There are a number of techniques that may be used to censor the internet. Each type of internet censorship requires specific technology and has its own potential limitations.
IP Blocking
Every web server has an IP address. IP blocking is a technique where censors generate a blocklist of known IP addresses and reset any connections attempting to connect to them. IP blocking can be used to block websites from entire countries or regions.
This is a relatively rudimentary type of censorship and it doesn’t require particularly sophisticated technology. However, it can cause overblocking, as several sites may share an IP address.
To get around IP blocking, a web proxy or a VPN can be used, if these services are not also blocked.
DNS Tampering
The domain name system (DNS) is used to convert a website address into the IP address of the server where it’s hosted. It is one of the first steps that happens when trying to access a website.
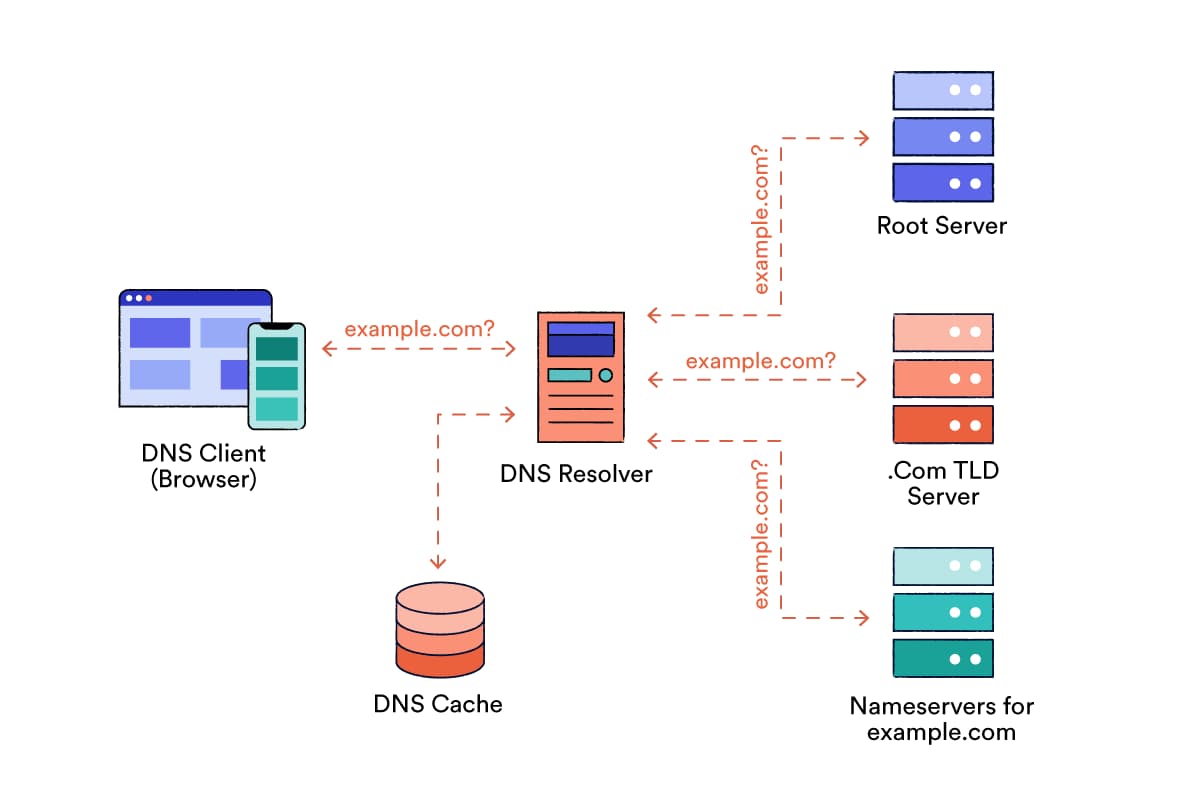
Your DNS resolver finds out the IP address for a website, so your device can connect to its server.
State agencies and ISPs can block access to websites or divert people to an alternative website by interfering with these DNS servers.
Some networks in China use a technique called “DNS mangling”, which returns a false response if someone tries to access a blocked website. This can also be referred to as “DNS lying.”
There is also “DNS cache poisoning”, which interferes with the response sent by a legitimate DNS server.
Although HTTPS encrypts much of your connection requests, DNS is largely unencrypted. This allows censors to view what website you’re trying to access and block the connection.
