Top10VPN is editorially independent. We may earn commissions if you buy a VPN via our links.
WireGuard vs OpenVPN
Our Verdict
The more recent WireGuard protocol outperforms OpenVPN in speed by a significant margin and is more efficient, using 15% less data. It also handles network transitions more smoothly and maintains robust security. However, OpenVPN has a proven track record, is more privacy-friendly, and is supported by more VPNs.

OpenVPN was released in 2001 and is traditionally seen as the industry’s gold standard. But the new WireGuard VPN protocol has burst onto the scene since its release in 2015, and is now threatening to take that crown away from OpenVPN.
In this in-depth guide, we compare OpenVPN and WireGuard to see which VPN protocol you should use.
Our extensive lab tests reveal which of the protocols is best in seven key areas, including security, speed, privacy, ease of use, and more.
We’ll also reveal how these protocols came into being, giving you background information on who’s behind them, and explain the differences in how they work.
Why Trust Us?
We’re fully independent and have been reviewing VPNs since 2016. Our advice is based on our own testing results and is unaffected by financial incentives. Learn who we are and how we test VPNs.
| VPNs Tested | 62 |
| Total Hours of Testing | 30,000+ |
| Combined Years of Experience | 50+ |
Summary Table: WireGuard vs OpenVPN
Here’s a quick summary of how OpenVPN and WireGuard compare in each key category:
| Category | Winner |
|---|---|
| Speed | WireGuard
WireGuard is twice as fast as OpenVPN, if implemented correctly. |
| Security & Encryption | Tie
Neither protocol has any known security vulnerabilities. |
| Privacy & Logging | OpenVPN
OpenVPN can easily be configured to be logless, whereas VPNs need to include mitigations to ensure user privacy when using WireGuard. |
| Data Usage | WireGuard
OpenVPN adds a data overhead of up to 20%, whereas WireGuard uses just 4% more data (compared with not using a VPN). |
| Mobility | WireGuard
WireGuard offers a more reliable connection for mobile users than OpenVPN because it handles network changes better. |
| Bypassing Censorship | OpenVPN
OpenVPN is better at bypassing censors (e.g. the Great Firewall of China) because it can use TCP port 443. |
