I detected failures that ranged from a complete failure to encrypt internet traffic to the exposure in clear text of DNS requests.
Whatever the type of encryption failure, my test results suggest that these 11 VPNs each pose a very high potential risk to user privacy.
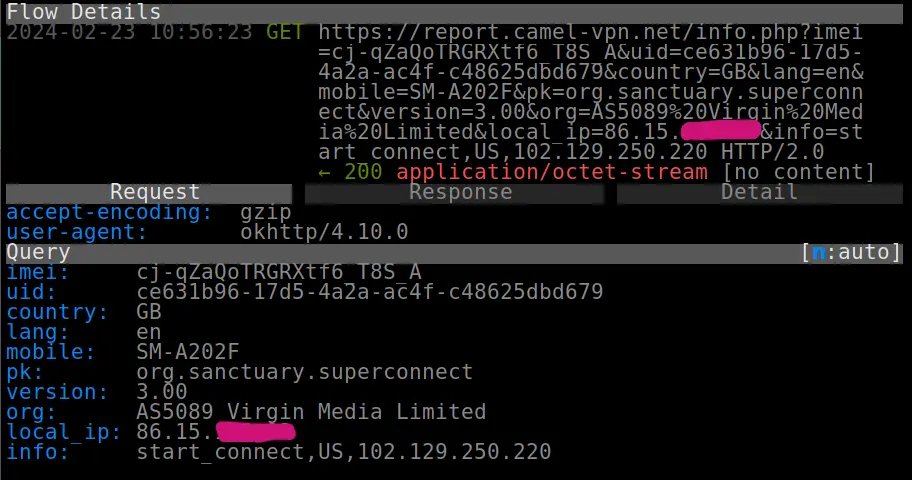
No encryption: VPN Satoshi was the only app to completely expose my browsing activity during my tests.
In the screenshot below taken from Wireshark you can see that not only is the name exposed of the test domain I visited but also the specific URL and the HTML contents of the page itself.
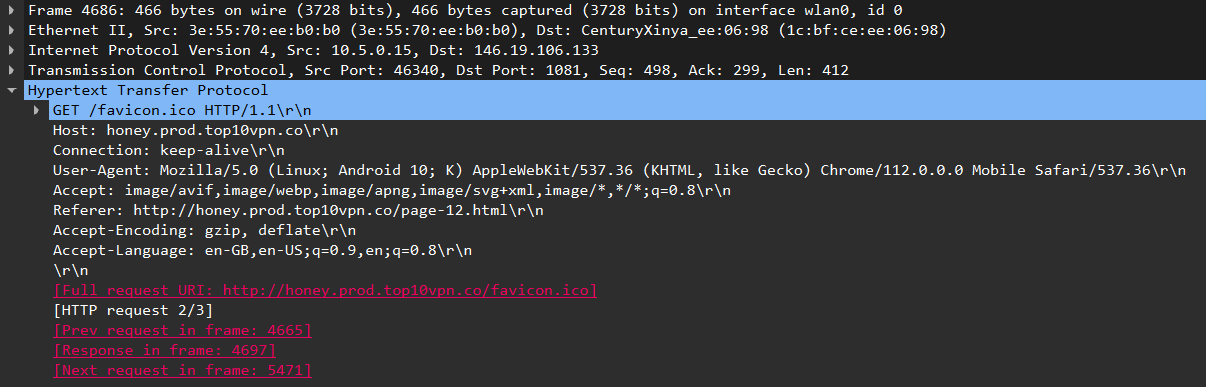
Screenshot of the contents of a HTTP packet captured from a session using VPN Satoshi while it was connected, showing unencrypted details of a web page I visited.