DNS tampering attacks like these can be circumvented. It’s possible to use an alternative public DNS server that is unaffected by government or ISP censorship, or set up a Smart DNS connection.
You can use free tools to check which DNS server your device is using, and change it if necessary.
Deep Packet Inspection (DPI)
Data travels across the internet in small sections called packets. Deep packet inspection (DPI) is a technique where the contents of these packets are studied as they travel across the internet.
When content is unencrypted, it’s possible to monitor all the traffic in transit. This allows censors to easily monitor and interfere with peoples’ connections.
If content is encrypted, DPI can still see the metadata, which reveals the type of traffic, the IP address, the amount of data transferred, and the date and time of that transfer. That can sometimes be enough to identify banned activity and block the connection.
DPI can be used to block VPN traffic, for example, unless VPN obfuscation is used to disguise it.
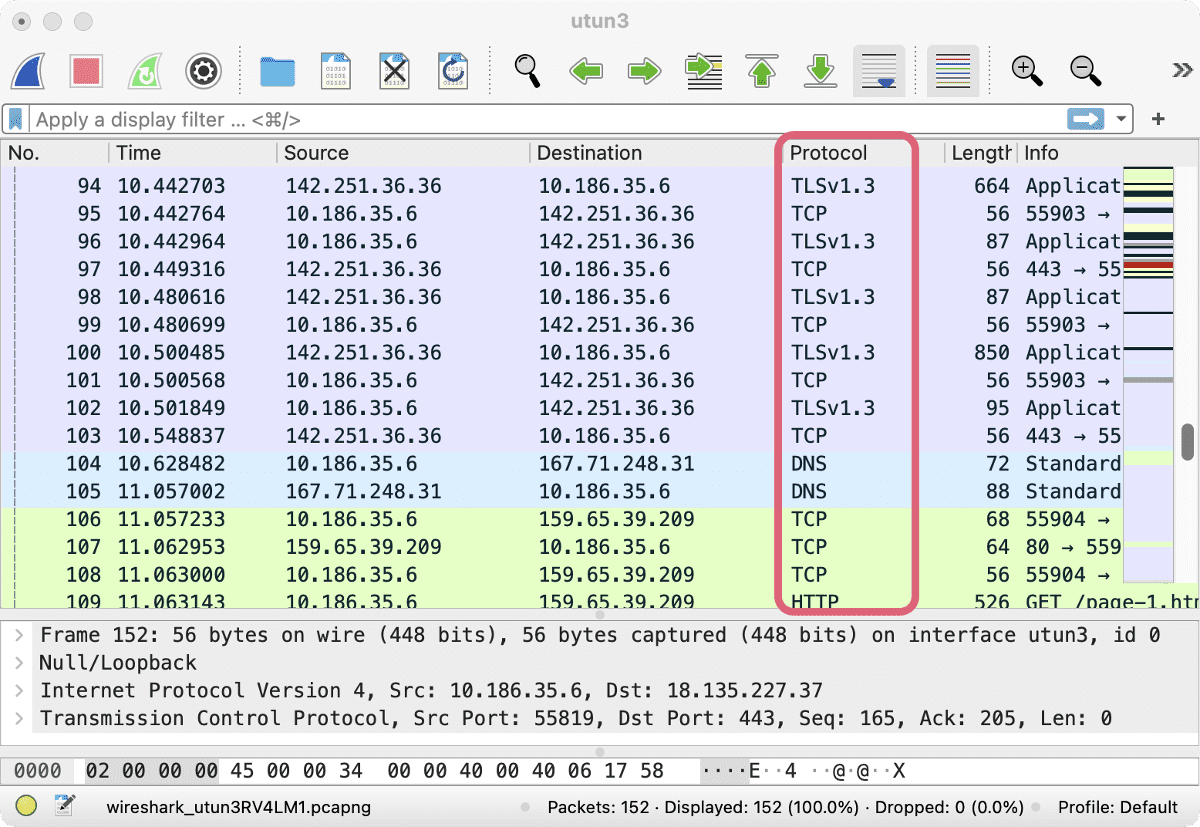
With Obfsproxy (a type of obfuscation) enabled, packet-sniffing tools like Wireshark are unable to detect an OpenVPN connection.