| VPN & Device Compatibility | OpenVPN
OpenVPN is currently supported by many more VPNs, across many more devices, than WireGuard. |
Speed
SUMMARY: WireGuard is a much faster protocol than OpenVPN. If you’re doing anything speed-sensitive, such as gaming or streaming, we recommend using WireGuard.
Winner: WireGuard
We connected to NordVPN servers around the world using either the OpenVPN or WireGuard, and recorded our connection speeds:
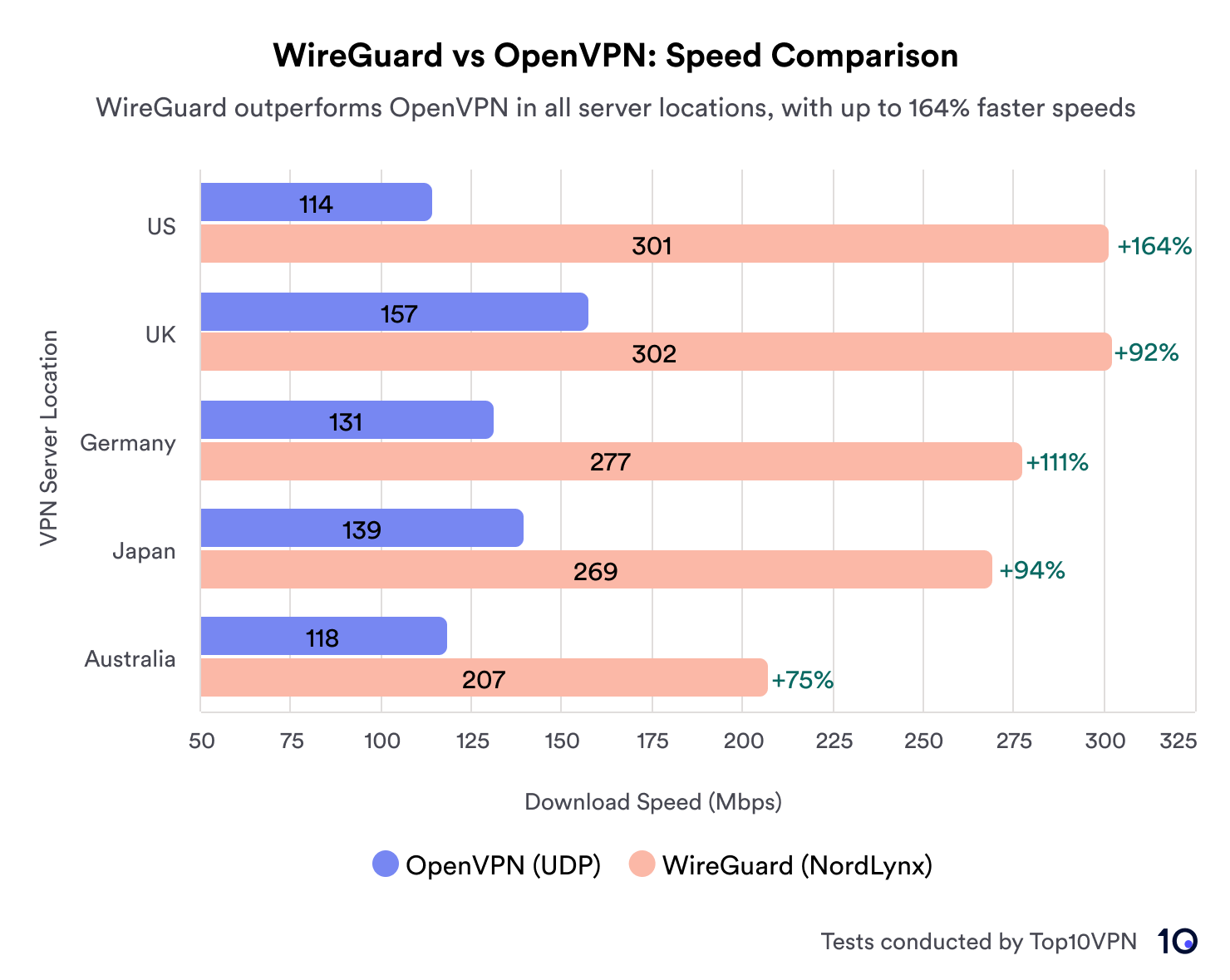
Our results found WireGuard was consistently over 75% quicker than OpenVPN, no matter where in the world we were connecting to, and on different devices.
On shorter-distance connections, the difference was even more pronounced, with WireGuard running at almost triple the speed of OpenVPN.
Our test results also match other tests done by NordVPN and WireGuard.
WireGuard also establishes a connection much quicker than OpenVPN. This is important because if the connection is lost or the VPN tunnel breaks for some reason, you want your VPN to reconnect fast.

An Ars Technica study found that an OpenVPN connection can take as long as 8 seconds to initiate, whereas WireGuard connections take around 100 milliseconds.
Overall, OpenVPN is significantly slower than WireGuard on our high speed internet connection. However, if you’re using a VPN with a 100Mbps connection or less, your speed loss won’t be so noticeable.
Encryption & Security
SUMMARY: WireGuard and OpenVPN are both very secure VPN protocols with strong encryption. Which is better for encryption and security mostly comes down to personal preference.
If you’re wary of newer technologies or like to have more control over your security settings, then OpenVPN is the better option for you. If you like the idea of an efficient, streamlined codebase, then go for WireGuard.
Winner: No clear winner. It’s a tie.
| OpenVPN | WireGuard | |
|---|---|---|
| Encryption Ciphers & Authentication Protocols | AES, Blowfish, Camellia, ChaCha20, Poly1305 & more | ChaCha20, Poly1035 |
| Perfect Forward Secrecy | Supported | Supported |
| Known Vulnerabilities | None | None |
OpenVPN lets you use a wide range of encryption ciphers and authentication algorithms, while WireGuard just has a fixed set for each release.