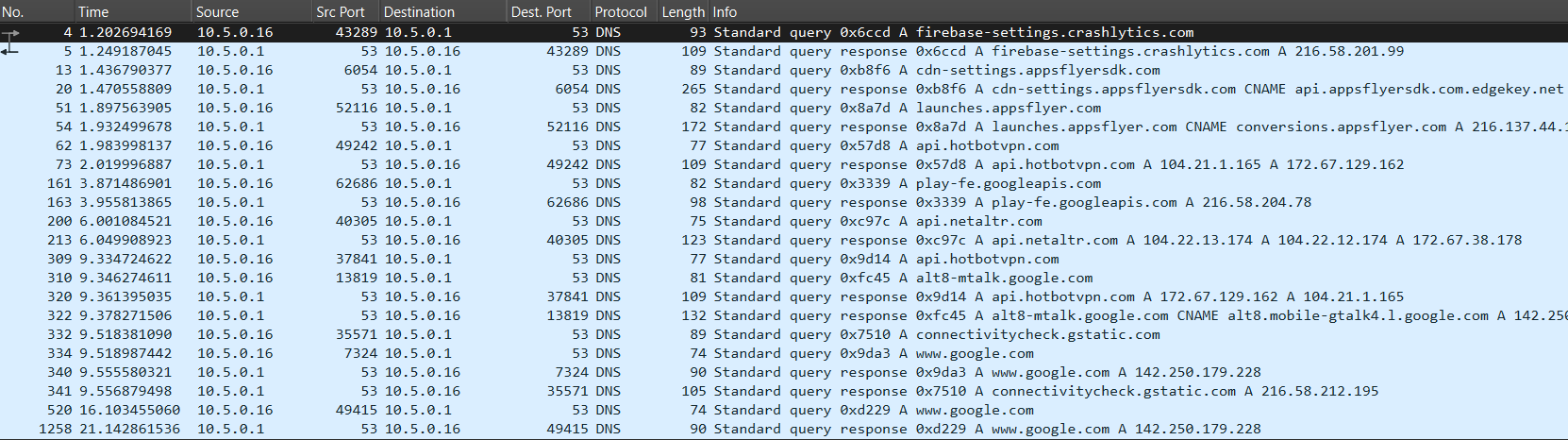
Browser DNS requests: The other 10 VPNs in the table leaked DNS requests relating to websites I visited during my tests.
As you can see in the Wireshark screenshot I’ve shared below, anyone monitoring my activity while I was using any of these VPNs, such as an ISP or network administrator, would be able to determine which domains I visited and when.
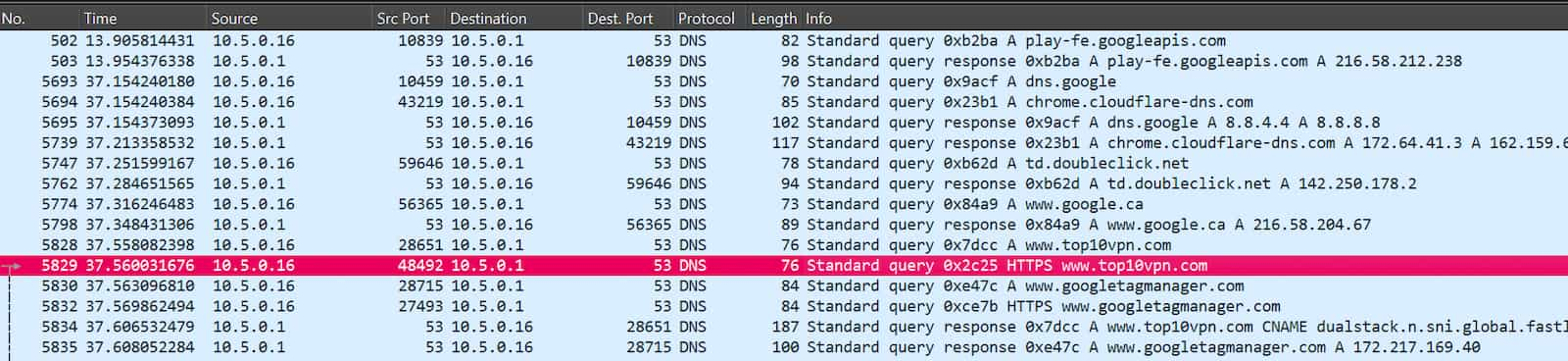
Screenshot of DNS requests from browsing activity leaking from the VPN tunnel created by VPN Private Android app.
AVG and Tenta, two private browsers with integrated VPNs, only exposed a subset of DNS requests related to tests performed by our leaks tool.