To help protect yourself against DPI, you can use a VPN, or try adjusting your network settings (the TCP/IP stack’s MTU/MSS) to reduce the amount of text contained in each packet.
EXPERT TIP: In China, authorities have the power to compromise site certificates, so a connection that appears to be encrypted may not be, after all.
URL Filtering
For censors, the problem with techniques such as DNS tampering and IP blocking is that you need to know which IP addresses or domains you want to block. There are too many to draw up a comprehensive list, and new sites are launching all the time.
URL filtering works by checking website addresses for banned keywords. If they are found, the connection is reset.
Censorship techniques based on keywords are particularly prone to overblocking. They may not be able to differentiate between pornography and sex education content, or between sites that promote alcohol abuse and sites that help people with recovery.
The “Scunthorpe problem” is so called because stories about the UK town have sometimes been blocked because the town name contains an offensive word.
Using a HTTPS connection, the censors can see the web domains you visit but not the individual pages you view. Censors have the option to block the entire domain or nothing on it, in that case. In China, entire blogging domains such as WordPress are blocked.
Search Engine Censorship
An alternative approach is to prevent search engines from including web sites in their search results in the first place.
Governments can exert pressure on search engines to remove results they don’t want people to see. For some years, Google worked with the Chinese government, providing a Chinese search engine with some results censored at the government’s request. Google withdrew from China in 2010 and its international search engine is now blocked there.
In Europe, Google blocks illegal content to comply with relevant domestic and international laws. It also allows users to request their information be removed from the search engine following a 2014 ruling by the Court of Justice of the European Union (CJEU). This is often referred to as the right to be forgotten.
Internet Throttling
Throttling is a technique where an internet connection is slowed down. If a connection is slowed enough, it can make the user’s device time out and drop the connection entirely. Internet throttling is sometimes called traffic shaping.
Governments in India, Venezuela and Jordan have all throttled internet speeds during periods of political upheaval. At times, they have targeted specific websites, while at others they have throttled all internet traffic in a particular region.
It has been often used in the past by ISPs in the US and Europe to slow down users who are torrenting, so they do not consume too much network bandwidth.
ISPs in the US and Europe often throttle bandwidth-intensive traffic like streaming or torrenting.
Distributed Denial of Service (DDOS) attacks
A distributed denial of service (DDOS) attack uses lots of devices to flood an internet resource with too much traffic, making it impossible for legitimate visitors to access the server. Often, the devices used for an attack have been compromised and their owners don’t know they’re being exploited.
DDOS attacks were launched by Russia against Ukrainian banks and government sites before the 2022 invasion, and are used in the Philippines against opposition politicians and independent media.
It’s cheap and easy to launch a DDOS attack today, with a 24-hour attack costing only a few hundred dollars.
As a web user, there’s not much you can do if the site you want to access is forced offline. You may be able to look for mirror sites or other places that host the same information, or you might have to wait until access to the site is restored.
Port Number Blacklisting
By blocking certain ports, censors can block entire applications. For example, web access, email, instant messaging, or VPN traffic.
This approach is sometimes used in the workplace to stop unauthorized applications, such as torrenting.
On-Device Software
In some cases, software can be installed on a device to censor the content that can be viewed on it. Most commonly, this is used by parents to protect children and young adults from content that is harmful to them.
In some cases, governments can install software on devices to control the information accessible through them. In May 2009, the Chinese government ordered manufacturers to include censorship software on computers they sold. They later said this was only necessary for computers that would be used in public places like internet cafes.
In 2021, the Lithuanian government found censorship software on a phone made by Chinese company Xiaomi. It censored content and sent data to Chinese authorities.
Internet Blackouts
In extreme cases, countries can turn off the entire internet in a region. These internet blackouts force everyone offline and are often imposed during protests or elections.
In 2019, the government in Sudan restricted access to the internet across the entire country. Following a court case that found the restrictions were unlawful, access to the internet was restored — but only for the one person who challenged the restrictions in court.