This means that, if a security vulnerability is found in an algorithm, OpenVPN can be quickly configured to use something else. Whereas WireGuard would require a software update across all devices. This ensures there are no devices ever using insecure code.
There are currently no known security vulnerabilities in both WireGuard and OpenVPN.
OpenVPN uses the OpenSSL library for encryption, which was first released in 1998 and has been thoroughly tested over a long period of time. The library supports a wide range of encryption ciphers, including AES, Blowfish, and ChaCha20.
WireGuard, created in 2015, doesn’t offer a choice of encryption. Instead, it forces you to use ChaCha20 for encryption and Poly1305 for authentication.
As a result, WireGuard requires much less code than OpenVPN: roughly 4,000 lines of code compared to 70,000 (at least).
This smaller footprint makes WireGuard much easier for security researchers to audit and verify WireGuard’s code than OpenVPN’s. It also makes WireGuard’s possible attack surface much smaller than OpenVPN’s.
Furthermore, less code considerably reduces the possibility of bugs occurring in WireGuard.
Are New Encryption Algorithms Safe?
Security researchers prefer encryption technology that has been around for a while. This is because newer algorithms may sometimes feature vulnerabilities that just haven’t been identified yet. It’s therefore often safer to go with a more tried-and-tested option.
Using Wireshark, we verified Windscribe’s connections are encrypted.
In this case, OpenVPN is by far the most tried-and-tested option. It was released decades before WireGuard, and the AES cipher it uses is almost a decade older than the ChaCha20 and Poly1035 algorithms that WireGuard uses.
In practice, however, WireGuard’s relative immaturity doesn’t appear to be a huge security risk. There are three main reasons for this:
- WireGuard’s minimal codebase means it can be audited very quickly. This mitigates a lot of the concerns about the protocol’s lack of rigorous testing, because experts can audit it much faster than OpenVPN’s code.
- ChaCha20 is very secure. The ‘20’ in ‘ChaCha20’ means there are 20 rounds of encryption to protect the data. In 2008, ChaCha7 (with seven rounds) was broken, but ChaCha8 remains unbroken to this day. So you can be confident that ChaCha20 offers a high level of security.
- Endorsements from Linux and Google. Linus Torvalds, original creator of Linux, said: “Can I just once again state my love for [WireGuard]… Maybe the code isn’t perfect, but I’ve skimmed it, and compared to the horrors that are OpenVPN and IPSec, it’s a work of art.” WireGuard has since been included in the Linux kernel, which represents strong support for its security credentials. Google also switched to using ChaCha20 and Poly1305 for encrypting traffic on its Android devices in 2014.
Privacy & Logging
SUMMARY: Despite what other websites say, both OpenVPN and WireGuard record IP addresses by default. However, they can easily be configured to not store your IP address, using a variety of methods. Configuring OpenVPN to avoid logging is easier than WireGuard, though. If provided by a trustworthy no-logs VPN, both protocols are equally private.
Winner: OpenVPN
| Logging | Mitigations | |
|---|---|---|
| OpenVPN | Default verbosity setting stores real IP addresses | Minor server configuration, diskless servers |
| WireGuard | Default configuration stores IP addresses | Double NAT, diskless servers |
An essential feature of a safe VPN service is that it doesn’t store any personally-identifiable information about you. This also applies to the VPN protocol being used.
When configuring OpenVPN servers, a VPN service must choose the server’s logging level (also known as “file verbosity”). It starts from level zero, which records very little information, to level 9, which records a lot of sensitive information.
In our research, we found OpenVPN’s default configuration is set to level 3 verbosity, which logs real IP addresses and usernames.
However, it is extremely easy for VPNs to configure the server to lower the logging level to zero, and avoid recording real IP addresses. This can also be done by configuring the server to regularly wipe all information.
Bear in mind, though, without a third-party audit, it’s hard to tell whether this has been done.