Despite running the leak tests via the apps’ “secure” browsers, as opposed to Chrome, DNS requests to iptools-6.top10vpn.com and dnstest6.top10vpn.com and were exposed. I didn’t find any other exposed DNS requests in my tests of these two apps.
Both apps employ the secure DNS over TLS (DoT) protocol and it’s possible this may be failing for IPv6, causing it to fallback to normal DNS, which is sent over a plaintext connection.
This is much less dangerous than the more wide-ranging encryption failures experienced by the other VPN apps in the table.
However given that this edge case has not been addressed, there’s a question mark about what other activity might be exposed in the course of normal usage.
For more findings around DNS and other leaks, jump straight to that section.
Weaker Encryption & Handshakes
The two most concerning VPNs in terms of encryption were HTTP Injector and Phone Guardian.
HTTP Injector functioned unreliably, sometimes changing my IP address and sometimes not.
In the screenshot I’ve shared below, you can see how the HTTP Injector app also repeatedly attempted to initiate the VPN tunnel using the outdated and insecure TLSv1 before switching to TLSv1.3.
TLSv1 dates back to 1999 and was formally deprecated in 2021.
Note that the SNI can be obfuscated in the app UI, with facebook.com as the default app setting.
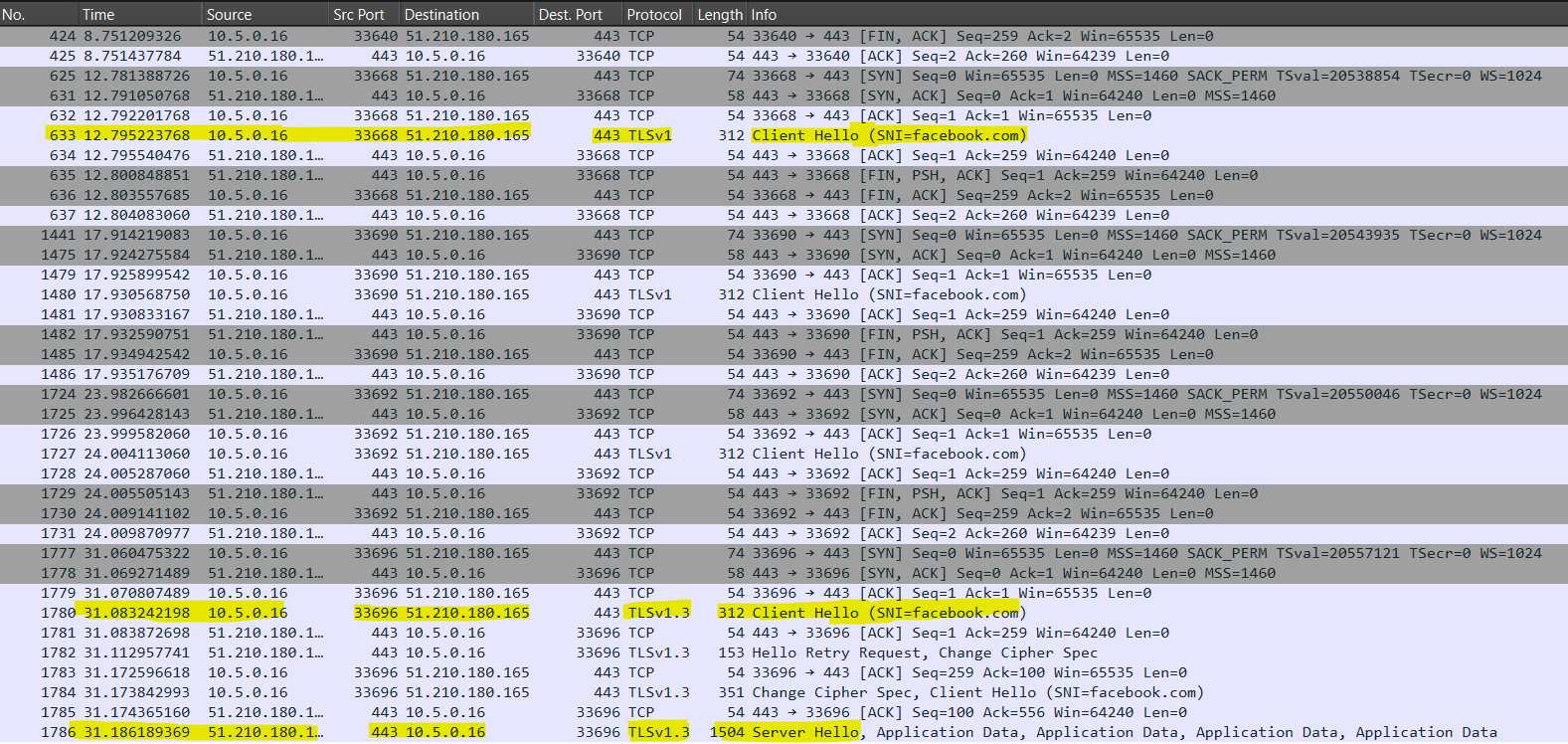
Screenshot of the attempted use of TLSv1 by HTTP Injector VPN Android app.
