs can manipulate results in an audit by only showing a specific server that’s been wiped clean while the rest are full of stored data.

Limitations of an audit outlined in IVPN’s No-Log 2019 Audit.
There’s also no guarantee that a server free of sensitive information over the two-week audit period will not start collecting data after the audit is concluded.
Even if a VPN carries out an extensive third-party audit, which provides major vulnerabilities to fix, the VPN can refuse to release it to the public if the results are negative.
In short, an external audit shows a VPN’s strong commitment to transparency and a private logging policy. But it doesn’t guarantee that an entire server network is completely free of sensitive information.
The best way to prove that is to have servers seized by law enforcement and raided for data. If no data is found on the randomly-seized servers, at a time when the VPN was unprepared for an investigation, then you can be sure that VPN’s servers are not storing data.
Diskless VPN Servers
When you connect to a typical VPN server, any data you transmit is stored inside the server on physical hard drives until it’s manually erased.
If the servers are seized by law enforcement or hacked, and the data hadn’t been erased, they could have access to any data kept inside.
To prevent this vulnerability, some VPNs use RAM-only or diskless server networks that erase data automatically on a regular basis or when a server is being seized.
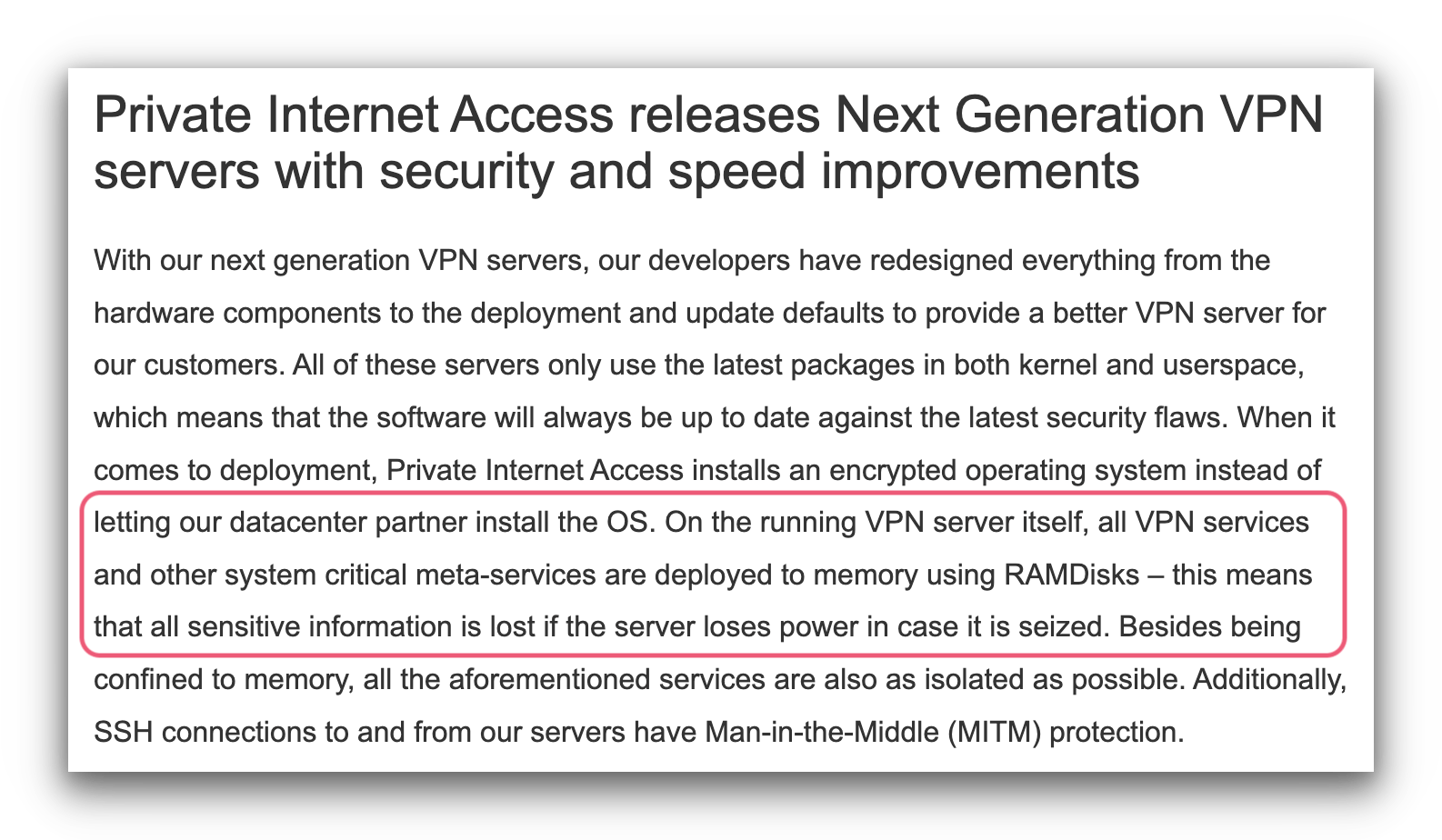
PIA implemented RAMDisk servers in June 2020.