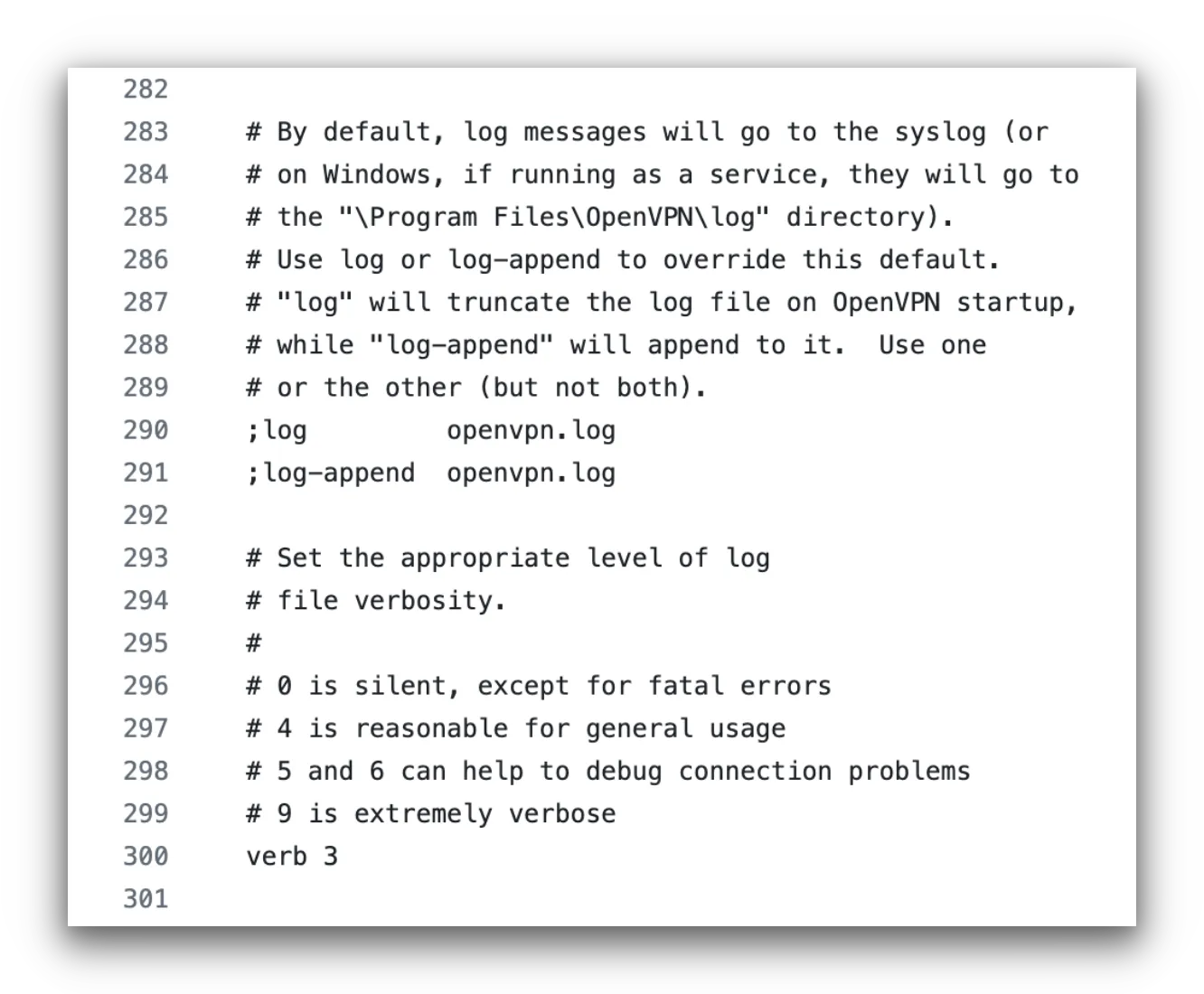
OpenVPN’s GitHub documentation shows “verb 3” logging is the default.
Similarly, WireGuard requires permitted IP addresses to be stored on the server until the server reboots.
This is concerning from a privacy standpoint, because if the server is compromised, the IP address could be used to link you to your activity and thereby remove the main benefit of using a VPN.
Be aware, then, that if you’re using the standard implementation of WireGuard, it’s likely your IP address is being logged for at least the duration of your session.