Phone Guardian advertises itself as a VPN but it doesn’t really behave like one.
It neither hid nor changed my IP address, nor did it encrypt the majority of my internet traffic.
Instead, Phone Guardian only encrypts HTTP sites when you connect to untrusted WiFi networks.
Unfortunately, this means the details of any HTTPS websites you visit remain exposed via DNS lookups and SNI in HTTPS handshakes.
While Phone Guardian works as intended, it’s very easy to be misled into believing you are being protected in the same way as a normal VPN.
More broadly, I found that at least 35 VPNs encrypted traffic using algorithms that, while neither insecure nor “broken”, could be considered sub-optimal as they were 128-bit rather than the stronger 256-bit encryption.
I found something similar with the implementation of PRF (Pseudo-Random Function) in the cipher suite of 11 VPNs. These VPNs used AES-128-CBC for PRF rather than the stronger HMAC-SHA2-256.
I also identified 16 VPNs that always used TLSv1.2 as the handshake protocol, plus another 2 VPNs that used it some of the time.
While use of TLSv1.2 remains acceptable, especially if it is manually configured to remove support for vulnerable cipher suites, this version of the protocol is nearing the end of its life and has been superseded by the faster and more secure TLSv1.3.
Given how free VPNs are often used to hide sensitive internet activity in high-censorship regions, it’s disappointing to see so many that fail to adopt the most secure forms of encryption.
Most problematic however were the four VPNs that I found using SSLv2 as the handshake protocol to establish a VPN tunnel.
This obsolete protocol is almost 30 years old and was quickly superseded by SSLv3 and since then by the various versions of TLS.
The four VPNs using this vulnerable protocol were:
- Thunder VPN
com.fast.free.unblock.thunder.vpn
- Tomato VPN
com.ironmeta.security.turbo.proxy.vpntomato.pro
- Urban VPN
com.urbanvpn.android
- VPN Ukraine
vpn.ukraine_tap2free
I identified two other VPN apps using SSLv2, albeit in a different and unusual manner.
After establishing a VPN tunnel using TLS, I observed the following apps make additional connections to VPN servers on different IPs to the tunnel endpoint using the obsolete protocol.
- “VPN – fast secure vpn proxy”
com.optimizer.booster.fast.speedy.phone.smooth
- VPN Monster
free.vpn.unblock.proxy.vpnmonster
I observed the apps sending and receiving hundreds of packets over these insecure connections.
Leaky VPNs
As well identifying leaks via Wireshark, I also used our own VPN leak tool to test for IP, DNS and WebRTC leaks.
Download the data sheet to see the full details of how each VPN app was affected.
Using our tool, I found that 15 VPNs leaked my IPv6 address, an example of which you can see in the screenshot below.
This includes 3 VPNs that leaked both the IPv4 and IPv6 addresses of my connection.