RAM (or Random Access Memory) is a type of short-term computer memory that needs a constant source of electricity to keep the information. If the server was shut down or rebooted, it instantly deletes all the information stored inside.
A diskless network is much more private than a hard drive server network. However, they’re very rare in VPNs. Only a select few have the resources to implement this advanced server infrastructure.
Customer Service Providers & Payment Processors
Beyond the VPN service collecting data from its servers, there’s also third-party customer service providers (such as Zendesk) and payment companies (e.g. Stripe or PayPal) that a VPN might use.
Live chat customer support services in particular might log your IP address, email address, and device information during your conversation. This will likely be addressed in a VPN’s privacy policy if it’s a high-quality service — but isn’t always easy to find.
Some VPNs, such as Mullvad and IVPN, offer PGP keys to encrypt your email communications with customer service.
A payment company that handles online subscription payments might also have access to your full name, address, and other billing information. This isn’t necessarily bad, as many financial institutions that process these transactions are regulated by national financial authorities.
It’s also necessary for these companies to take this information in case you want to request a refund at the end of a money-back guarantee period.
Follow these steps to stay anonymous with VPN third parties:
- Register with a fake name and throwaway email address.
- Use an anonymous payment method, such as a gift card, virtual credit card, cryptocurrencies, or cash.
- Only contact customer service using a PGP key or throwaway email if you have any questions.
Why VPN Services Collect Logs
There are four main reasons why a VPN will collect logs. A majority of these are negative, but a VPN might also have a reasonable explanation for collecting data — like for issuing refunds or customer support.
1. Maintaining the VPN Service
A VPN might collect anonymous aggregated data or server load data in order to prevent product abuse and maintain fast speeds.
A VPN might also collect information to create an account or collect a subscription payment if you don’t use an anonymous payment method.
Lastly, most VPNs collect some sort of device information data to limit the amount of device per subscription. In these cases, collecting data in a way that means it can’t be traced back to a single user can be acceptable.
2. Government Intervention Might Force a VPN to Store Logs
In 2013, an encrypted email service, Lavabit, shut down its service to avoid having to “be complicit with crimes against the American people.” Alongside Lavabit, Silent Mail shutdown its service before it could receive any warrants or subpoenas from the US government.
In 2018, the Australian government passed an anti-encryption law, enabling it to silently perform mass-surveillance on its citizens. Additionally, any tools companies have to develop to allow the government access to user data could be a gold mine for sophisticated hackers.
Recently in 2022, India attempted to instate a new data privacy law that would force VPN providers to log user data for up to five years. Following backlash from VPN providers, in which ExpressVPN and Surfshark removed its Indian servers, the data law has been postponed indefinitely.
3. Selling Data to Advertisers
Some free VPNs will collect user data and sell it to advertisers instead of charging a subscription fee. This is extremely dishonest and unethical, especially if the VPN claims to be a zero-log VPN or privacy-first service.
That’s why it’s so important to use free VPNs that have been verified as safe.
However, it goes beyond just collecting a user’s browsing activity and IP address when connected to a VPN. Only three out of the top 20 free VPNs on iOS we tested respected a users’ decision to block advertisers from tracking user activity outside of the VPN app.
4. Poor Technical Infrastructure
A VPN with a poor technical infrastructure is vulnerable to attacks and can unknowingly leak your data.
As an example, in June 2021, Ukrainian authorities seized two of Windscribe’s OpenVPN servers as part of an ongoing investigation. It turned out that the servers were running an outdated configuration, with unencrypted OpenVPN server configuration and key.
Which VPNs Keep Logs? Full Test Results
To help shed light on this murky aspect of the VPN industry, we fact-checked the logging policies of 70 of the most popular VPN services on the market.
Our research revealed that the majority of VPNs record some form of user data:
- 39% log connection timestamps
- 26% store original IP address
- 10% record browsing activity data
- 6% log server IP address
The following table lists all 69 VPNs we’ve analyzed and the specific types of data they log. If you’re searching for a specific VPN, use Ctrl+F to find the provider you’re looking for.
Aggregated – Aggregated data has been collected in a group and shows trends in total, never on an individual basis. For example, some VPNs collect aggregated server bandwidth data to make sure servers aren’t overloaded.
Anonymized – Anonymized or de-identified data is encrypted to make sure any third-parties wouldn’t be able to use the data.
Vague – This means a VPN provider hasn’t specified in its Privacy Policy whether this datapoint is collected.