Thankfully, most commercial VPN services that support WireGuard have implemented workarounds to minimize these privacy risks. Some examples include:
- NordVPN: NordVPN has combined WireGuard with its proprietary Double Network Address Translation (NAT) technology to create NordLynx. Instead of storing your static IP address until the server reboots, NordLynx assigns a unique dynamic IP address to each VPN tunnel, such that each session has a different IP address that only lasts as long as the session.
- Mullvad: To maximize privacy when using WireGuard, Mullvad deletes your IP address from its servers after 10 minutes of inactivity. As an extra step, Mullvad also suggests you use its Multihop feature to route your traffic through two or more servers when using WireGuard.
- IVPN: IVPN deletes your IP address after three minutes of inactivity. It also randomly generates a new IP address every 24 hours, to avoid issues around using a static IP address.
These mitigations will be enough for most users. However, if you are in a strict censorship country or a country where officials may try to prosecute VPN users, it’s probably not a risk worth taking.
We’d also recommend checking with your VPN provider which mitigations they have in place for WireGuard users, if you’re concerned about your privacy.
Data Usage
SUMMARY: WireGuard uses much less data than OpenVPN. Choose WireGuard if your internet access has a data cap, or if you’re charged based on the amount of bandwidth you consume.
Winner: WireGuard
Using a VPN always increases the total amount of data you consume. That’s because the tunneling process sends additional information over the internet, which leads to an increase in data usage.
Data overhead can affect the speed of your VPN. If you’re on a cell phone contract, you might also spend more money or reach your data limit sooner.
The VPN protocol you use actually impacts how big the data overhead is. Our research found that WireGuard consumes far less data than OpenVPN:
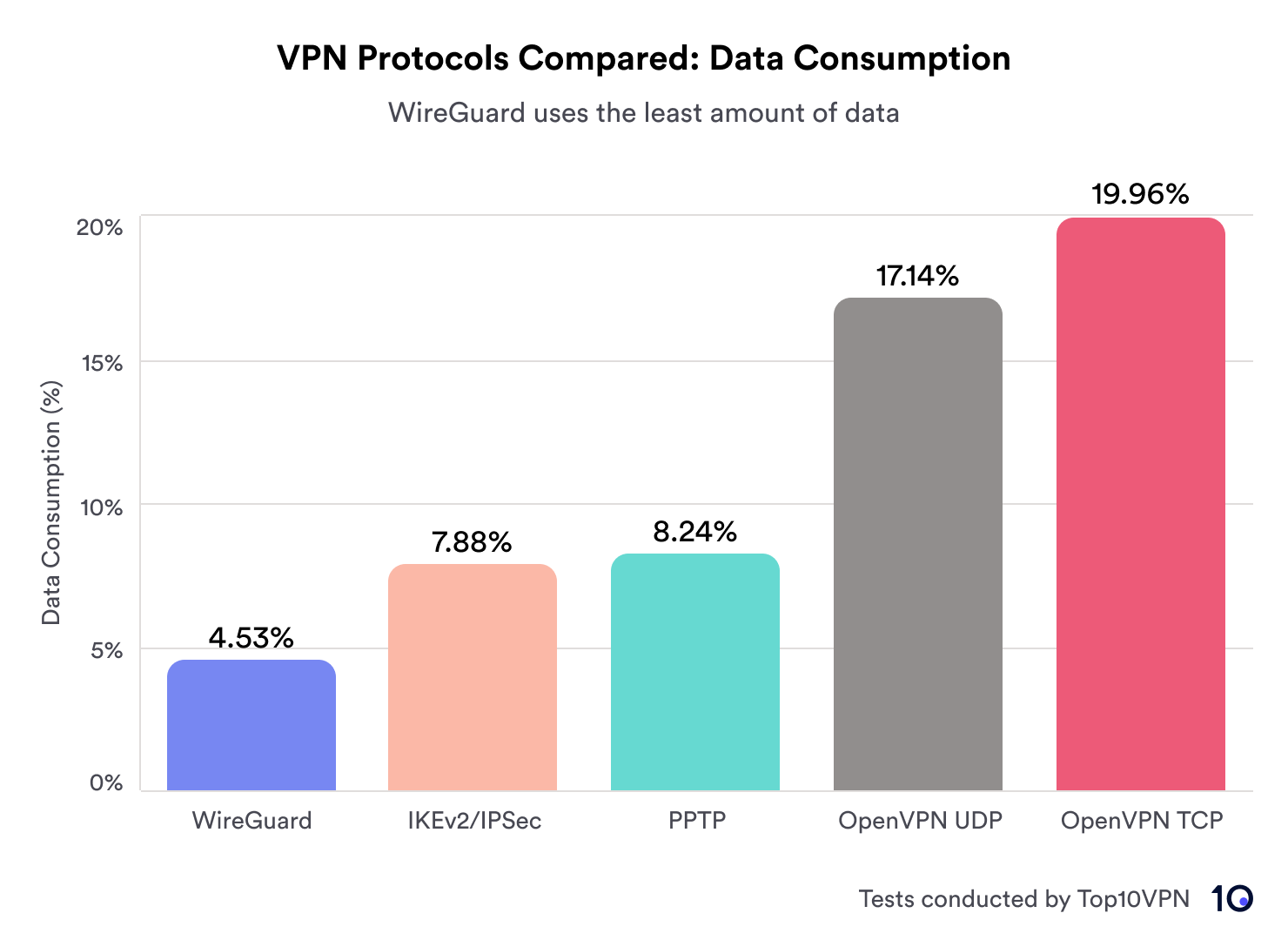
WireGuard adds just 4.53% to your data consumption, while OpenVPN UDP has a large overhead of 17.23%. When using OpenVPN TCP, this overhead is even greater, at 19.96%.
WireGuard actually has the smallest data overhead of any VPN protocol we’ve tested, including IKEv2 and PPTP. By contrast, OpenVPN has the largest.
To test each protocol’s data usage, we used the Linux WireGuard and OpenVPN applications and calculated how much additional data they were adding to our connection, compared to not using a VPN.