The three VPNs that leaked my IPv4 and IPv6 addresses were:
- Tomato VPN
com.ironmeta.security.turbo.proxy.vpntomato.pro
- Phone Guardian VPN
com.distimo.phoneguardian
- Ultimate VPN
com.open.hotspot.vpn.free
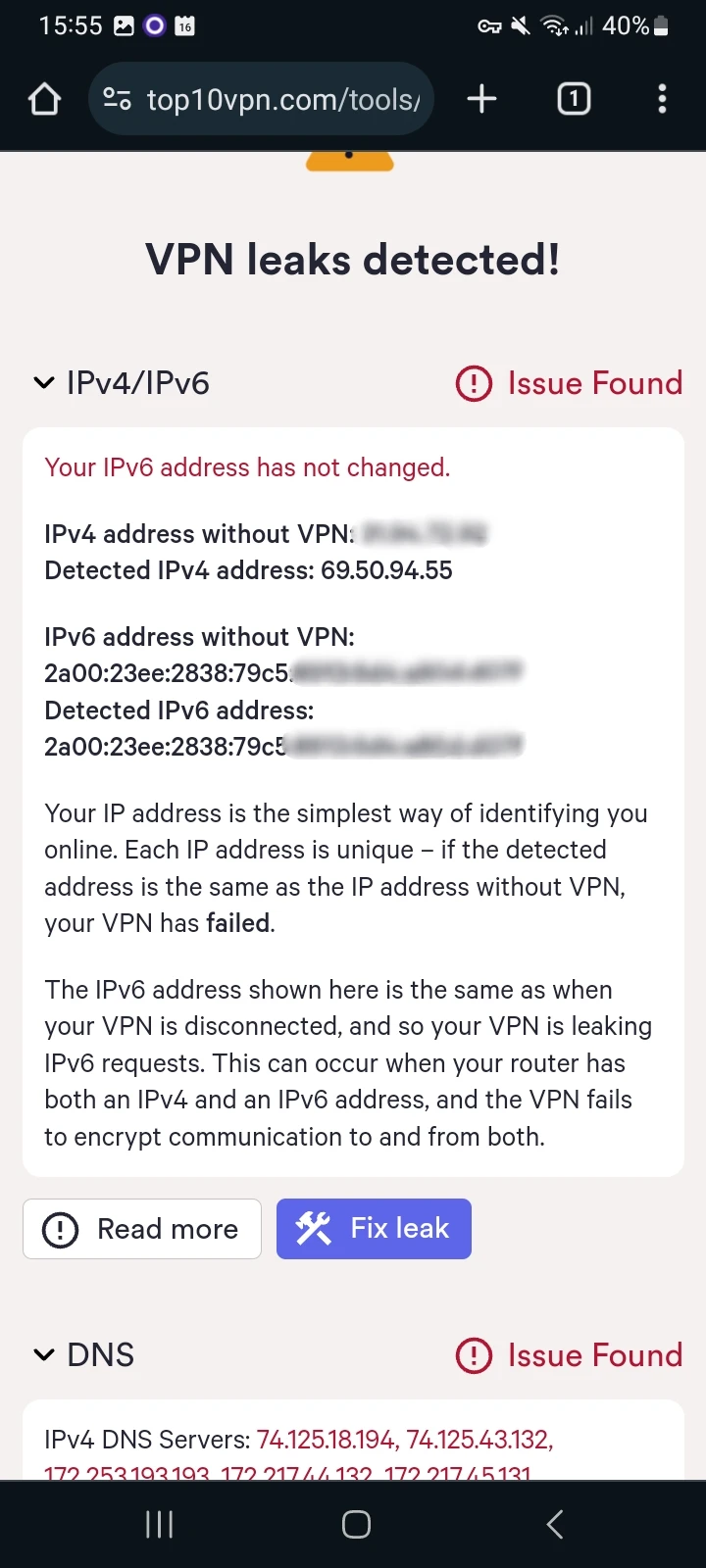
Screenshot of Top10VPN leak tool showing IPv6 leak in VPN Pro.
IPv6 leaks are just as dangerous as IPv4 leaks. Websites and applications will have access to your real location, and your ISP will know your internet history.
The five most popular VPNs that leaked my IPv6 address were:
- Turbo VPN
free.vpn.unblock.proxy.turbovpn
(335 million installs)
- WiFi Map
io.wifimap.wifimap
(116 million)
- VPN – Super Unlimited Proxy
com.free.vpn.super.hotspot.open
(93 million)
- VPN Proxy Master
free.vpn.unblock.proxy.vpn.master.pro
(84 million)
- Turbo VPN Lite
free.vpn.unblock.proxy.turbovpn.lite
(68 million)
I found that 83 VPNs leaked DNS requests from my test devices.