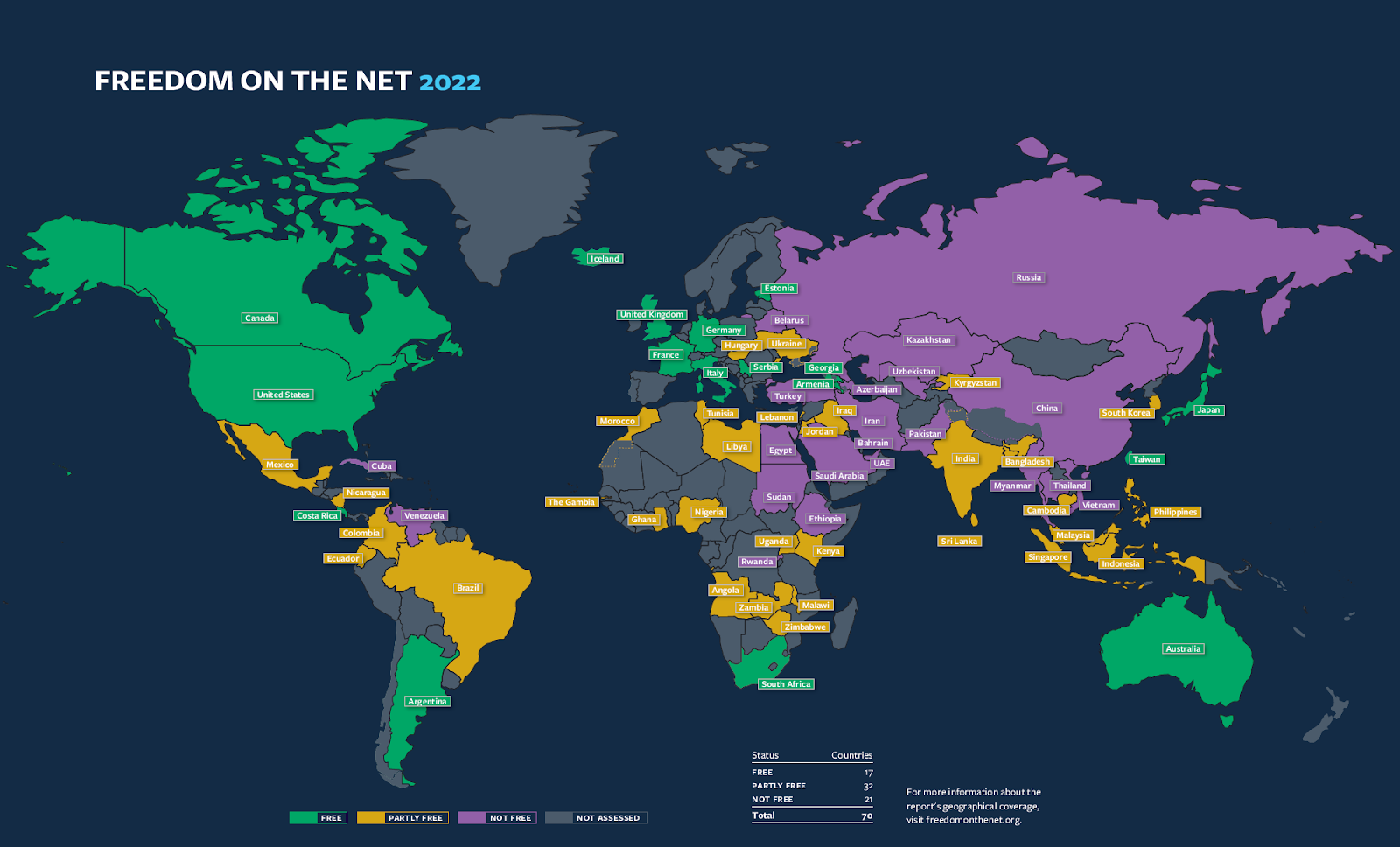
Since 2019, we have recorded more than 500 major government-mandated internet shutdowns. These include internet blackouts, as well as social media shutdowns and severe throttling.

Khartoum, Sudan. 30th June, 2019. Sudanese protest against the ruling Transitional Military Council (TMC) during a total internet blackout.
In total, these restrictions cost the global economy over $44 billion. In 2022, countries including Russia, Myanmar, Iran, India and Ethiopia all implemented internet shutdowns.
Self-Censorship
In many countries, oppressive regimes encourage people to censor themselves, out of fear of reprisals.
In China, for example, journalists, human rights lawyers, and activists have been detained for their online activities. In Iran, journalist Ruhollah Zam, who founded a site critical of the government, was executed. Vietnam has sentenced a number of independent online journalists to prison terms of between two and 10 years.
With penalties such as these, many people are reluctant to share their true thoughts online, and so are unable to form associations with others who hold the same views.