For each test, we copied a 209MB test file between two virtual servers. We conducted each test three times, and worked out the average data increase.
Mobility
SUMMARY: Unlike OpenVPN, WireGuard copes impressively well with regular network changes. It’s also faster and more privacy-friendly than IKEv2, which is the default protocol for most VPN apps on mobile.
Winner: WireGuard
Devices today frequently move between mobile and WiFi networks. A good VPN protocol needs to be able to make that switch efficiently and effectively.
WireGuard is far better than OpenVPN for mobility. It handles network changes seamlessly, whereas OpenVPN has historically struggled when users regularly switch between networks.
Many VPN services have actually opted to use a different protocol, IKEv2, for mobile devices.

IKEv2 is a reasonably good VPN protocol, but it is closed source and some people have concerns that it may have been compromised by the NSA. Instead, WireGuard presents a new, open-source solution to the problem of which VPN protocol to use on mobile.
If you’re using a VPN while on the move, we strongly recommend using WireGuard rather than OpenVPN.
Bypassing Censorship
SUMMARY: OpenVPN is the better choice for bypassing censorship. It enables you to use port 443, which is very difficult for censorship systems to block. Use OpenVPN (TCP) if you’re trying to access the free, global internet from within countries like China, Iran, and the UAE.
Winner: OpenVPN
OpenVPN and WireGuard are both very reliable VPN protocols that deliver a stable internet connection under most circumstances.
However, only OpenVPN natively supports TCP, which is helpful for bypassing strict internet blocks. This is because TCP connections can use port 443, the same port regular HTTPS traffic uses.
It’s highly unlikely that censorship systems in countries like China, Russia, and Turkey would block port 443, because it would halt essential activities like online banking and shopping.
In short, OpenVPN is more effective at bypassing censorship than WireGuard, because WireGuard natively doesn’t support TCP.
Astrill VPN offers OpenWeb, OpenVPN, StealthVPN, and WireGuard protocols.
We usually recommend using UDP whenever possible because it’s usually faster, more efficient, and equally stable when used within a VPN tunnel. However, for bypassing firewalls and circumventing censorship, a TCP protocol is preferable.
This is reflected in the option that VPN services default to when you try to connect in China.