By that I mean any DNS requests made while using any of these 83 VPN apps are serviced by a third-party rather than by the VPN provider.
As a result, that third-party, whether it’s Google, Cloudflare or some random ISP, knows every site you visit, massively compromising your privacy in the process.
Almost half (40) of leaking VPNs used Google for to handle DNS request and 14 used Cloudflare.
While the majority of these DNS-leaking VPNs (72 apps) did not send DNS requests related to browsing activity outside of the VPN tunnel, many did fail to route DNS requests to their own servers and failed to send HTTP communication to ad trackers or analytics services through the tunnel.
The screenshot below shows examples of that type of DNS leak.
Note that 10.5.0.1 is the address of my default DNS server. If you use this method to check whether your VPN is leaking then expect to see the IP address of your ISP’s DNS servers or of your router.
Screenshot of DNS leaks captured from HotBot VPN session.
Some of the most downloaded VPNs that suffered DNS leaks were:
- Turbo VPN: 335 million installs
- SuperVPN: 250 million installs
- Secure VPN: 166 million installs
- Psiphon Pro: 141 million installs
- Kaspersky VPN: 117 million installs
I also captured packets from 79 VPNs that had domain names visible in their SNI (Server Name Indication) fields.
This exposed SNI information, which included domains for the VPN services I was using, their third-party trackers, and the websites I had visited, was evidence of traffic that should have gone through the VPN tunnel and not been visible in this way.
The leaking of these packets from the tunnel undermined my privacy while using these VPNs, exposing my activity to anyone monitoring my connection.
There were 5 VPNs where I observed this kind of leak but did not detect any other DNS, IP or WebRTC leak.
- Avira Phantom VPN: Fast VPN
com.avira.vpn
- Bitdefender VPN: Fast & Secure
com.bitdefender.vpn
- F-Secure FREEDOME VPN
com.fsecure.freedome.vpn.security.privacy.android
- hide.me VPN: The Privacy Guard
hideme.android.vpn
- Unblock Websites — VPN Proxy
com.master.unblockweb
VPN Tunnel Instability
I detected abnormally high numbers of TCP Reset (RST) packets in test sessions with 25 VPNs, averaging nearly 17 resets per session despite my test sessions typically only lasting for just over a minute.
While RST packets close sockets in normal TCP/IP communications, the high volume suggests network anomalies like congestion, unreliable connections, or misconfigurations, indicating potential instability and vulnerabilities.
Furthermore, I also found signs of tunnel instability through out-of-order TCP packets, TCP Window Full packets, and wrong sequence number ESP packets in 53 VPNs.
HTTP Data Exposure
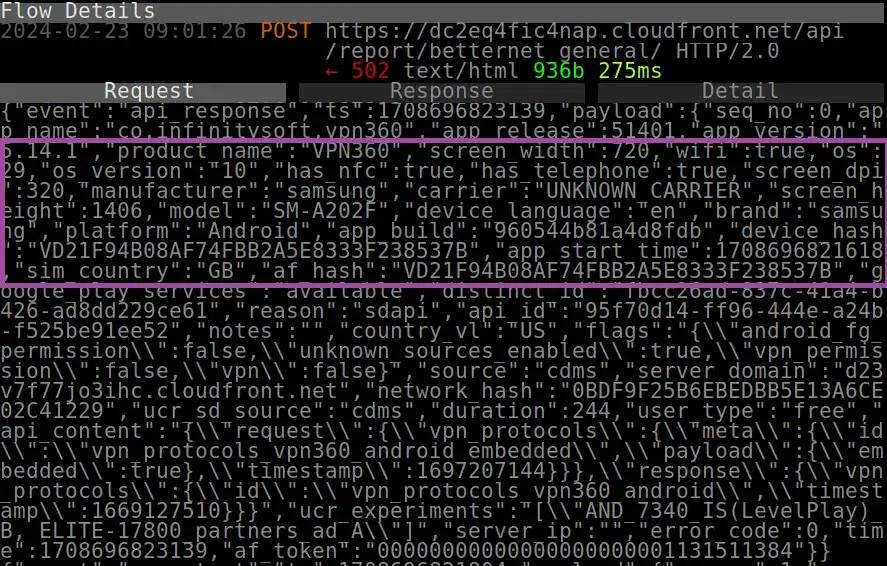
I discovered that several VPNs exposed sensitive information about me in responses to HTTP requests that were not encrypted.
Four VPNs received personally identifiable information (PII), including my real IP address, in unencrypted HTTP/JSON responses from ip-api.com which they used to show me my geolocation data.
Here’s a screenshot of one of these unencrypted responses.
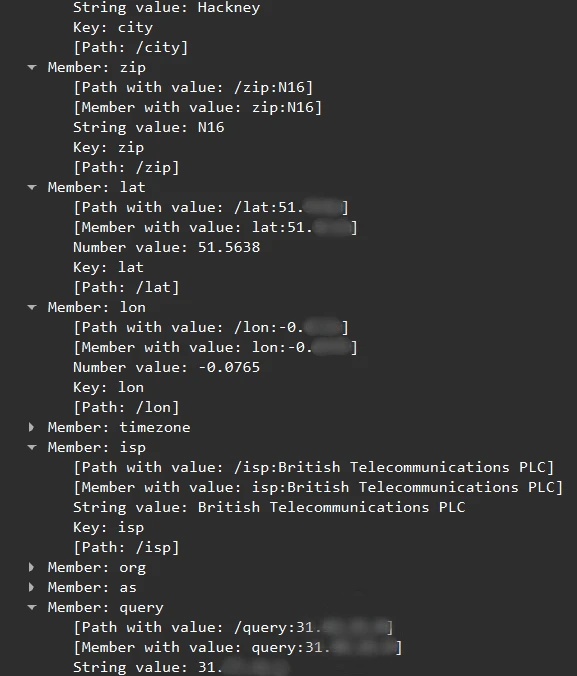
Screenshot unencrypted of HTTP/JSON response received by WiFi Map VPN containing PII, including my real IP address.
This practice is insecure and poses a privacy risk.
Given that only the free version of the ip-api service, which is not intended for commercial use, is not encrypted, it’s likely that the VPNs in question are exposing their users’ data for the sake of $14 a month.
The only alternative is that these VPNs have failed to use to the correct endpoint. We will never know whether this is a deliberate choice or simply incompetence.
The affected VPNs were:
- Turbo VPN Lite
free.vpn.unblock.proxy.turbovpn.lite
- Speedy Quark VPN
com.speedy.vpn
- VPN Proxy Master
com.freevpn.unblock.proxy
- WiFi Map
io.wifimap.wifimap
Another app, VPN Proxy Speed com.supervpn.vpn.free.proxy sent rather than received similar information to the following URL rufjskls.shop/report.php on the 104.21.12.129 IP address.
The content on rufjskls.shop as per this screenshot indicates that it’s operated by VPN provider.
Screenshot of content on domain that received requests from VPN Proxy Speed containing PII .
Four more VPNs (WiFi Map VPN, Turbo VPN Lite, TLS Tunnel, and “VPN – fast secure vpn proxy”) sent telemetry about my test device, such as make, model and OS, unencrypted over HTTP in User-Agent strings.
While the privacy risk is relatively low, unencrypted data transmission indicates lax security practices that could manifest more seriously elsewhere. This data could also compromise privacy if combined with other personal information.
Individual VPN Traffic Anomalies
I also found notable anomalies in individual VPNs’ traffic that raised privacy and security concerns.
Thunder VPN, which has over 91 million installs worldwide and was highlighted earlier in this report for using the obsolete SSLv2 protocol, had and issue around unusual numbers of what initially appeared to be DNS records.
I detected multiple packets containing an abnormally high number of questions, answer resource records (RRs), authority RRs, and additional RRs. The packets do not appear to be valid DNS queries, so port 53 is potentially being used for as a side data channel to the VPN Server.
Elsewhere, I discovered that Pawxy VPN (1.1 million installs) exchanged bt-dht (distributed bittorrent discovery protocol) packets with 178.71.31.82, a Russian IP address operated by Rostelecom, despite the app being connected to a French VPN server at the time.
This was a major red flag as I had no bittorrent client installed on my test device nor was any such functionality advertised on the Pawxy app.