We found that, in almost every case, when a VPN provider offers both WireGuard and OpenVPN, the service will default to using the OpenVPN protocol when you try to connect from within China.
We also tested a few VPN services that we know work well in China to see whether OpenVPN or WireGuard was better at bypassing the Great Firewall of China:
- Astrill VPN was able to beat the censorship using both OpenVPN and WireGuard.
- Private Internet Access (PIA) was only able to connect when using OpenVPN, and failed using WireGuard.
VPN & Device Compatibility
SUMMARY: OpenVPN has been around for almost two decades and is natively supported within almost every VPN app. WireGuard is currently being integrated into more and more VPNs, but your chosen VPN provider is still more likely to support OpenVPN. This is especially the case if you’re using a VPN on your router.
Winner: OpenVPN
OpenVPN is natively supported by almost every commercial VPN service, whereas WireGuard is much less widely available.
WireGuard is catching up fast, though. Despite only being released in 2015, the protocol has already been implemented into many leading VPNs – often across both desktop and mobile apps.
Here’s an overview of which protocols are supported on 10 of the most popular VPNs:
| VPN Protocol | ExpressVPN | NordVPN | CyberGhost | IPVanish | Surfshark | PrivateVPN | PIA | Windscribe | Proton VPN | Astrill |
|---|---|---|---|---|---|---|---|---|---|---|
| OpenVPN | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| WireGuard | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ |
Traditionally, most VPNs use OpenVPN as their default protocol, particularly on desktop. However, we’re now seeing an increasing number of providers switch their allegiance to WireGuard.
For example, CyberGhost now uses WireGuard by default on Android and iOS, and NordVPN uses its NordLynx version of WireGuard as the default in most of its apps.
NOTE: To use a VPN on your router, you’ll likely still have to use OpenVPN. Only a few VPNs, like Mullvad and Proton VPN, offer WireGuard at the router-level.
What Are OpenVPN and WireGuard?
OpenVPN and WireGuard are two types of VPN protocol. A VPN protocol is technology used to create a secure tunnel between your device and a VPN server. In other words, a VPN protocol is a key element to how a VPN works.
You can use both OpenVPN and WireGuard independently to create your own VPN connection. However, they’re more commonly used as part of personal VPN services.
Here’s an overview of each protocol’s main features:
| OpenVPN | WireGuard | |
|---|---|---|
| Initial Release | 2001 | 2015 |
| Open Source | Yes | Yes |
| Code Length | 70,000+ Lines | ~4,000 Lines |
| Speed | Moderate | Very Fast |
| Data Usage | High | Very Low |
| Security & Encryption | Very Strong | Very Strong |
| Privacy | Needs Configuration | Needs Configuration |
| VPN & Device Compatibility | Widely Supported | Widely Supported |
OpenVPN

The original OpenVPN software was created in 2001 by James Yonan.
Yonan made OpenVPN to ensure his connection was private while travelling through Central Asia and using Asian and Russian internet connections.
Today, Yonan is the CTO of OpenVPN Inc. The company provides business-to-business services as well as running OpenVPN.
The company’s CEO and founder is Francis Dinha, who grew up in Iraq and shares Yonan’s concerns about staying private from state surveillance.
The OpenVPN software has now been downloaded more than 60 million times, and almost every VPN today employs the protocol.
OpenVPN is available under an open-source license, which means anyone can view its underlying code.
For over a decade, OpenVPN has been considered the pinnacle of VPN security. However, with the release of WireGuard, there is a new contender for that top spot.
WireGuard

WireGuard was created by Jason A. Donenfeld from Edge Security, and had its first release in 2015.
WireGuard is designed to improve upon existing VPN protocols by being simpler, faster, and easier to use.
Unlike OpenVPN, WireGuard is “cryptographically opinionated,” to use Donenfeld’s words. That means he’s selected one solution for each aspect of the VPN’s security.
As a result, WireGuard includes less choice than OpenVPN, but it’s also far less complex.
Like OpenVPN, WireGuard is also open source.
Despite only being released in September 2015, WireGuard has already been incorporated into a number of VPN services. NordVPN, for example, built its proprietary NordLynx protocol on top of it.


